By David Lindner, Chief Information Security Officer
September 23, 2021
The primary goal of the OWASP Top Ten has always been to drive awareness of the biggest application security risks out there, and thereby establish a “floor” or minimum standard for application security efforts at an organization. The newly released 2021 OWASP Top Ten has done a fantastic job of communicating the breadth and depth of the problems we face today. It is based on thousands of hours of hard work by the OWASP Top Ten leadership and others—including an analysis of telemetry data that is unprecedented in size and scope and one of the biggest industry surveys on the topic ever conducted.
Research results for the 2021 OWASP Top Ten.
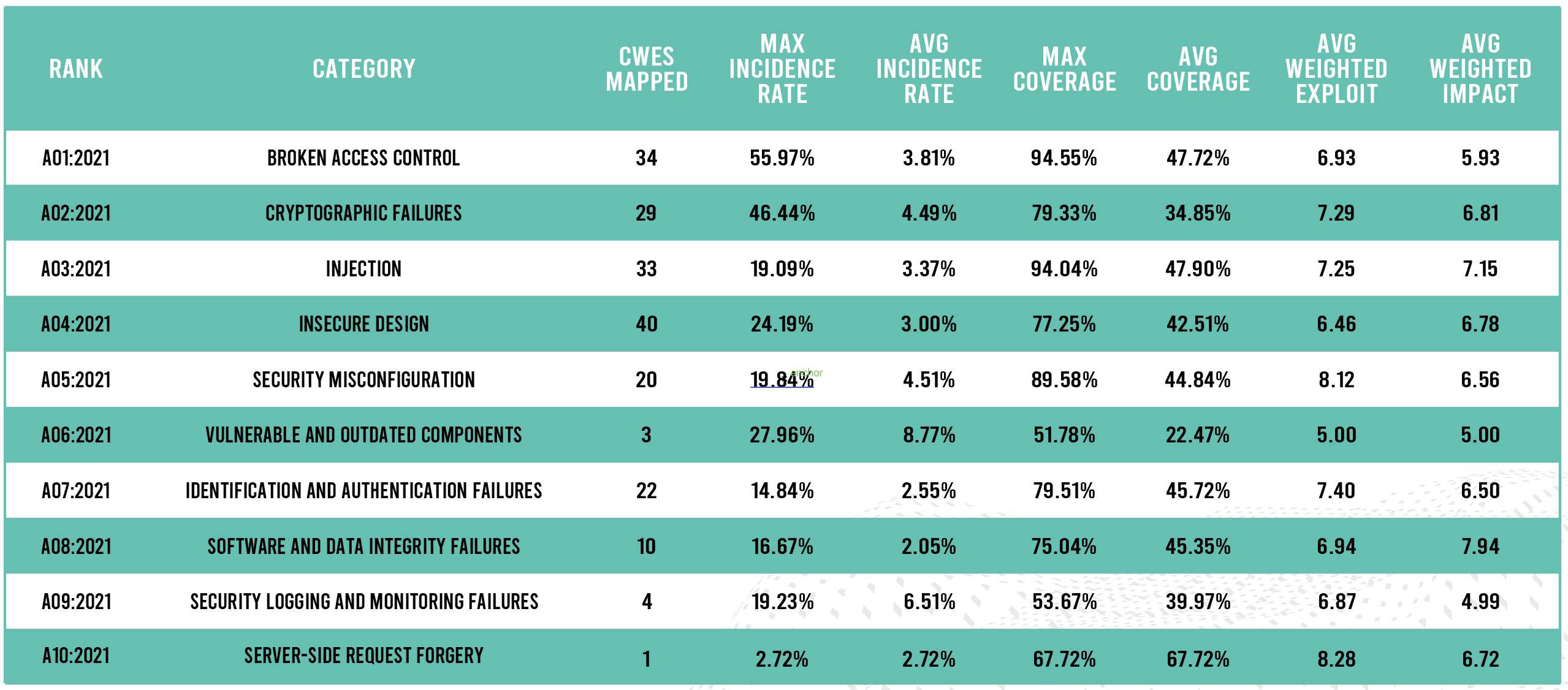
The team’s comprehensive data analysis included far more Common Weakness Enumerations (CWEs) than ever before, and the result is that many more of them are a part of the Top Ten—nearly 200 in total. But OWASP’s achievement in the 2021 Top Ten goes beyond its ability to fit more CWEs into 10 bullets. Rather, this more comprehensive analysis of the data has resulted in something I have been advocating for years: less emphasis on individual vulnerabilities and more emphasis on broad security control areas.
This broader focus will positively impact the security of applications over time, especially for organizations for which the OWASP Top Ten is a primary compliance metric for application security. Rather than seeing specific vulnerabilities as checkboxes that need to be fulfilled, organizations will be motivated to do the broader, more structural work of preventing classes of vulnerabilities.
Injection vulnerabilities are a classic example of this. There are 33 CWEs associated with this category in the 2021 Top Ten, including well-known ones like SQL, NoSQL, LDAP, and Expression Language (EL). Most of these were consolidated in 2017, but Cross-Site Scripting (XSS) was added to the category for 2021—a move that I fully support, because it is unquestionably a type of injection. Hopefully, the consolidated category will incentivize organizations to formulate a strategy to avoid all vulnerabilities that involve injection by looking at application architecture and core development practices.
Another example is Broken Access Control, which moved to number one on the 2021 OWASP Top Ten. We concur with this change, as Broken Access Control is at the top of our RiskScore Index™. In my mind, Broken Access Control should have been number one all along; the potential impact of a breach is substantial and moreover it is one of the hardest things for organizations to get right—especially after the fact. And security tools have fallen really short in finding and making a dent in these issues.
The difficulty in getting things right after the fact is behind a new category in the 2021 OWASP Top Ten, which debuted high on the list, at number 4. The Insecure Design category reflects how the Top Ten overall is moving in a more strategic direction as opposed to tactical. It is a recognition that an application’s underlying architecture must be built with core security principles in mind from the very beginning of the design process.
This is the ultimate example of “shifting left.” Most organizations will talk a good game about how they want to shift left with their application security efforts, identifying and remediating vulnerabilities earlier in the development process. But few shift further left than the first line of code! Regardless, the architectural design of an application plays a significant role in how secure the software is when it goes into production.
As OWASP points out, secure design is both a culture and a methodology that places security prominently in the way software is architected. Secure design is all about prevention rather than remediation. Indeed, we all know that, when possible, prevention is a superior way to protect our physical health compared with treating an illness after it occurs. The same is true for software. If software is created in a more secure way up front, this helps organizations avoid extremely costly mistakes where the needed security controls were never defined.
Moreover, as Contrast’s CTO and Co-founder Jeff Williams notes, the Insecure Design category is a wake-up call for organizations to do what they should have been doing for years: threat modeling. Very few organizations do threat modeling even today, and this is not surprising as it is a hard skill to build—and in many ways can be more difficult than penetration testing.
How can an organization launch a threat modeling program? To begin, break down an application’s architecture and talk about security control areas. The Flow Map feature in Contrast Assess shows the architecture of an application in a visual format, including components, where the connections are, what back-end databases are involved, and so forth. Such a visualization can get the conversation moving when it comes to threat modeling.
Of course, the 2021 Top Ten goes beyond Injection, Broken Access Control, and Insecure Design. Two additional categories are new for this year’s edition. Software and Data Integrity Failures debuts at number 8. While software integrity and data integrity are largely unrelated problems, they both present risk to organizations. And several high-profile software integrity failures have occurred over the past year, including the attacks on SolarWinds and Kaseya. Server-Side Request Forgery (SSRF) is another new category, and unlike the other categories, it includes just a single CWE. Many readers have seen this issue at their organizations, and the data behind it came from both the telemetry data and the industry survey.
A number of 2017 categories were combined, rearranged, and renamed as well. Sensitive Data Exposure was renamed Cryptographic Failures, Broken Authentication was renamed Identification and Authentication Failures due to the addition of identification issues, and the Security Misconfiguration category was expanded to include XML External Entities (XXE). The problem of using outdated open-source libraries was combined with open-source vulnerabilities to create the Vulnerable and Outdated Components category.
If I had been asked to create the categories for the OWASP Top Ten, I might have organized them somewhat differently. Nevertheless, the biggest application security risks are all found somewhere in the Top Ten, and it does not matter how each vulnerability is categorized and ranked, because every organization needs to protect against all elements of the Top Ten. As I have said, what is important is that everyone focuses on the broader security control areas. Doing this will take care of each individual CWE.
Organizations that take the 2021 OWASP Top Ten seriously will build new applications securely. At the same time, they will harden their existing applications from vulnerabilities and corresponding attacks. That said, the task of applying the Top Ten to current applications will be easier said than done in some cases. For example, applications with underlying structural problems may require developers to peel back multiple layers of custom code, not to mention open-source libraries and frameworks, to get to the root of the problem.
It reminds me of a personal story from a decade ago. I was consulting with a very large enterprise that had experienced intrusions in a business-critical application. As I reviewed the steps they would need to take to retroactively make their application sufficiently secure, they realized that the effort would be extremely costly in terms of both time and money. They ultimately concluded that it would be less expensive and disruptive to rebuild the application from scratch, using a newer programming language and newer technology. I have not connected with that company in some time but guarantee they are in a much better place today for having made that decision.
Both DevOps and application security are in a better place in 2021 than a decade ago, and I do not expect many organizations to make a similar decision today. But that does not mean that coverage for the OWASP Top Ten will not be costly in some cases. One CIO recently told me that it was going to cost $50 million for his team to upgrade the Apache Struts framework across the company’s application portfolio. If that is the cost of moving to a new version of a third-party framework, what would it cost to repair security gaps in the underlying design of a thousand applications?
The OWASP Top Ten team has done a fabulous job of identifying and describing the application security risks that require the most attention in 2021. For organizations that do not have an application security program, this is where they should start in building one. Those that have ongoing application security efforts should consider the OWASP Top Ten as the baseline for the threat modeling efforts they need to implement if they have not already done so.
ADDITIONAL RESOURCES
WEBINAR: OWASP Co-founders Discuss the OWASP Top 10 2021
PODCAST: Key Takeaways and AppSec Recommendations From the 2021 OWASP Top Ten
BLOG POST: The Forthcoming 2021 OWASP Top Ten Shows That Threat Modeling Is No Longer Optional
BLOG POST: Behind-the-Scenes Observations on the 2021 OWASP Top Ten

David is an experienced application security professional with over 20 years in cybersecurity. In addition to serving as the chief information security officer, David leads the Contrast Labs team that is focused on analyzing threat intelligence to help enterprise clients develop more proactive approaches to their application security programs. Throughout his career, David has worked within multiple disciplines in the security field—from application development, to network architecture design and support, to IT security and consulting, to security training, to application security. Over the past decade, David has specialized in all things related to mobile applications and securing them. He has worked with many clients across industry sectors, including financial, government, automobile, healthcare, and retail. David is an active participant in numerous bug bounty programs.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.