
Businesses under 1000 employees were breached 4 times more often than large organizations and faced double the breach risk from vulnerability exploits, according to the 2025 Verizon Data Breach Investigations Report. This disproportionate targeting occurs precisely when security teams often manage broad responsibilities with carefully allocated resources, making effective defense challenging. For these businesses, a successful breach isn't just an operational setback; it can trigger crippling financial penalties, legal liabilities and a loss of customer trust that threatens their very existence.
A primary reason for this breach risk lies in the "application blindspot." While firewalls monitor networks and endpoint detection watches processes, the complex interactions within running applications and APIs often remain opaque to traditional security tools. Attackers exploit this visibility gap to target business logic and internal flaws. This lack of runtime insight allows threats to dwell undetected, leading to potentially severe consequences like data theft, operational disruption and erosion of customer trust — impacts that can derail a growing company and, in some cases, prove unrecoverable. Addressing this blindspot is a critical security imperative, especially when the financial and operational stakes are so high.
Security functions within midsize businesses face a unique convergence of challenges when securing applications:
While necessary, the tools commonly monitored by security teams provide an incomplete picture:
These tools leave security teams guessing when faced with inevitable application incidents, forcing time-consuming manual correlation and often requiring slow, inefficient handoffs to security partners and development teams for investigation.
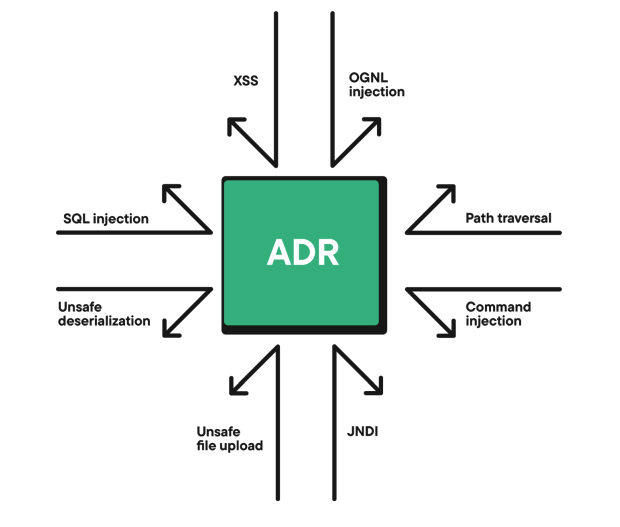
Contrast Application Detection and Response (ADR) provides visibility and control where lean security teams need it most: directly within running applications and APIs. By instrumenting applications in runtime, ADR observes actual code execution and data flow, eliminating the guesswork required with external tools. This integrated approach allows ADR to deliver accurate alerts, precise context for faster triage and response and reliable threat blocking – significantly reducing noise and the need for expert expertise.
Key benefits for security teams include:
Effective application and API protection
Empower security teams
Accelerate threat response
ADR acts as a critical last line of defense when other tools miss the threat, helping to prevent breaches that could incur devastating regulatory fines, legal costs, and reputational damage from which an SMB may not recover. It’s not just better alerts; it’s protection against existential threats.
Contrast Security’s platform utilizes threat sensors inside each application. This provides continuous, real-time monitoring, detection and protection purpose-built for the complexities of modern application architectures. Contrast ADR integrates seamlessly with the tools security teams already use — such as SIEMs or IT ticketing systems — ensuring actionable intelligence flows into existing workflows and enhances current security investments.
For an SMB, operating with an application security blindspot isn't just a risk; it's an invitation for potentially catastrophic consequences. Relying solely on traditional monitoring tools leaves critical applications vulnerable, and the financial and legal fallout of a breach can be insurmountable. Contrast ADR empowers lean security teams — whether internal or outsourced — to overcome resource limitations and the AppSec skills gap. By providing unparalleled runtime visibility, actionable context, and real-time protection from within the application, Contrast ADR acts as essential 'insurance' against these threats. It enables teams to defend their application and API, significantly reduce the risk of business-ending incidents, and focus confidently on innovation and scaling, knowing they have a robust protection where most breaches start.
Schedule a demo and see how to eliminate your application-layer blind spots.
Book a demo
