The need for digital engagement with customers, partners, and employees has never been greater than it is today. Most organizations were already in varying stages of digital adoption when the pandemic hit. Suddenly, businesses of all sizes realized that their very survival depends on their ability to lean into digital transformation initiatives.
What Does Digital Transformation Mean
Digital transformation means different things across industries, markets, and even companies. And while much has been gained as a result of digital innovation, much still remains to be done. For example, McKinsey finds that nearly 8 in 10 enterprises are still in the early stages of digital adoption.
When it comes to software, Software-as-a-Service (SaaS) applications and services are certainly a critical linchpin. They offer organizations various advantages—rapid time to market to ease of use. But not every business requirement can be addressed by SaaS applications and services. In response, organizations develop their own applications—either by themselves or in concert with software development providers.
Legacy development approaches simply will not scale to meet the time-to-market requirements of this new push to develop and deploy applications. Software releases must occur multiple times per week or even day, and this has given rise to Agile and DevOps. Pre-pandemic, research shows Agile and DevOps adoption was a key focus area: 56% of CIOs said they planned to implement Agile or DevOps this year. Growth forecasts for the space are significant as well—Market Insights, as an example, predicts a compound annual growth rate (CAGR) of 20% for DevOps through 2026.
Agile and DevOps Expanding Post-pandemic
With the pandemic, though organizations are cutting back in many areas of their businesses, digital transformation is not one of them. A study from April by OpsRamp found that 73% of IT operations and DevOps leaders plan to accelerate or maintain digital transformation initiatives as a result of COVID-19. A recent survey completed by Contrast Security uncovered similar results, with nearly 60% of development, security, and operations leaders indicating they plan to increase Agile and DevOps spending and resources. A paltry 9% said they plan to decrease spending and resources in the area.
These digital initiatives pose substantial opportunities for most organizations. In a study conducted by EY, business leaders cite improving customer experience (61%), cost control and business efficiencies (53%), improved IT systems and processes (32%), and increased organizational agility (24%) as top factors behind digital innovation. Without Agile and DevOps, organizations simply cannot achieve the scale, speed, and cost efficiencies needed to develop and deploy the applications that power these business outcomes.
Agile and DevOps Dramatically Expand Application Attack Surface
Yet, the growth in applications, including application programming interfaces (APIs), creates significantly greater risk exposures. In the study Contrast Security recently completed, we found that the average enterprise has between 250 and 499 applications in development or production and over 1,500 APIs serving as the thread connecting them. The sheer number of applications and APIs to protect is daunting. Add that upwards of 90% of applications rely on open-source frameworks and libraries, including an average of 47 third-party libraries in one application, and securing the application attack surface becomes a huge undertaking, which extends from developers, to security, to operations.
Putting aside the challenges modern software development life cycles (SDLCs) pose when it comes to accelerated development cycles, the dramatically expanded attack surface poses significantly greater risk to organizations.
Cyberattacks on Applications at Exponential Volumes
The volume of attacks on individual applications is exponential. Contrast Labs in our recently published “2020 Application Security Observability Report” found that an individual application experienced an average of 13,279 attacks each month over the past year. And while only 2% actually found a vulnerability, the hit rate is significant—266 per month or 3,192 for the year. Multiply that by the total number of applications in production, and the number becomes enormous—six figures for an organization with just 31 applications.
Application-related Data Breaches Explode
Considering the number of successful “connections” are happening with cyberattacks and application vulnerabilities, it is not surprising that the percentage of data breaches tied to application vulnerabilities more than doubled this past year—reaching 43% according to Verizon. In a separate study, Forrester uncovered a similar finding, with 42% of organizations indicating they experienced a cyberattack in the past year that was due to an application vulnerability exploit.
Successful Application Compromises
In Contrast Security’s recently completed survey of development, security, and operations leaders, we found that many application vulnerability exploits are resulting in serious business harm. Over 25% of respondents indicate they experienced more than six successful application compromises in the past year. More than 6 in 10 said they had more than three, with only 5% indicating they had none.
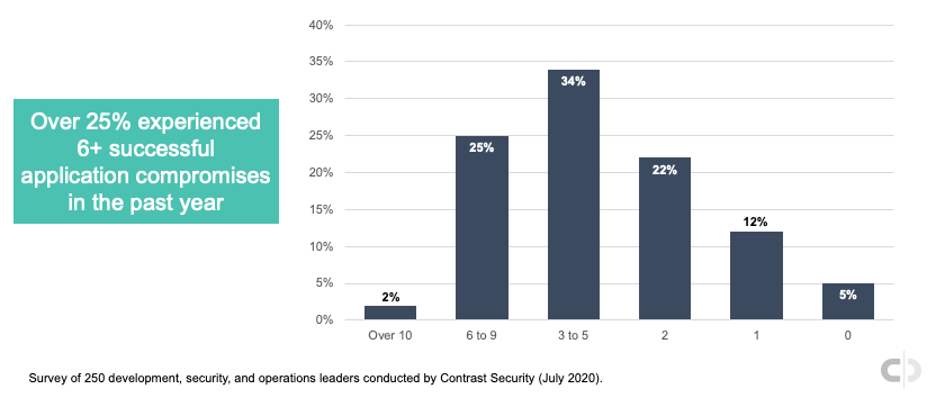
Frequency of successful application exploits
Repercussions of Successful Application Exploits
Organizations that experience successful application vulnerability exploits admit they led to deleterious business repercussions. In our recently completed survey, we asked survey participants if application vulnerability compromises resulted in brand degradation, exposure of business-critical data, and/or disruption or outage in operations. Nearly three-quarters said they experienced an operational disruption or outage, 66% revealed they had business-critical data exposed, and 62% experienced brand degradation. No business impact was listed by only 1% of survey respondents.
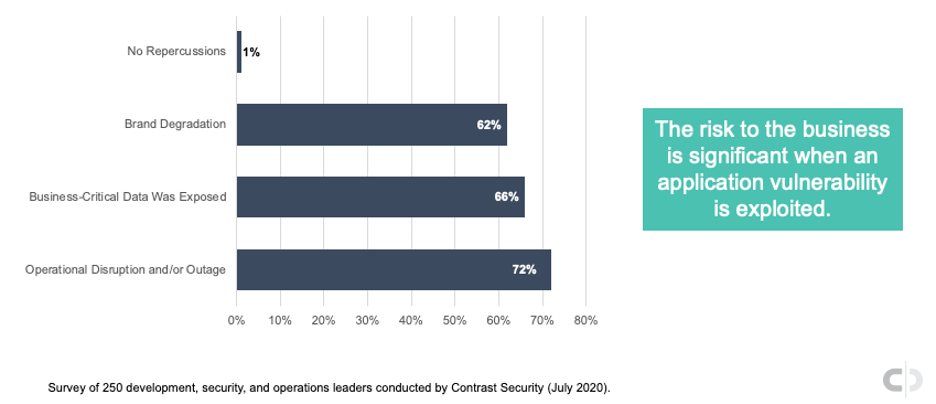
Repercussions of successful application cyberattacks
These data points align with the just-released Ponemon and IBM research report on the financial repercussions of successful cyberattacks. The study highlights an average cost per breach of $3.86 million and an average of 280 days to identify and contain. And while the cost per breach slightly decreased from 2019 to 2020, the findings indicate a growing divide between those with mature cybersecurity strategies and those that are lacking in them.
Some Recommendations to Combat the Advanced Threat Landscape
The above illustrates the severity of the problem when it comes to protecting software from malicious cyberattacks. The application attack surface is growing in leaps and bounds due to the rapid adoption of Agile and DevOps, and the COVID-19 pandemic is only accelerating the pace of change. This wider exposure has not gone unnoticed. Cyber criminals “smell blood in the water” and are going—as they always do—to the areas where they have the greatest likelihood of gaining access to critical systems, applications, and data.
The upside is that organizations can do a number of different things to limit their application risk. Following are a handful that will get you started:
- Shift application security left; waiting for software releases dramatically increases the cost and time required to remediate vulnerabilities
- Virtually eliminate false positives generated by legacy static and dynamic application scanning solutions that create alert fatigue, overwhelm security and development teams, and lead to missed true vulnerabilities
- Extend application security from development into production using a platform approach. Using runtime application self-protection (RASP) with security instrumentation enables SecOps teams to protect both SaaS and proprietary software applications from cyberattacks when running in production.
For more recommendations on developing an application security strategy that reduces risk while enabling the business, check out the Inside AppSec podcast—“Instrumentation Disrupts Application Security—from Development Through Production.”
Learn More About Sophisticated Application Cyberattacks
For those interested in gaining insights around the rapidly expanding application attack surface and the advanced threat landscape—including some of the tactics cyber criminals are using to exploit vulnerabilities, make sure to register for our upcoming webinar, “Assessing the Risk from the Confluence of an Expanded Application Attack Surface and Advanced Threat Landscape.” The moderated webinar will also cover how bots, brute-force attacks, artificial intelligence (AI) and machine learning (ML), and other sophisticated attack techniques make it increasingly difficult to protect software from malicious exploits.









