Modern security teams are flying blind where it matters most: Inside the application
Based on the 1.6 trillion runtime observations Contrast sees per day, this report reveals what traditional tools miss and why attackers are winning at the application layer.
Download this threat report to see
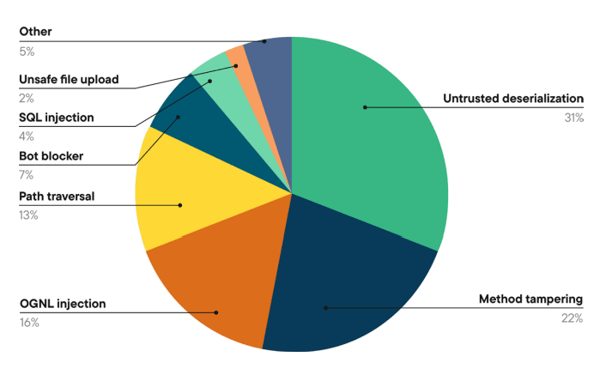
- 81 real attacks/month per app:
Confirmed, viable exploit attempts that reach vulnerable code
- 30 serious vulns per app, and counting:
Vulnerability backlogs are accelerating
- 5 days to exploit, 84 days to patch:
The risk gap is growing fast
- WAFs and EDRs can’t see these threats:
They miss what happens inside the code
- AI is making attackers more sophisticated:
Once-rare exploits are now common and scalable
Why Contrast's data is different
This isn’t survey data or scanner output. Contrast’s embedded runtime sensors capture what’s happening inside thousands of real-world applications, so this report reflects actual exploit behavior, not theoretical risk.
Get the full threat report to learn
- Which attack types dominate by industry and language
- Which types of attacks are just noise and which are worth your time
- How to shift from reactive defense to runtime protection




