It is likely no secret to readers of the AppSec Observer Blog that serverless computing has moved into the mainstream over the past two years. The reason for this trend is clear: By removing the burden of maintaining server infrastructure for applications as they are developed and move into production, serverless applications enable faster release cycles, greater business agility, and lower cost.
Unfortunately, Contrast’s 2021 State of Serverless Application Security Report demonstrates that security has not kept up with this pace of innovation at most organizations. Released today, the report contains research based on a survey of 250 DevOps, application security, and cloud operations professionals in individual contributor and middle management roles. Respondents come from 24 countries around the world and work for companies with more than 5,000 employees.
RECOGNIZING SECURITY CHALLENGES
While serverless architecture has the potential to provide the best security for applications, an organization’s security strategy must take into account several special challenges posed by how serverless environments are designed. Serverless applications are often more complex, and the fact that the software is divided into its component functions makes for a more porous perimeter and an expanded attack surface. “No-edge blindness” resulting from functions that have no public-facing URL also brings visibility challenges.
The good news is that organizations tend to recognize these challenges. More than two-thirds of respondents consider security to be very important or critical to their serverless strategy, and half of respondents report that their application security budget increased in 2021—perhaps in part to address serverless security. Larger majorities of technology (66%) and financial services companies (59%), as well as organizations in the Asia-Pacific region (60%), increased investments in application security.
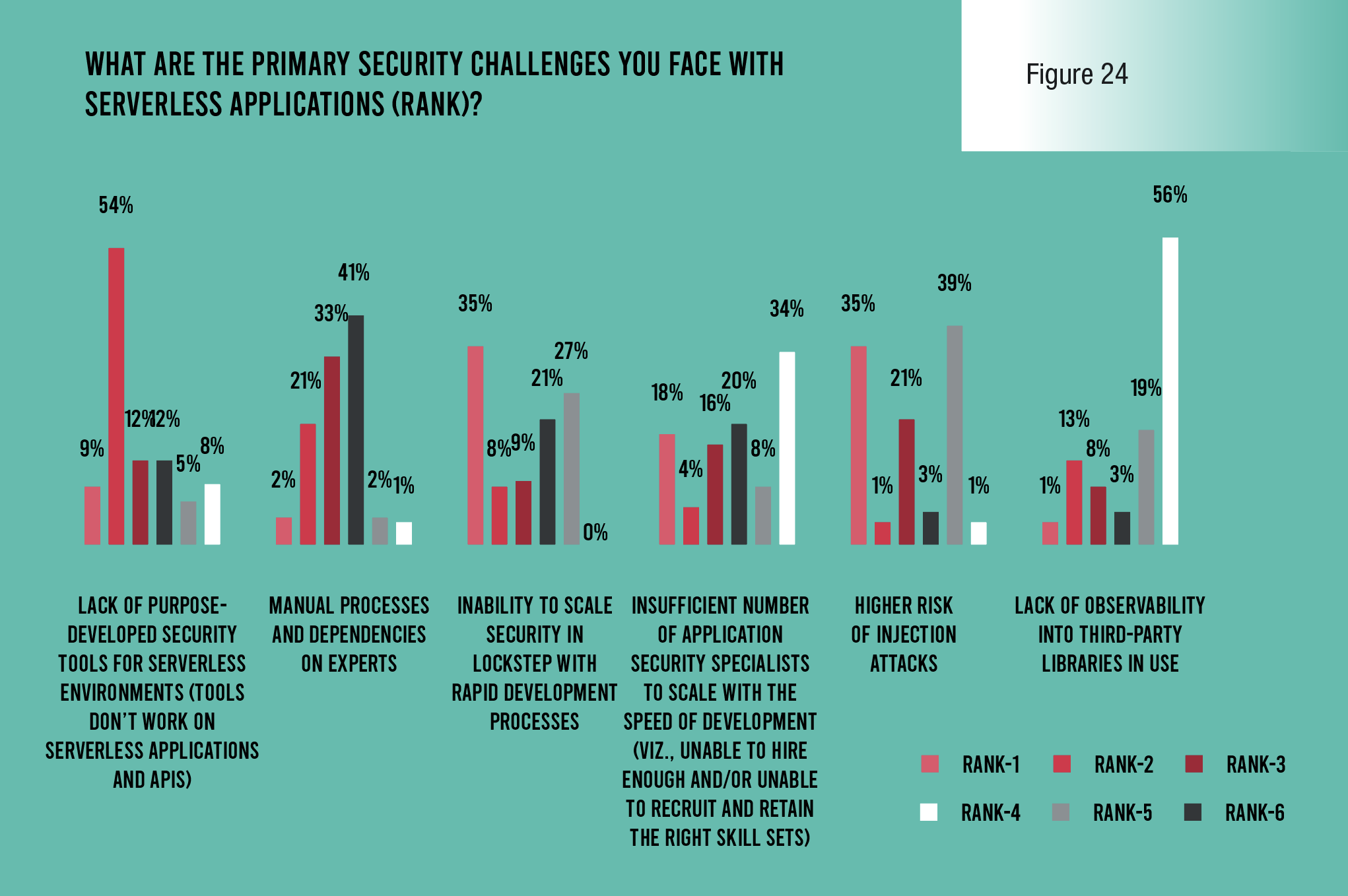
It was interesting to see the results when respondents are asked to rank a list of security challenges they face in serverless security. Looking just at the highest-ranked answer for each respondent, two problems were most common by far: the inability to scale security in lockstep with rapid development processes, and an increased risk of injection attacks. Of course, the second problem is caused by the first.
LOOKING THROUGH ROSE-COLORED GLASSES
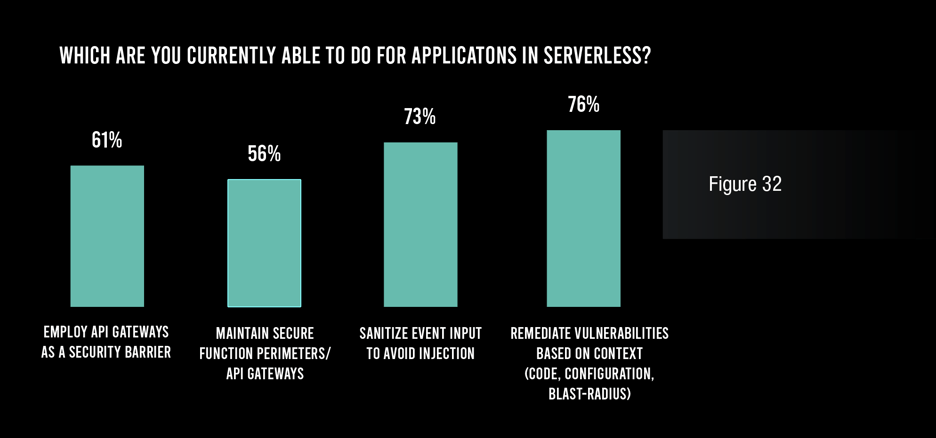
While respondents were quite realistic in defining the security challenges they face with their serverless applications, they tend to be overly optimistic about how well they are addressing them. Large majorities of respondents claim the ability to perform four specified security best practices (see below), and an astounding 62% say that they remediate vulnerabilities in their serverless applications within one day. This claim is especially common in the manufacturing, healthcare, and retail/hospitality sectors.
We believe these claims are exaggerated because of the disaggregated tool soup that respondents report using—and, more importantly, the security outcomes to which they admit. I discuss both of these issues below.
SIMMERING A SECURITY TOOL SOUP
Looking again at the question about serverless security challenges, the most commonly cited number two answer is a lack of purpose-built security tools for serverless environments. This problem is directly related to the inability to scale security to serverless environments and delineates a central problem in serverless security today.
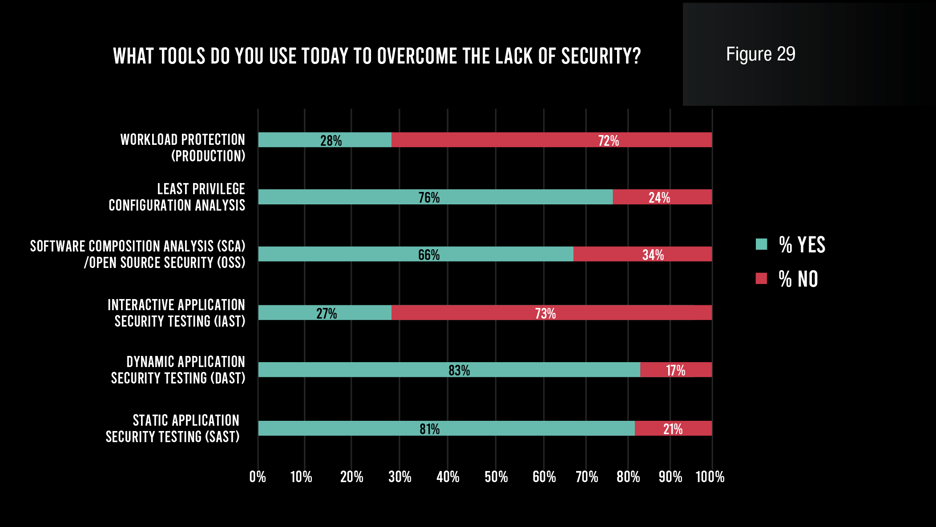
The result is that large majorities of respondents retrofit existing toolsets to try to protect their serverless applications—including workload protection (28%), software composition analysis or open-source security (SCA/OSS; 66%), and static application security testing (SAST; 81%).
These tools are often totally unconnected with each other and work less well with non-serverless applications than they did a decade ago. Open-source and custom code is addressed within separate silos, and virtually every tool has a high false-positive rate. And in a telling indicator that security bottlenecks are negating some of the benefits of serverless, a huge majority of respondents (86%) say that their serverless security tools consume more than 20 staff hours per week for administration.
BUILDING A SERVERLESS SECURITY DEBT
These disaggregated tools bring not only degradation in operational efficiency, but also reduced security. This becomes crystal clear when 71% of respondents admit that the average serverless application has more than 10 vulnerabilities—and 43% say that number is above 15. Tellingly, no respondent claimed fewer than two vulnerabilities per application. This is despite the fact that 65% of organizations scan their serverless applications daily.
These backlogged vulnerabilities represent a significant security debt for the organizations that own the applications in question. It reflects the fact that developers are unable to address vulnerabilities as they occur, but instead must fix them long after additional code has been layered above where the problem exists. Since vulnerabilities are more time-consuming and expensive to fix later in the process, this can cause delays in release cycles, diminishing cost-effectiveness for going serverless, and even potential attacks for applications in production.
ENDURING DATA LEAKS, FAILED AUDITS, AND SUCCESSFUL ATTACKS
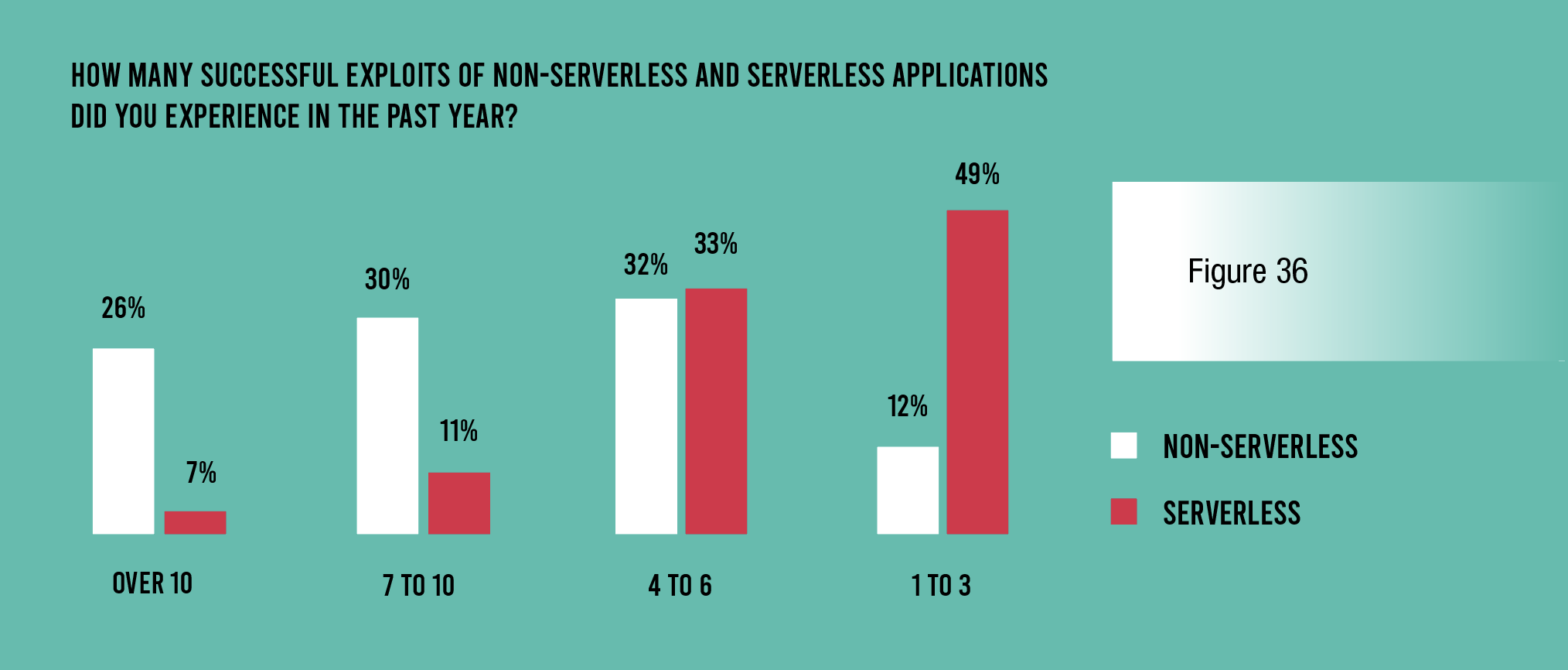
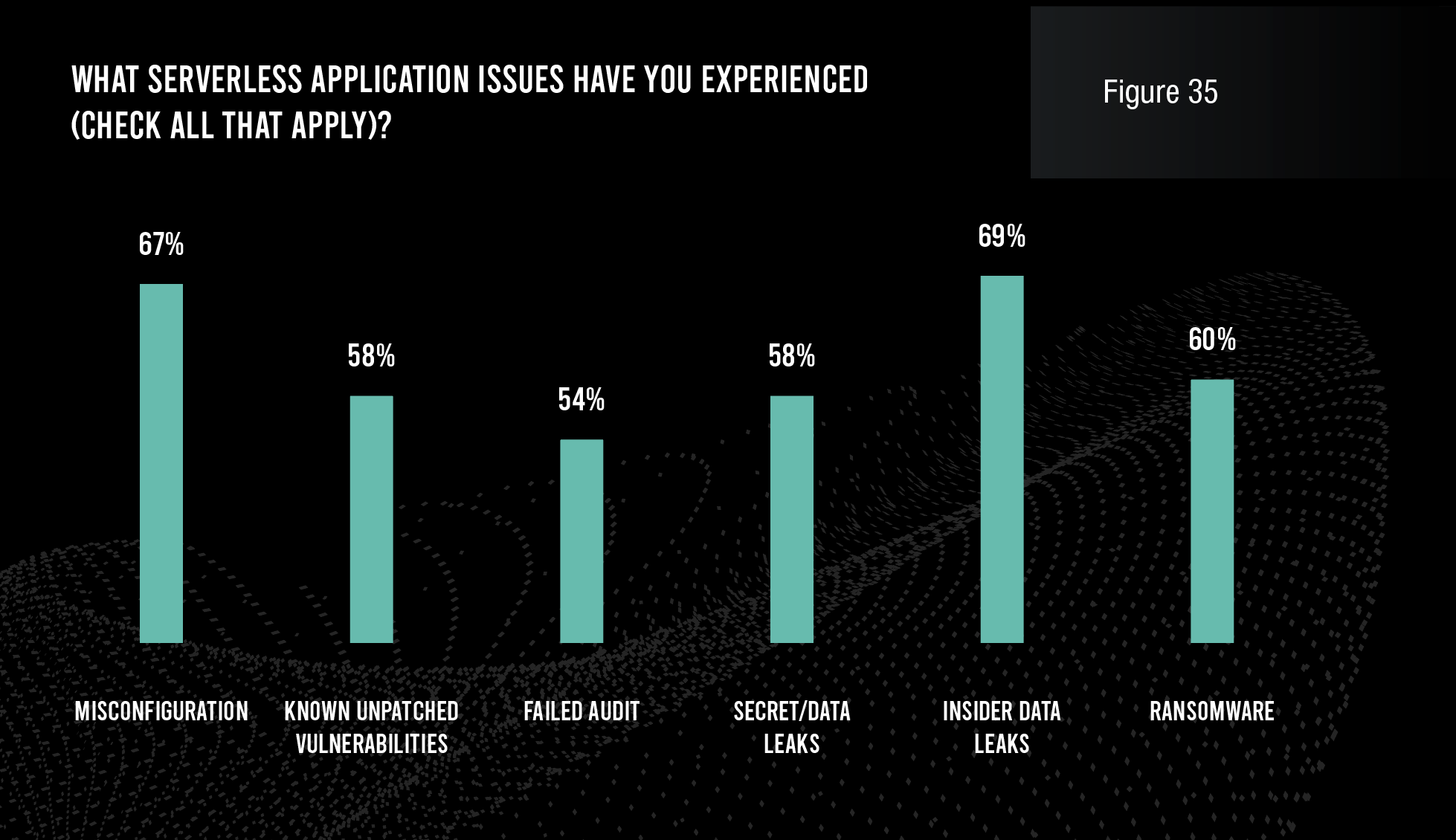
Poor security outcomes do not stop with vulnerabilities, unfortunately. Large majorities of respondents admit to have experienced misconfigurations, known unpatched vulnerabilities, insider data leaks, other data leaks, and ransomware in their serverless applications. A majority (54%) have even failed an audit. Even worse, a majority (51%) have experienced four or more successful exploits with their serverless applications over the past 12 months.
An even higher percentage of respondents (88%) experienced four or more successful exploits with their non-serverless applications, which could suggest that the serverless ones are more secure—admittedly a low bar to clear. However, the answers were interesting when respondents were asked to speculate as to why fewer successful attacks occurred with serverless applications. Half of them admit that the reason is a reduced capacity to detect attacks with serverless applications. For all they know, successful attacks on serverless applications may be even more common than with those on traditional infrastructure. They just cannot see all the attacks.
ORGANIZATIONS NEED A PURPOSE-BUILT TOOL
Serverless computing will undoubtedly continue to gain prominence in the coming years. The myriad benefits of entrusting server and database management to someone else are impossible to deny. This means that application security teams must accelerate their own innovation to match the pace of their DevOps colleagues to keep these growing environments secure. Organizations need to do a better job in reducing their serverless security debt by addressing vulnerabilities as they occur. And crucially, they must achieve full security observability for both serverless and non-serverless applications.
To do this, organizations must design a serverless application security strategy that accounts for the unique aspects of serverless computing and enables developers to solve problems in real time. In other words, what is needed is a comprehensive, purpose-built tool for serverless security.
Fortunately, such a solution already exists. Contrast Serverless Application Security offers a purpose-built solution for serverless security that is accurate and efficient. It also enables the integration of serverless and non-serverless application security as a part of the Contrast Application Security Platform.
Contrast’s serverless solution enables full observability of the entire serverless environment, including AWS Lambda functions, with near-zero false positives. Its resource map automatically discovers and presents a visualized graph of all resources (e.g., S3 bucket, API Gateway, DynamoDB) and their relationships within tested environments in a few short minutes per session. This helps security teams quickly identify weak spots and potential risks.
Contrast Serverless Application Security uses context-based static and dynamic engines to automatically detect vulnerabilities, and then helps developers easily fix the problem themselves with guided remediation. It suggests a tailored least-privilege policy for each Lambda function based on its actual needs to address identity and access management (IAM) vulnerabilities. And it addresses custom and open-source code with a single tool.
SERVERLESS IS IN EVERYONE’S FUTURE
Virtually every enterprise—and more than a few small and midsize businesses—will be developing serverless applications in a year or two, if they are not already. Unfortunately, as research by Contrast has shown, many organizations still struggle to provide adequate security for their non-serverless applications. And as we have seen, serverless environments pose even more complex security challenges. It is time for every organization to take tangible steps to ensure that their security efforts keep up with the incredible speed and innovation that their colleagues in DevOps are achieving.
Additional Resources
Report: Outlook of Serverless Application Security Report: Here
Inside AppSec Podcast: Key Takeaways From a New Serverless Application Security Report: Here
Webinar: Assessing the Current and Future Outlook of Serverless Application Security: Here
Blog: Contrast Delivers Developer-friendly Security for Serverless Applications: Here
White Paper: Quickly and Easily Scale and Secure Your Serverless Application Security: Here