
A 34% surge in vulnerability exploitation marked a significant shift in how breaches began last year, with this method now accounting for 20% of initial access, according to Verizon’s 2025 Data Breach Investigations1 report. This surge puts immense pressure on security operations teams tasked with protecting vital applications and Application Programming Interfaces (APIs). Yet, these teams often find themselves battling tool limitations. Traditional Web Application Firewalls (WAFs) operating outside the application generate a flood of alerts based on simplistic traffic patterns, burying real threats in a sea of false positives.
Meanwhile, newer OS-level visibility tools, often leveraging technologies like eBPF, offer deep insights into kernel activity and system calls. While valuable for infrastructure monitoring, they fundamentally lack application context. They can't see inside the application's code, logic or data flows, making it difficult to accurately identify application-specific threats or understand their true risk, let alone respond effectively without disrupting the business. SecOps needs a better way to both detect and respond with precision.
Contrast Application Detection and Response (ADR) provides unparalleled visibility, accuracy and response capability by working from inside each application. Using threat sensors that integrate seamlessly and safely within the application runtime, Contrast gains continuous, deep runtime context — seeing actual code execution, data flow, library usage, configuration, backend connections and more, precisely as the application experiences them.
Contrast ADR leverages this deep context to perform behavioral detection, tracking data flow and analyzing code logic as it executes within the runtime. Unlike tools relying on signatures or system calls, runtime analysis identifies behavioral anomalies and malicious patterns based on their actual runtime interactions, pinpointing only genuine threats.
Operating from inside the application provides advantages unattainable by other methods:
While OS-level tools see system calls originating from various sources, Contrast ADR understands the specific application logic initiating many of those calls, providing crucial context. External tools often have to guess how the application will interpret complex payloads, leading to misinterpretations or missed attacks. Because Contrast ADR operates inside the runtime, it sees data after it's been processed by the application's frameworks, exactly as the application logic handles it, ensuring analysis is based on ground truth. Furthermore, this deep context enables precise response. Contrast ADR can prevent specific exploits attempts from causing damage while allowing legitimate users to continue using the app/API. By comparison, eBPF-based tools generally operate asynchronously, limiting their response options for application logic attacks primarily to reporting for external/delayed action (like packet filtering or sending notifications) rather than direct, inline prevention within the application flow. True ADR requires deep application context for both accurate detection and precise response.
By analyzing actual application behavior and verifying risk within the runtime context, Contrast ADR distinguishes attempted exploits from legitimate software behavior. This accuracy not only stops the flood of false positives but also gives teams the confidence to enable active blocking, knowing that legitimate activity won't be impacted. Furthermore, unlike signature-based WAFs that require constant updates for new threats, Contrast ADR's behavioral detection focuses on the underlying techniques (the classes of attack). This allows it to detect and block novel variants and even zero-day attacks that exploit vulnerabilities within known classes (like SQLi, path traversal, etc.) without requiring specific signatures. Essentially, Contrast ADR takes critical tools out of the attacker's toolbox by preventing the core behaviors required to exploit applications.
Kernel module
eBPF program
Software instrumentation
Contrast's behavioral detection works through advanced analysis powered by unique runtime context. Contrast confirms active threats by observing their direct impact and identifying key behavioral anomalies across different dimensions:
These are just some examples that show some of the essential detection techniques; Contrast ADR also recognizes other behavioral irregularities to ensure complete security. High-fidelity detection of runtime behavioral anomalies directly powers precise, optional in-application blocking of attacks. Contrast ADR can be configured to intervene exactly where needed, halting the specific malicious operation or request within the runtime, offering effective protection with minimal disruption.
Furthermore, when an attack is detected, the Contrast platform provides developers with rich diagnostic details about the underlying vulnerability, including the exact line of code, stack traces, data flow analysis and remediation advice, accelerating permanent fixes and improving the application's security posture.
Contrast ADR’s behavioral detection understands attack techniques, not just known patterns found in signatures. This provides inherent protection against many zero-day threats that exploit known vulnerability classes, closing the critical gap left by signature-based tools.
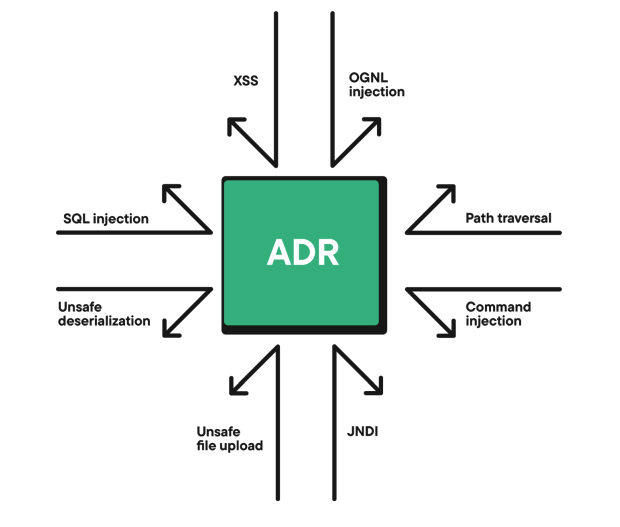
Contrast's behavioral detection and response capabilities protect applications and APIs against a wide array of critical attack patterns. Contrast coverage includes crucial OWASP Top 10 risks and other sophisticated techniques attackers use to compromise applications from within.
Contrast ADR deploys easily via lightweight threat sensors with minimal performance overhead. Get accurate runtime protection without complex tuning or disruptive changes.
 Actionable intelligence that accelerates and informs response
Actionable intelligence that accelerates and informs responseDetecting and blocking a threat is critical, but seamless integration into existing security operations is just as important. Contrast ADR provides rich, actionable intelligence that integrates seamlessly with leading SIEM platforms and ticketing systems. This allows SecOps teams to correlate Contrast's deep application insights with data from across their security stack, incorporating accurate application threats into their existing workflows.
Every alert includes precise context — exact code location, full data details, environmental specifics and more — slashing Mean Time To Detect (MTTD) and Mean Time To Identify (MTTI) and informing developers for faster Mean Time To Respond/Remediate (MTTR), all within the tools operations teams use every day.
With Contrast ADR, security operations teams can finally gain control over application risk. Empower the security operations center (SOC) to:
| Focus on actual application threats | Prioritize high-fidelity alerts originating from deep within each application. |
| Gain full application visibility | See attacks unfolding inside the runtime where other tools are blind. |
| Detect critical threats | Ensure comprehensive coverage against sophisticated application-layer attacks. |
| Protect against zero days | Proactively block novel attacks exploiting entire vulnerability classes. |
| Respond with precision | Benefit from accurate, in-application blocking that stops attacks, not the business. |
| Accelerate incident response and remediation | Leverage rich, actionable context integrated into existing SOC workflows. |
| Secure applications and APIs | Effectively protect the complex applications and APIs that drive the business. |
Schedule a demo and see how to eliminate your application-layer blind spots.
Book a demo
