By David Lindner, Chief Information Security Officer
February 5, 2020
We live in a dynamic economy that is constantly developing new ways to generate revenue. An area that fascinates me are the bug bounty programs such as Atlassian on BugCrowd. Generating tangible rewards from these programs is not an easy undertaking. After years of participating in them, I can attest that the bar is set quite high. It takes time and focus getting your arms around each program and the scope of applications involved.
But what would you say if the bar was lowered—it suddenly was easier and faster to reap returns. Would you participate? Would I have your attention if I told you that I made $600 in 15 minutes using Contrast Community Edition (CE), a free and full-strength application security platform from Contrast Security that provides always-on IAST, RASP, and SCA for Java applications, NET Core, and APIs?
When I started at Contrast Security, I wanted to get my hands dirty with its products to understand how they worked. I picked Contrast CE and ran it against the OWASP Webgoat project, knowing there are plenty of application security vulnerabilities in it. It immediately delivered impressive results—identifying a long list of vulnerabilities. After this initial test, I was determined to run it on a real-world application, and one used by millions of users and with a Bug Bounty program in place. I found the perfect candidate in Atlassian JIRA Server, which we also use internally at Contrast Security.
After downloading Atlassian JIRA Server, I followed the setup instructions, which were very straightforward. JIRA Server launched, and I was up and running:
With the JIRA Server successfully running, I moved to connecting Contrast CE to JIRA Server. Following are the different steps:
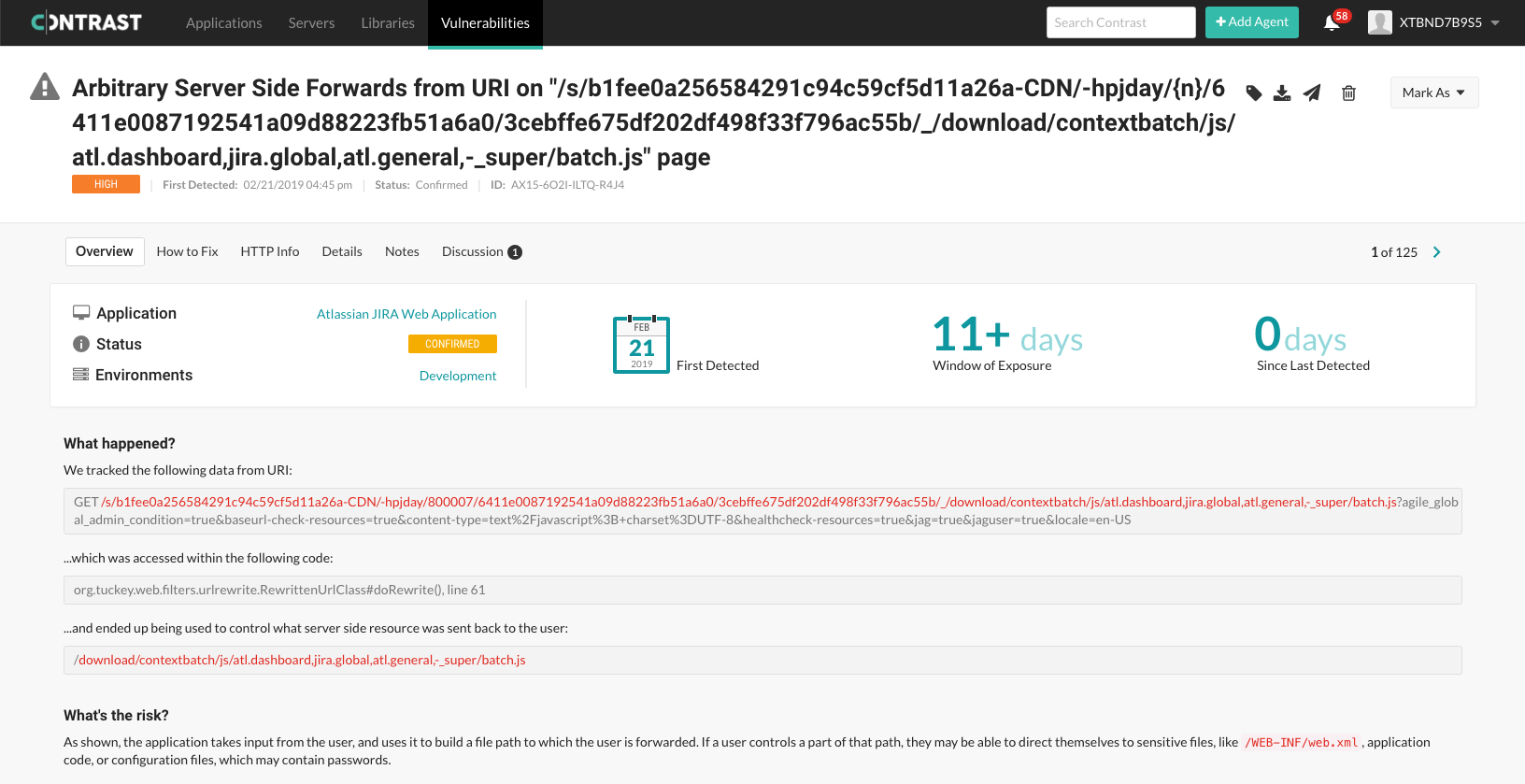
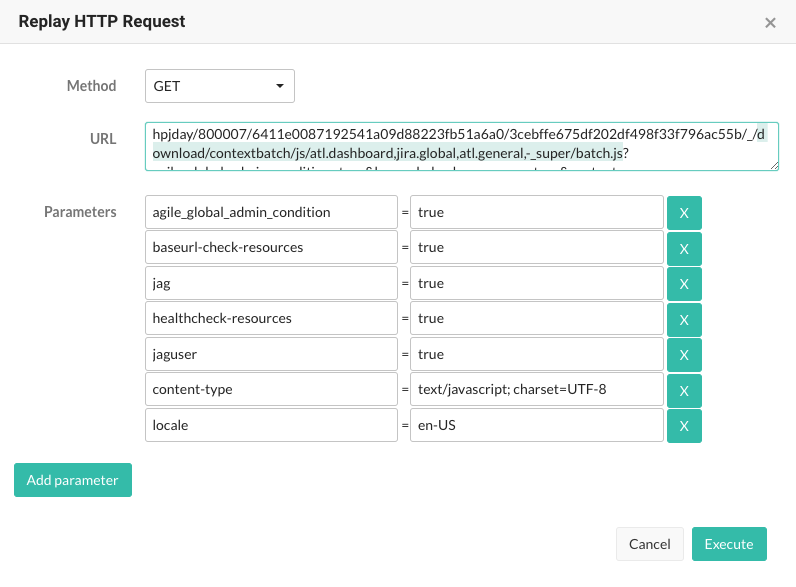
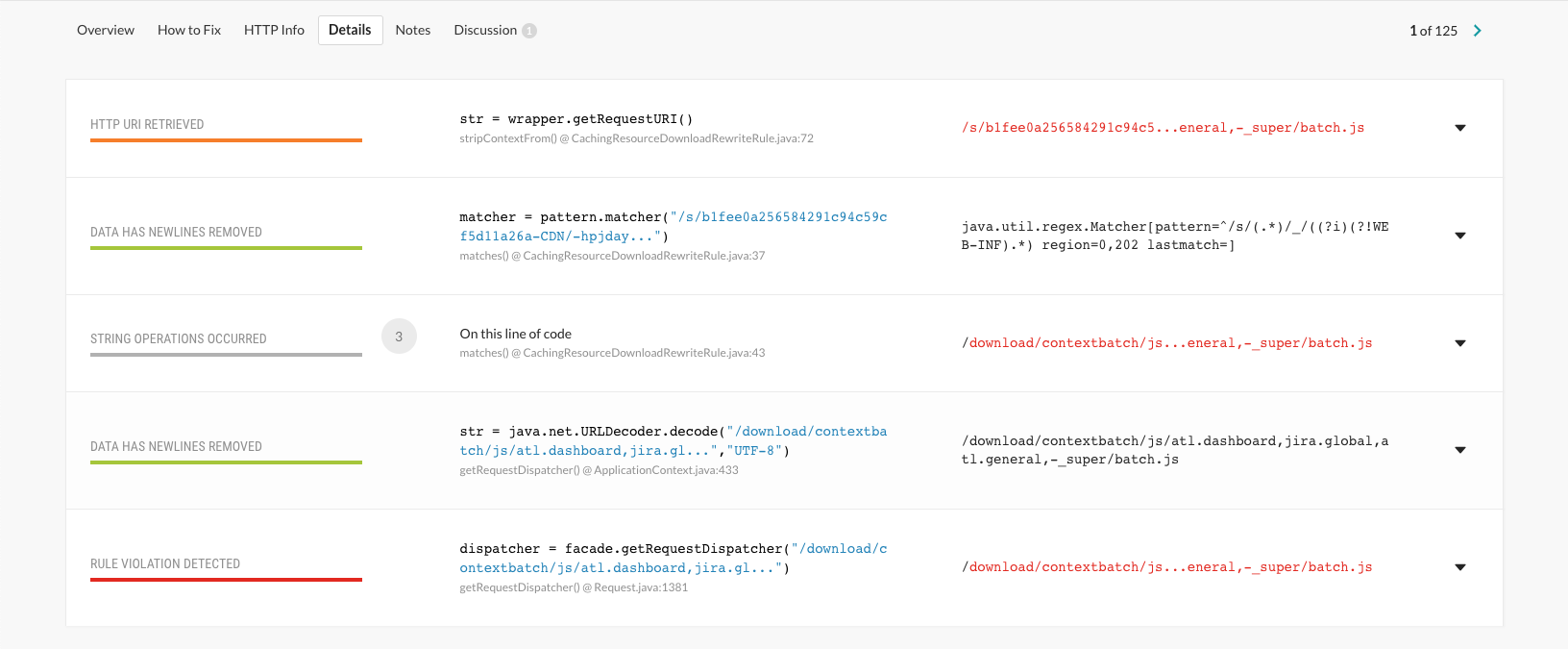
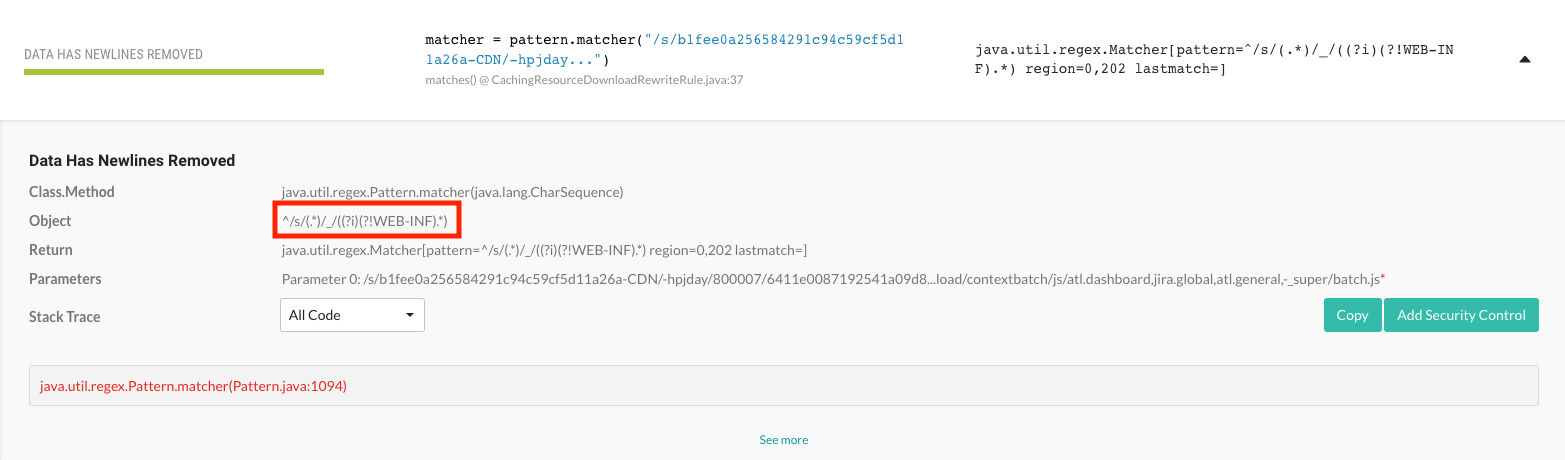
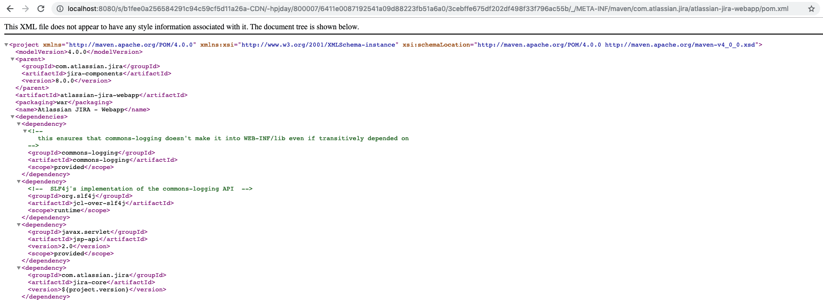
A CVE was also issued for this vulnerability.
One of the most impressive outcomes of the above is that it took me around 15 minutes to complete these tasks. What a great value proposition for anyone looking to make some extra dollars—using a free tool—via bug bounty programs. Download a free copy of Contrast CE to get started today.

David is an experienced application security professional with over 20 years in cybersecurity. In addition to serving as the chief information security officer, David leads the Contrast Labs team that is focused on analyzing threat intelligence to help enterprise clients develop more proactive approaches to their application security programs. Throughout his career, David has worked within multiple disciplines in the security field—from application development, to network architecture design and support, to IT security and consulting, to security training, to application security. Over the past decade, David has specialized in all things related to mobile applications and securing them. He has worked with many clients across industry sectors, including financial, government, automobile, healthcare, and retail. David is an active participant in numerous bug bounty programs.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.