Detect and respond to attacks on applications and APIs before exploits occur.
Try Contrast
surge in the number of application and APIs attack in 2024 1
attacks bypass the WAF and exploit vulnerabilities in the average app monthly 2
of application security events take more than 12 hours to resolve 3
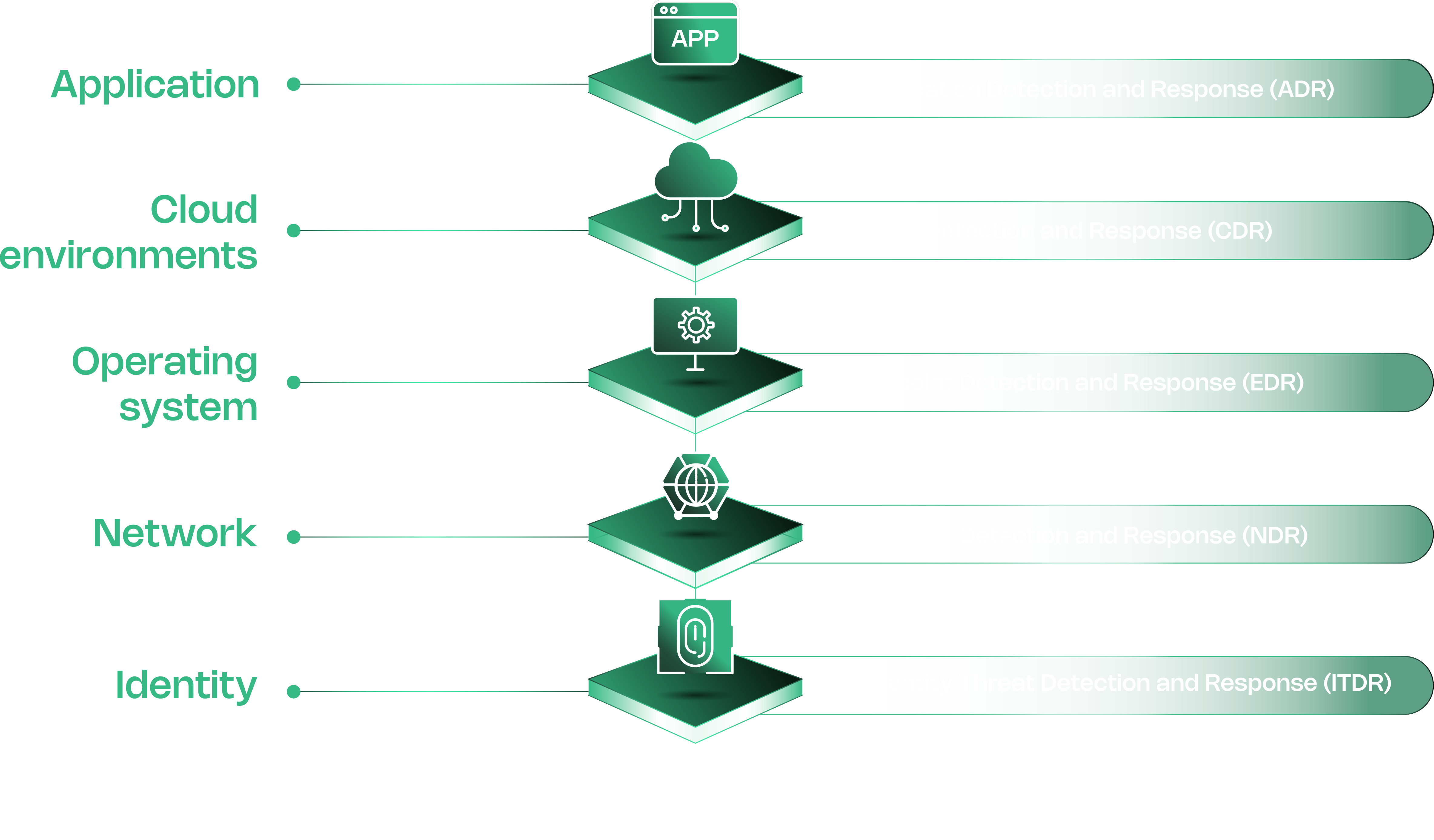



The Contrast Graph is the core of the platform, providing runtime intelligence that builds a unified, real-time security model for your entire application and API security ecosystem.
Learn moreRuntime protection blocking for application attacks, even if the exploit is novel.
Detects and alerts on anomalous behavior within the application layer.
Continuous application and library vulnerability monitoring in production.
Clear, actionable steps to quickly identify true positive attacks and contain threats.
Gain context from application alerts related to suspicious activity, payloads, IoCs and more.
Real-time security blueprints provide context to incidents better to assess the impact of an attack.
Integrate accurate ADR alerts to monitor and triage across the SIEM, XDR, SOAR and CNAPP.
Respond efficiently with insights from inside your applications.
Continuous visibility into exposure of your applications in production, enabling proactive risk mitigation.
Add context to attack vectors with vulnerability data, enabling faster and more effective triage and response.
Automatically generate a fix for critical vulnerabilities with Contrast AI.
Focus on the vulnerabilities that truly matter, reducing backlogs and accelerating remediation efforts.

Managed runtime security powered by the people who built it.
Learn more
ADR directly addresses the challenge of securing applications, one of the most common entry points for cyber attacks. It closes the visibility gap at runtime, providing the accuracy and context that security teams need to differentiate real threats from noise. This allows teams to effectively protect their production applications and APIs from active exploits.
ADR is used to provide active, real-time protection for production applications and APIs. Its primary function is to provide a structural defense against zero-day exploits and other novel attacks. By identifying and blocking threats at runtime, ADR also plays a key role in an organization's overall attack surface reduction strategy.
ADR embeds lightweight sensors into the application's runtime environment to analyze its behavior as it executes. This is critically important because it allows ADR to detect malicious activity based on how the application is behaving, not just by matching known-bad signatures. This runtime visibility enables effective detection and blocking of application attacks, including common threats such as SQL injection and unsafe deserialization attacks, as well as emerging threats like zero-day vulnerabilities.
ADR protects against zero-day threats by focusing on behavioral detection and attack techniques rather than known signatures. Because its sensors operate inside the code, it can detect and block entire classes of attacks (like command injection or deserialization) at the framework level. This provides a structural defense against novel exploits, even without a specific CVE or patch.
ADR delivers high-fidelity, verified alerts directly into the SIEM. Each alert is enriched with deep contextual data, including the exact line of code, stack trace and attack payload. This reduces the need for manual validation and provides the rich data required for rapid, automated incident response.
The best platforms provide accuracy through behavioral analysis at runtime, not just signature matching. They should also provide true inline blocking to stop an attack before it becomes a breach. Finally, a leading solution should not only block active threats but also list the associated vulnerability to help teams proactively reduce the application attack surface.
