Prioritize and address risks with faster application and API vulnerability detection and fewer false positives.
Try Contrast
high-risk vulnerabilities in 79% of applications 1
increase in application exploits year over year 2
days to fix an application security vulnerability 3
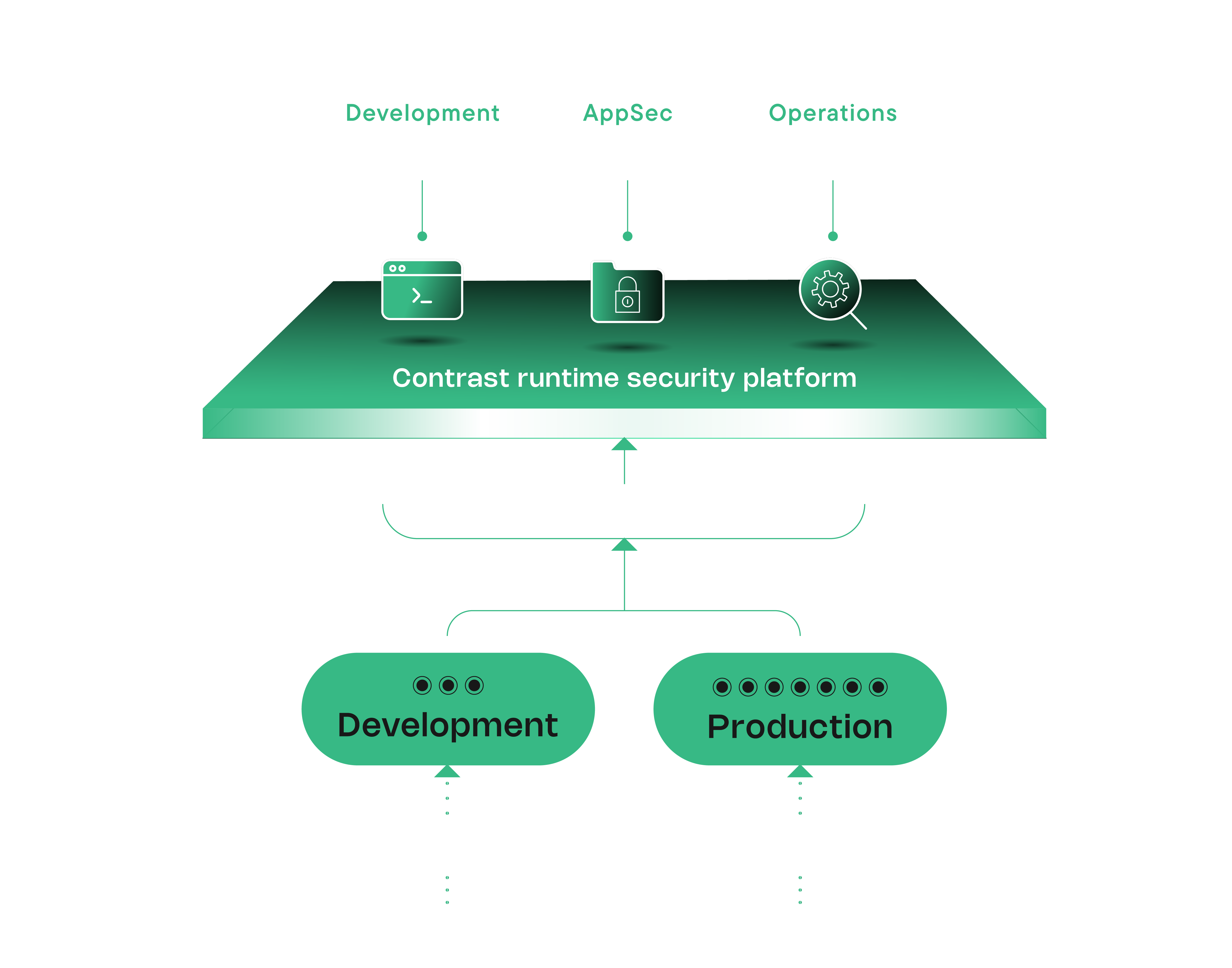
Contrast AST maps data flows within applications, accurately identifying the potential for exploits such as SQL injection, cross-site scripting and insecure configurations by analyzing code paths at runtime.

Contrast AST’s runtime agent provides security insights from directly inside the application, eliminating the need for separate scanning environments. Contrast integrates seamlessly into tools such as Jira, Jenkins, and GitHub, streamlining DevOps workflows.

Contrast AST detects vulnerabilities as code is written, delivering actionable insights to resolve issues faster and reduce security expertise technical debt.

The Contrast Graph is the core of the platform, providing runtime intelligence that builds a unified, real-time security model for your entire application and API security ecosystem.
Learn moreUncover known and unknown risks at every stage of the SDLC without the burden of scanning.
Find vulnerabilities in third-party applications, custom code and all their dependencies.
Monitor applications at runtime to find vulnerabilities without producing false positives.
Integrate seamlessly with existing DevOps and CI/CD workflow tooling.
Actionable insights pinpoint the exact code causing the issue, speeding remediation.
Give developers a head start on eliminating risks quickly.
Secure Java, .NET, and Python applications and many more.
Meet compliance requirements without slowing down development or deployments.

Managed runtime security powered by the people who built it.
Learn more
Get the Gartner® view of Application Security Testing and see why Contrast is recognized as a Visionary.
Read more