Find and fix vulnerabilities that matter in your code.
Try Contrast
are patching vulnerabilities in a timely manner 1
waste time on vulnerabilities that pose minimal risk 2
days on average to fix an application security vulnerability 3
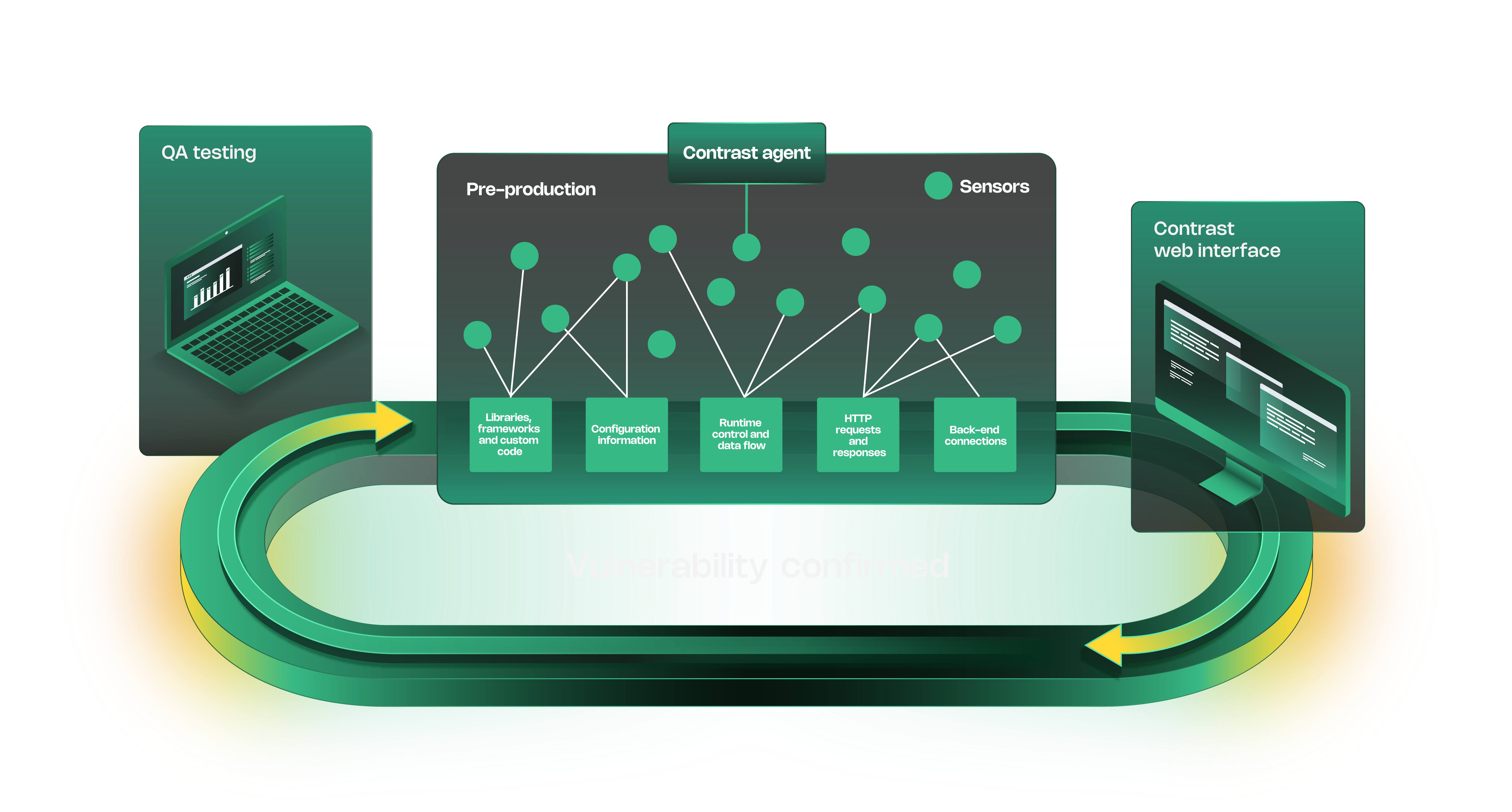
Detect vulnerabilities early to prevent security breaches and exploits
Continuously monitor applications and APIs for real-time security assessments

Reduce manual effort with seamless security integrations and automation
Streamline compliance by integrating security into CI/CD pipelines

Receive real-time guidance on security flaws and resolutions
Get actionable insights to remediate vulnerabilities efficiently

Detects and prioritizes vulnerabilities and guides teams on how to eliminate security risks.
In-depth visualization of application components, code trees and data flow.
Pinpoints exactly where a vulnerability appears in code, and how it works.
Identifies vulnerabilities to form a starting point for threat modeling remediation.
Provides a mapping of software routes that are executed during the testing.
Instantly identifies risks in running applications without scanning delays.
Embeds security into development workflows for proactive threat mitigation.
Enables developers to fix vulnerabilities easily without the need of security expertise.

Managed runtime security powered by the people who built it.
Learn more
