Spring4Shell Vulnerability: What Steps to Take Now
Protect your Java applications against exploits like Spring4Shell.
What is the Spring4Shell Vulnerability
Spring4Shell is a 0-day Remote Code Execution (RCE) vulnerability was discovered Tuesday, March 29, 2022 impacting applications using certain versions of the Spring Framework and Java running on Apache Tomcat. A change introduced in Java 9 roughly five years ago combined with the Spring Framework can lead to vulnerable applications.
WHAT IS SPRING FRAMEWORK
The Spring Framework is the foundation for most enterprise applications written in the Java programming language. Our recent data showed Spring Core as being used by 74% of Java applications. Specifically, Spring provides the "plumbing" of enterprise applications so that teams can focus on application-level business logic, without unnecessary ties to specific deployment environments
why does the Spring4Shell Vulnerability matter to me?
Here are a few requirements for an application to be vulnerable:
- Use Spring Framework 5.3.0 to 5.3.17 5.2.0 to 5.2.19 Older, unsupported versions are also affected
- Use Java (JDK) 9+Run on Apache Tomcat packaged as a WAR file (Spring Boot, jar packaging not impacted)
- Have a spring-webmvc or spring-webflux dependency
- Use form binding with name=value pairs – not using Spring’s more popular message conversion of JSON/XML
- You don’t use an allowlist -OR- you don’t have a denylist that blocks fields like “class”, “module”, “classLoader”
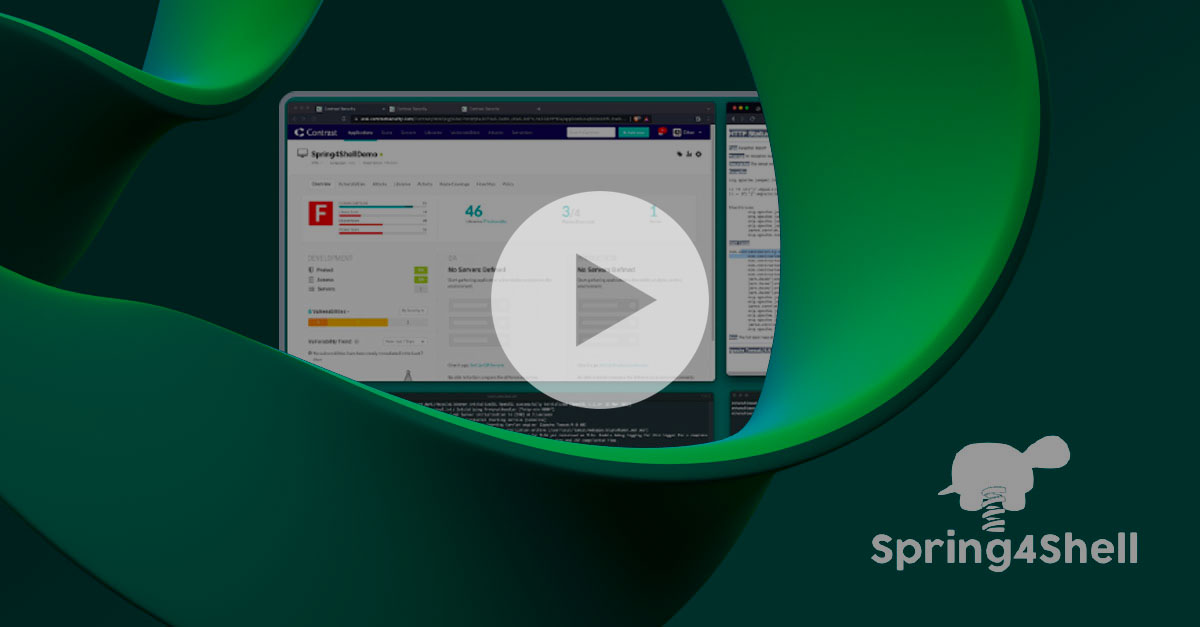
Preventing the Spring4Shell Exploit: a Demonstration
The video illustrates the Spring4Shell attack and how Contrast finds and stops the attack.
Contrast Protect
Can protect your Java applications against exploits like Spring4Shell.
CISO Guidance on Spring4Shell
Get a CISO security perspective on this latest vulnerability to learn the latest details and how to protect yourself now and going forward.
Additional Resources
Spring4Shell Vulnerability: What it is and how to prepare
BLOG
On March 29, 2022, a Chinese cybersecurity research firm leaked an attack that could impact most enterprise Java applications, globally. An investigation of the issue showed that the root cause was a vulnerability in the widely used, free, community-developed, open-source programming framework called Spring Core.
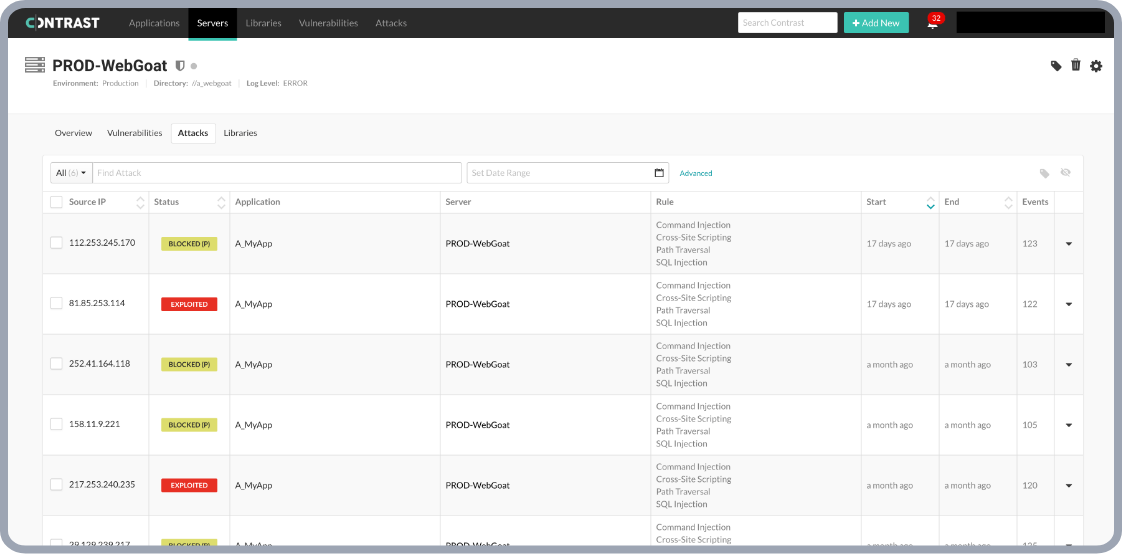
Preventing the Initial Spring4Shell Exploit
DEMO VIDEO
While planning to implement the suggested updates to both Spring and Tomcat, deploying Contrast Protect delivers immediate protection against Spring4Shell. Ethan Shimooka, Systems Engineer for Contrast Security, created this timely video highlighting the issue and easy implementation of Contrast Protect to shield against attacks.

CISO Guidance on Spring4Shell
ON-DEMAND WEBINAR
Get a CISO security perspective on this latest vulnerability to learn the latest details and how to protect yourself now and going forward.
Experience Contrast today
Leverage the Contrast secure code platform and service offerings to stop attacks at runtime with Contrast Protect.




.jpg?width=200&name=spring4shell-logo-(1).jpg)