May 12, 2021
Until recently, the word “Hafnium” most commonly referred to an obscure atomic element—atomic number 72 in the Periodic Table of the Elements. It was named for the city where it was discovered in 1923—Copenhagen, Denmark, whose Latin name is Hafnia. Chemically similar to zirconium, it is used for control rods in nuclear reactors.
But some readers of this blog are keenly aware of a newer use of this word. Hafnium is also the name of a state-sponsored threat actor said to be connected to the Chinese government. Its goal is to exfiltrate data from Western organizations of all types, including government and military secrets, medical research, and information on critical infrastructure.
While the group has been around for a while, it gained notoriety this year with its recent attack against several zero-day vulnerabilities in the Outlook Web Access interface for on-premises Microsoft Exchange Server deployments. The attackers may have seen this as an opportune time to attack a webmail interface, which might be more widely used when employees work from home. They also targeted a product that tends to be used by small and midsize organizations rather than larger enterprises that might have more sophisticated security measures in place.
Hafnium used automated methods to install backdoors in Outlook Web Access that enabled them to return later with full control of specific accounts. Victims include more than 30,000 servers in the U.S. and many more worldwide. Once the infiltration occurred, other threat actors were able to use the vulnerabilities to deliver a new ransomware family called DearCry that has already claimed numerous victims. To prevent even more bad actors from exploiting them, no announcement was made of the vulnerabilities for two months after their discovery, until Microsoft released a patch in early March.
Coming on the heels of the SolarWinds attack that was revealed in December of last year, the Hafnium attacks are another reminder that most organizations need to prioritize application security more than they do today. Contrast Labs’ newly released Application Security Intelligence Report for January–February 2021 finds that serious vulnerabilities are a growing problem in custom code. The bimonthly report, based on aggregate telemetry from the applications protected by Contrast Assess and Contrast Protect, helps security and development teams prioritize their application security efforts according to the latest trends.
The report starts with an update on Contrast RiskScores for the bimonthly period. As we described in a recent report, this numerical score (on a 10-point scale) provides an objective way to describe the relative risk of different vulnerability types based on what is happening in real applications.
Broken access control and cross-site scripting (XSS) continue to be the two most dangerous vulnerability types by far, with almost a two-point gap between them and the third-highest score. Broken access control attacks enable bad actors to bypass authentication safeguards and perform tasks only allowed for privileged users. XSS attacks compromise user interactions by inserting malicious scripts into websites being executed on the client side. They can also give cyber criminals privileged access to the victim applications.
Insecure configuration has been trending upward in RiskScore for several months, and it now has the third-highest RiskScore, displacing sensitive data exposure to fourth. SQL injection is once again trending upward after a steep decline in its RiskScore late last year.
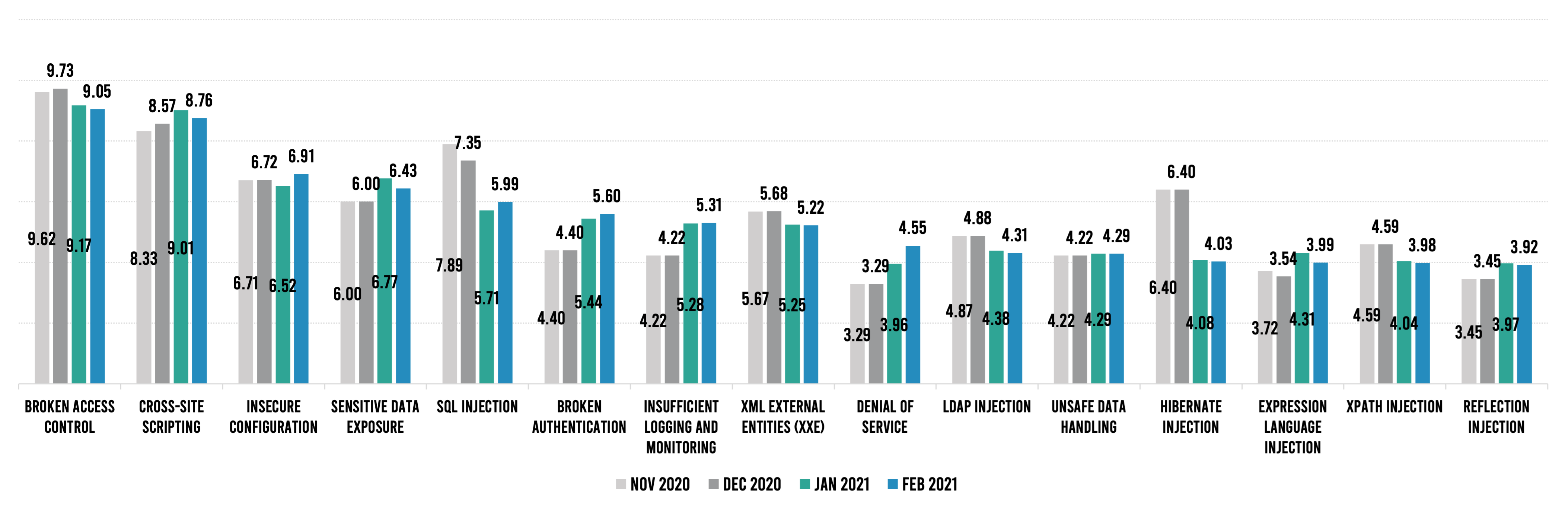
While the top five have remained remarkably consistent over the past year, fluctuations in “mid-tier” vulnerability types further down the list are perhaps more helpful in prioritizing application security efforts on a month-to-month basis. Broken authentication is now in sixth position after increasing from 4.4 to 5.6 over four months. For example, denial of service has been steadily increasing for eight months now, and hibernate infection fell over two points from the November–December time frame.
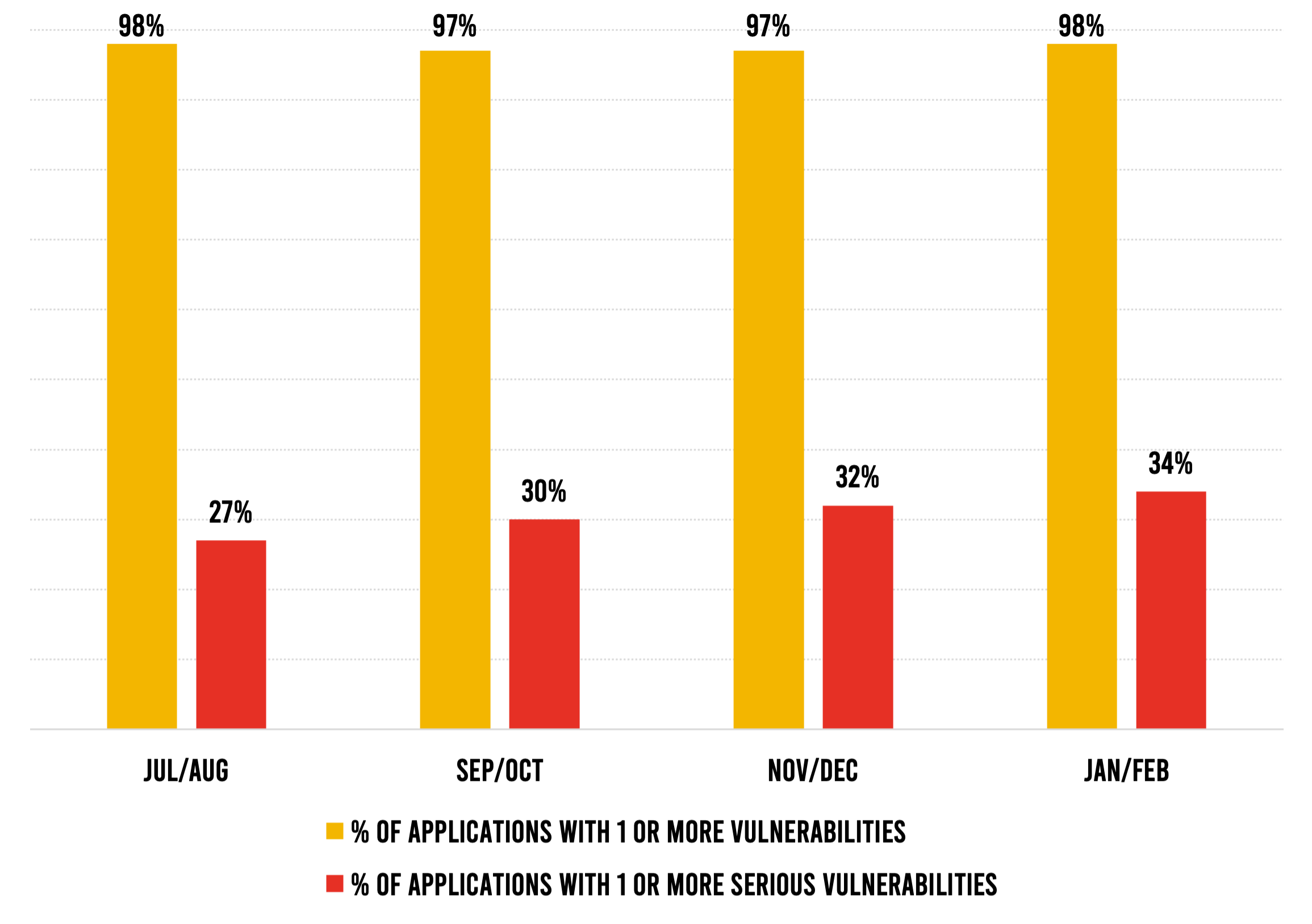
Telemetry from applications protected by Contrast Assess shows a troubling increase in serious vulnerabilities. The percentage of applications that contain at least one serious vulnerability has been steadily growing for eight months now, from 27% in July–August to 34% in January–February—a 26% increase. We all know that not all vulnerabilities in a piece of software pose risk to an organization, but the growing share of applications with vulnerabilities that are rated High or Critical is a concern.
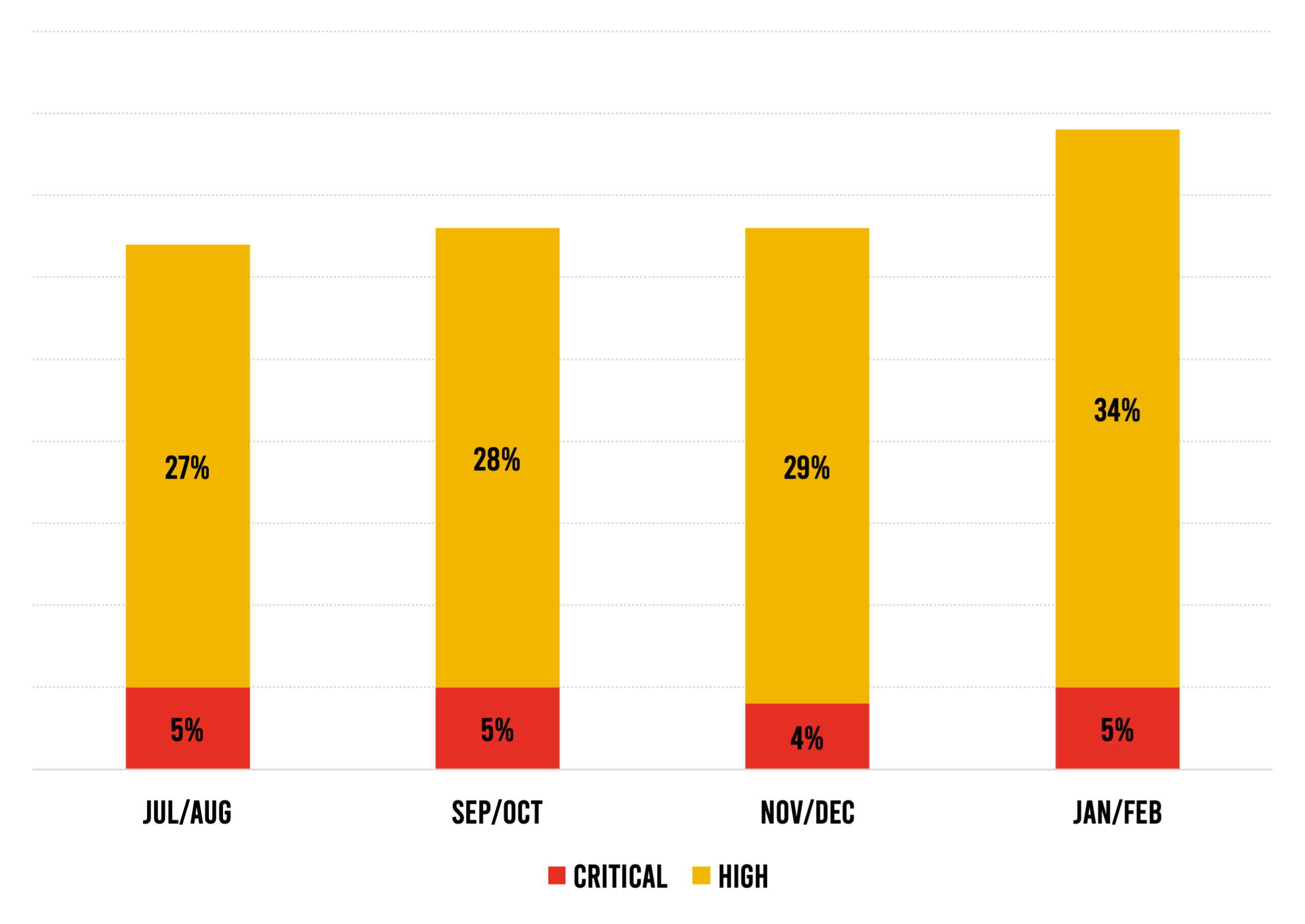
Serious vulnerabilities have also risen as a share of overall vulnerabilities—a trend that has continued for 10 months. There was an especially big jump in this figure between the last two bimonthly periods, from 33% in November–December to 39% in January–February—an 18% increase. Again, this is a concern because the trend seems to be that an increasing percentage of software vulnerabilities pose at least some risk to an organization.
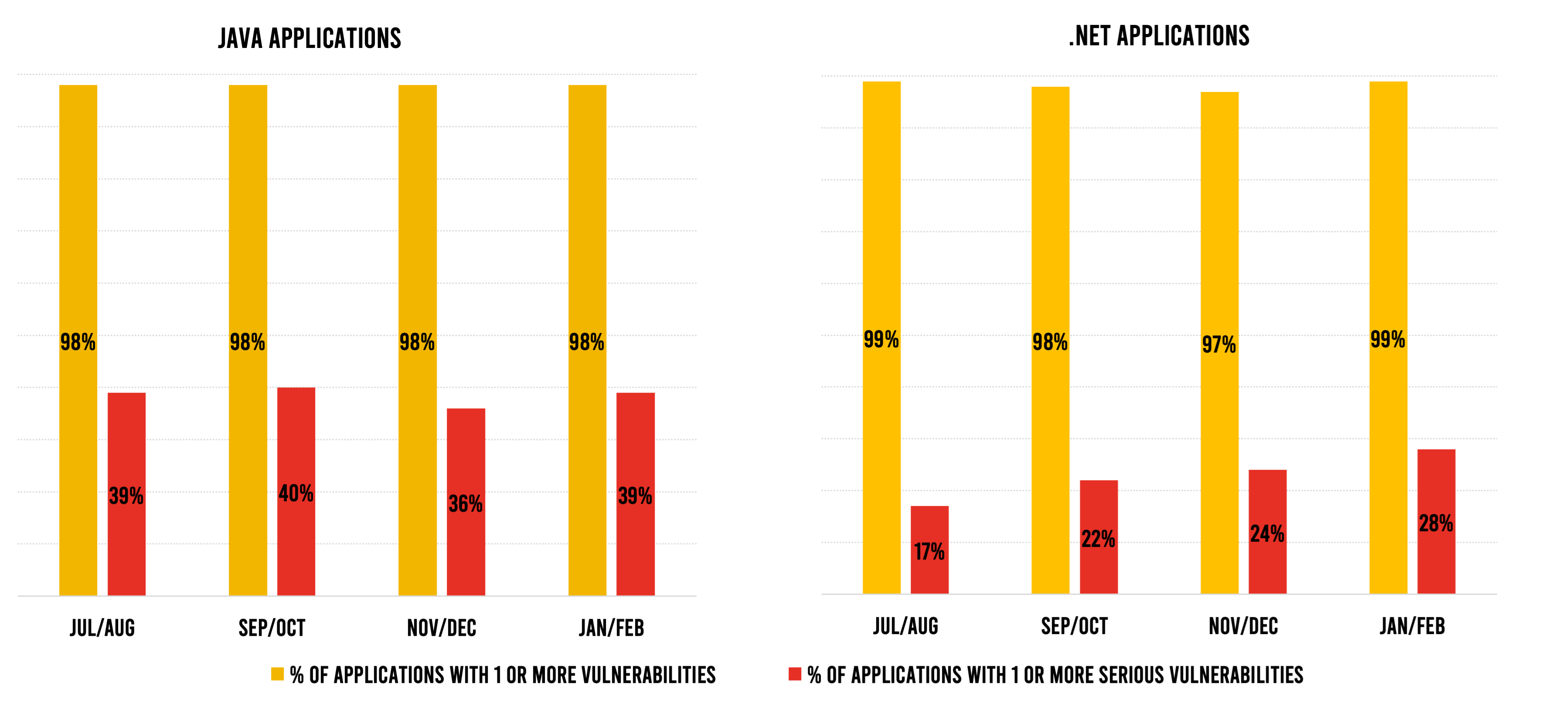
Looking at vulnerabilities by programming language, we see that the share of .NET applications that contain at least one serious vulnerability continued its upward trajectory, reaching 28% in January–February. This is the highest percentage in nearly a year and reiterates the fact that .NET is also susceptible to vulnerabilities—perhaps contrary to popular belief.
More Java applications had serious vulnerabilities as well—39% in January–February compared with 36% in the last two months of 2020. However, the 39% figure is closer to the average that we have seen over the past 18 months. Java remains the language that has the highest propensity for vulnerabilities, and the fact that so many Java applications have serious vulnerabilities remains a concern.
One other thing that should be noted about vulnerability trends: While a majority of applications are free of serious vulnerabilities, some applications have a lot of them. One in 10 applications has more than 10 serious vulnerabilities and 4% have more than 50. For these applications, taking measures to reduce their security debt is critical to the health of the software—and the overall security of the organization.
Looking at attack data from users of Contrast Protect, fewer attacks than ever before hit an existing vulnerability in the applications we cover. Less than 0.5% of attacks were viable in January–February, down from 1% to 3% in all the months we have been tracking this data. This means that more than 99.5% of attacks were harmless probes.
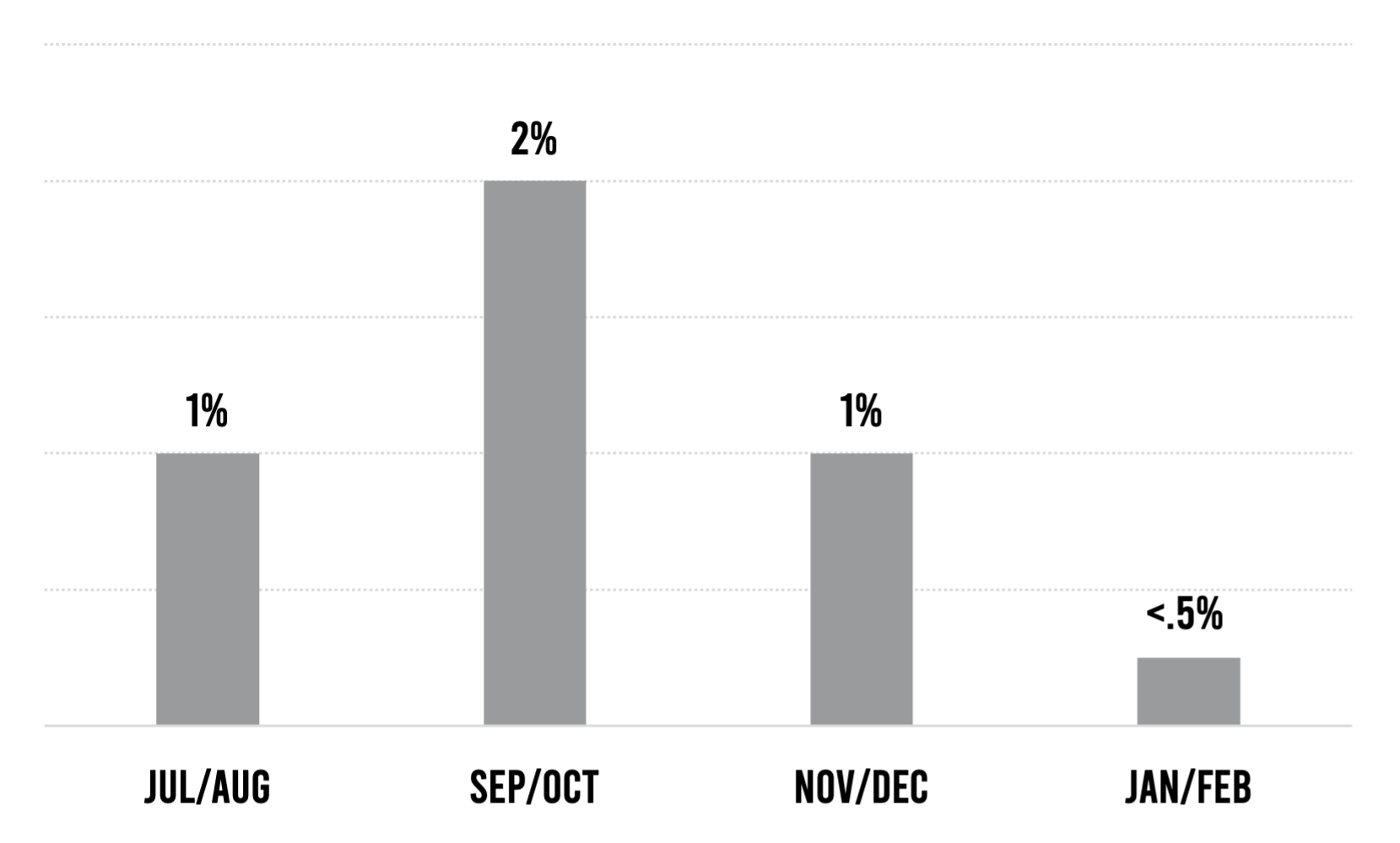
While development and security teams might utter a sigh of relief at this data, that relief is likely to be short-lived. Since the purpose of probes is to identify viable attack options, what bad actors learn from the exceedingly high number of probes they sent in January–February will inform more successful future attacks.
Among viable attacks, two attack types were predominant. Broken access control and SQL injection attacks accounted for 90% of attacks in January–February. These attack types have been in the top two for the past year, and the remainder of the top five have also remained consistent for the past year.
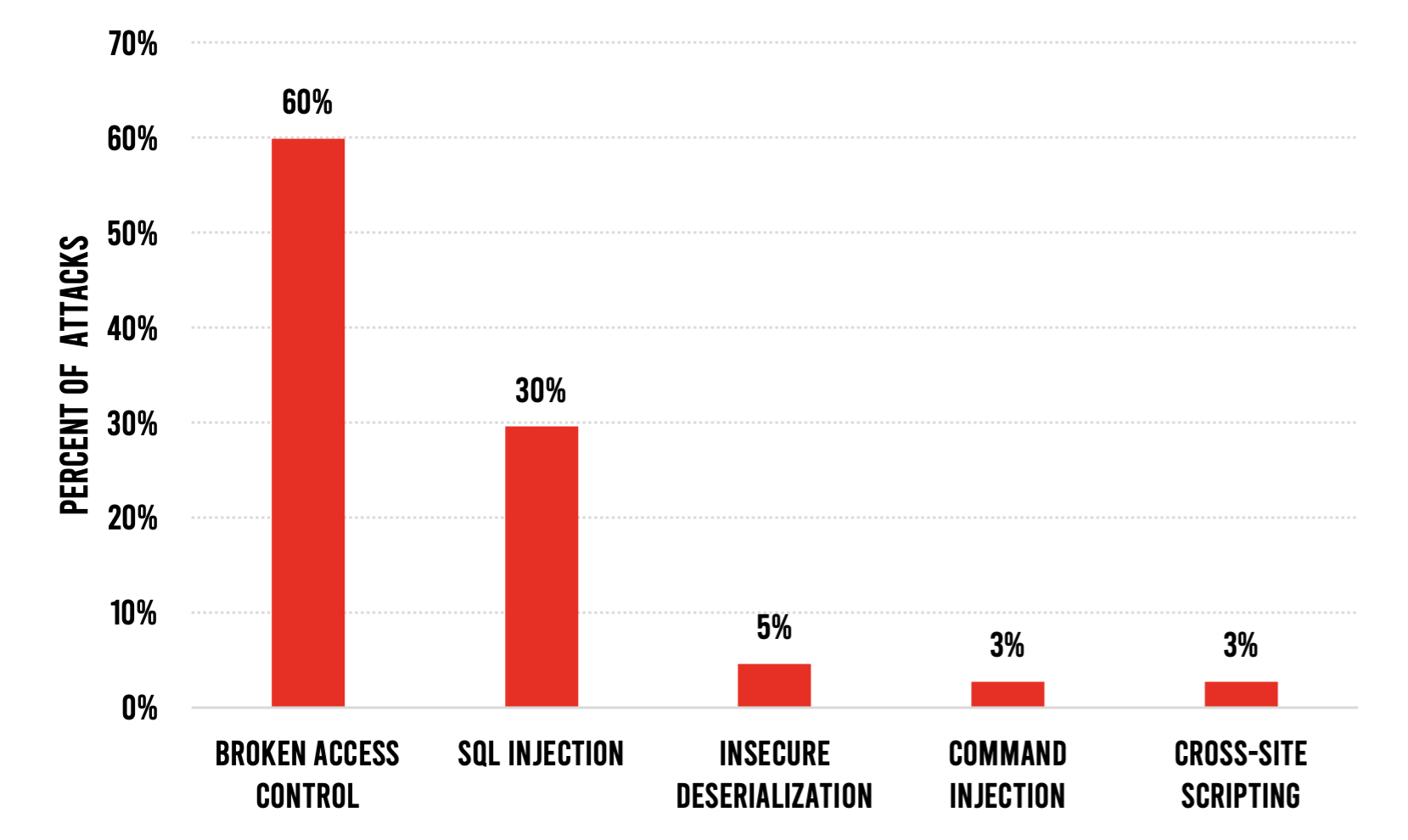
The SolarWinds and Microsoft Exchange attacks have propelled application security into the headlines. And while ethical security researchers work tirelessly to identify vulnerabilities so that off-the-shelf software can be made more secure, they are vastly outnumbered by bad actors who pummel every application with thousands of probes looking for a way to get in. The data analyzed in this report confirms that serious vulnerabilities are still rather commonplace in applications—those in development and those in production.
Fortunately, there is good news on the public policy front. In response to SolarWinds, the Biden administration has signaled that it wants the delivery of secure applications to be a bigger focus for the U.S. government. A forthcoming executive order will set standards for software security and may include a scoring system for the security of off-the-shelf applications.
Picture what such a scoring system would look like if it were mandatory. A security score might be displayed alongside user ratings for every application in a desktop or mobile app store. Published scores for all enterprise software would provide another evaluation criterion in the decision-making process. If such a system were in place, every organization that creates software for customer use would have a huge incentive to make their applications more secure.
Whether such a system is launched or not, legacy application security tools and processes are inadequate for today’s fast-moving and rapidly evolving software factories. When information about vulnerabilities takes days to filter back to the developers who will fix them, they must work through multiple layers of code that have been added since the vulnerability occurred. This creates bottlenecks in the development process and more vulnerabilities that slip into production.
Contrast’s instrumentation approach involves continuous scanning of applications throughout the software development life cycle (SDLC)—and real-time, actionable feedback from those scans that enable remediation on the fly. It enables security professionals to focus on the strategic rather than the tactical, and allows developers to do most remediation without the hassle of involving the security team. It enables security to be one of the outputs of the highly efficient software factory—rather than an impediment to it.
REPORT: January-February 2021 Bimonthly AppSec Intel Report
INSIDE APPSEC PODCAST: Software Supply Chain Is a Priority in the Latest Contrast Security Bimonthly AppSec Intel Report
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.