Scalable Software Supply Chain Security
Continuous monitoring and protection for your critical custom and third-party software assets
The Software Supply Chain Security Challenge
Along with custom code built in-house, the software supply chain introduces security and visibility gaps stemming from third-party software imported from unknown or untrusted sources.
Lack of Visibility
Problem: Understaffed security teams have no centralized means of benchmarking their third-party software inventory including both commercial and open-source libraries deployed across their environment. With new code changes shipping multiple times per day, security teams can't keep up with the dozens of libraries introduced from unknown sources.
Implication: Without understanding which third-party software assets carry security defects or potential licensing risk, security teams can’t fully comprehend where their commercial and open-source software supply chain security is vulnerable.
Results Overload
Problem: Juggling separate tools for testing custom and third-party code creates hours of unnecessary work as a result of erroneous findings and a lack of context into how libraries are invoked by custom code. Developers are left overwhelmed with the sheer volume of results with no context into how to fix them or if they're valid.
Implication: Security teams don’t have a way to prioritize software supply chain security findings and end up chasing fixes for results that don’t matter, creating strain with their developer counterparts.
No Rapid Response Plan
Problem: As new vulnerabilities are disclosed for older libraries, managing security debt becomes more complicated. Patching or updating libraries is not always a turnkey solution. Patches may break builds, or don't exist because there's no active development for specific projects. In order to meet deadlines, developers have no choice but to ship code with exploitable libraries.
Implication: In the event of a zero-day vulnerability, businesses run the risk of opening themselves up for attack when shipping vulnerable libraries into production.
The Contrast Security Solution
Centralized platform for complete software supply chain security across the entire software development lifecycle - from code, through test, to production.
Comprehensive Software Bill Of Materials (SBOM)
In order to meet regulatory and procurement requirements, Contrast generates a comprehensive software bill of materials via the Contrast CLI or a simple API call. Contrast complies with the minimum SBOM standards outlined by NIST detailing critical security, versioning, environmental, and library usage information.

End-to-End Software Supply Chain Risk Intelligence
The Contrast Secure Code Platform catalogues custom, commercial, and open-source software assets and flags risk across the entire development lifecycle - from build, to test, to production. Contrast provides governance within native CI/CD workflows and tests for potential attack vectors embedded in risky third-party libraries, transitive dependencies and out-of-policy open source licenses.
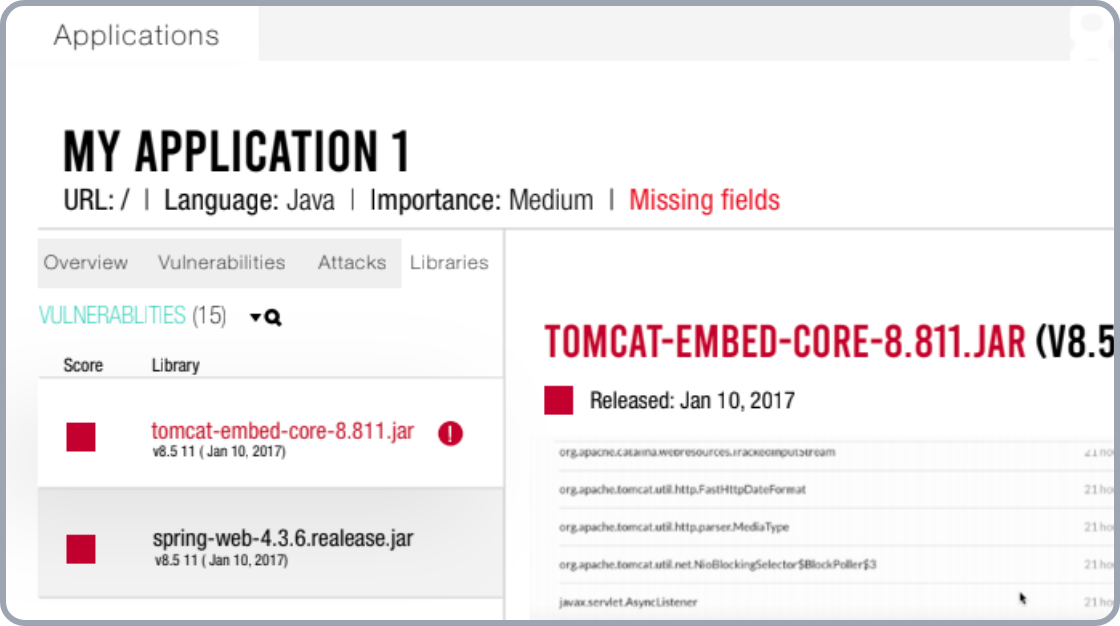
Targeted, Actionable Findings
Contrast provides real-time alerts for new vulnerabilities in third-party libraries, dependencies, and flags risky open source licenses. Because it doesn’t silo custom and third-party testing, Contrast can which libraries are actually invoked by the application during runtime, saving Security and Development teams from hours of needless, manual correlation.
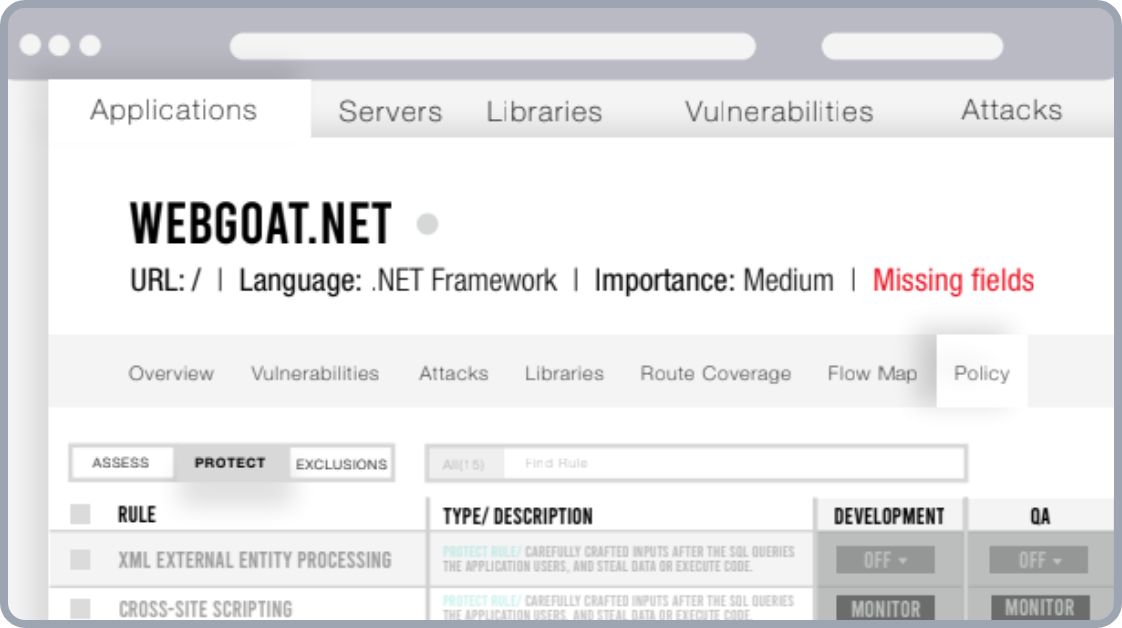
Protection In The Wild
When patching or updating a library is not an option, Contrast ensures that businesses are able to protect themselves from attacks against vulnerable libraries. Contrast comes with out-of-the-box protection rules that help safeguard exploitable libraries deployed in production.
Gartner® Report: Innovation Insights for SBOMs
New Gartner® Report Details How Businesses Should Incorporate SBOMS Into The SDLC
Resources

PRESIDENT BIDEN’S EXECUTIVE ORDER: SECURE THE SOFTWARE SUPPLY CHAIN
Blog
Read this Blog Post to learn what President Biden's Executive Order means for Federal agencies and how the Contrast platform can help them prepare to meet forthcoming requirements.

SECURING THE SOFTWARE SUPPLY CHAIN STARTS WITH A SOFTWARE BILL OF MATERIALS (SBOM)
Blog
Find out why SBOMs are the key to the security of the software supply chain and how Contrast Security is ensuring our customers have access to them.

CONTRAST SCA: AUTOMATED OPEN-SOURCE SECURITY SOFTWARE AND COMPLIANCE
Solution Brief
Open-source software (SCA) affords developers many freedoms to build feature-rich applications on aggressive timelines. However, reliance on SCA adds layers of complexity across an organization’s software supply chain.

Gartner® Report: Innovation Insights for SBOMs
Analyst Report
Download this Gartner® report to learn how maintaining a software bill of materials (SBOMs) can help your organization secure and govern software components throughout the software development lifecycle (SDLC).

Securing the Software Supply Chain in Modern Development Pipelines
On-Demand Webinar
Industry experts in software security and engineering discuss how to lock down your software supply chain at scale.

Demystifying OMB M-22-18: 5 Things You Need to Know
On-Demand Webinar
Moderated by our computer security industry veteran Lisa Vaas, Contrast Security co-founder & CTO, Jeff Williams chats with Contrast Security CISO, David Lindner, discusses early action steps you can take now, so you’re ready when you need to be
Learn How
Learn more about Contrast Security's centralized platform for complete software supply chain security across the entire software development lifecycle.




