As part of an overall digital transformation, organizations have quickly been moving toward Open Source Software adoption to get software to market faster and gain a competitive edge in today’s face paced business environment. Open Source Software components have become the fundamental building blocks of modern application software development to help improve efficiency.
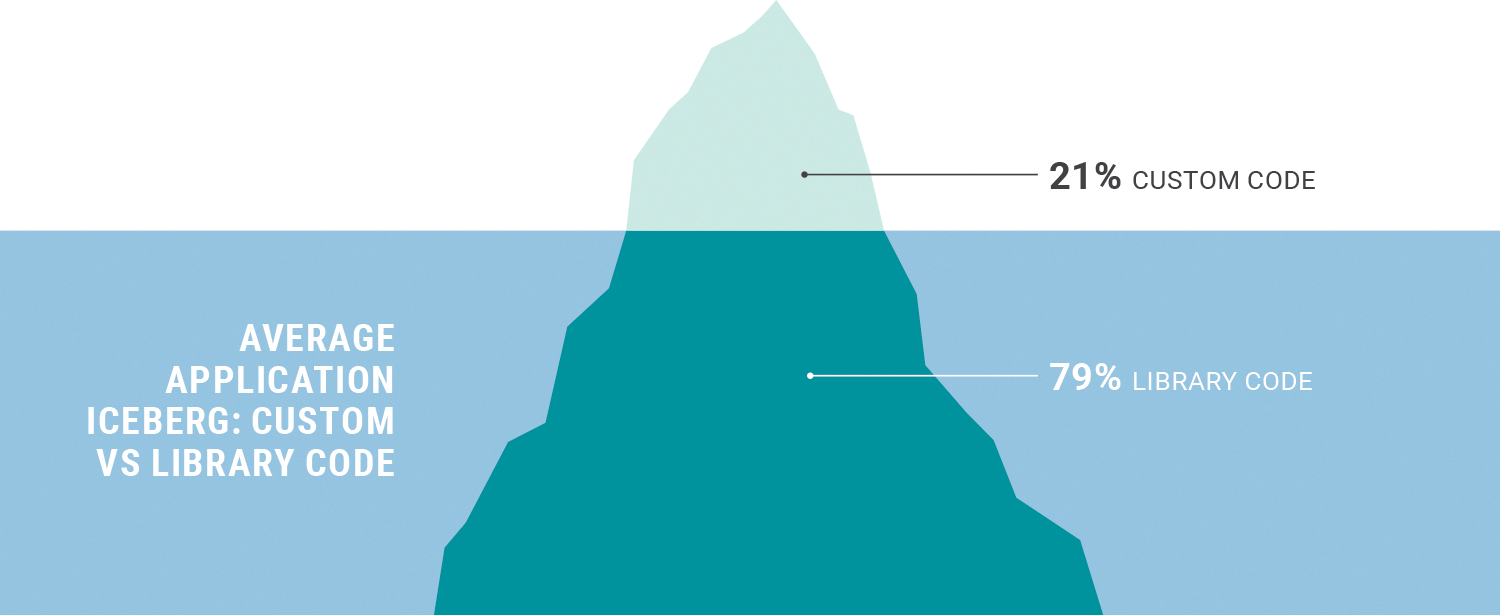
Open Source Software puts code directly into the hands of developers as the fundamental building blocks of modern application software development. It provides developers with a plethora of off-the-shelf components that can be modified, reused, enhanced and re-distributed. Developers have continued to rely on Open Source Software components to work more efficiently as they develop code and release rapidly. As a direct result, companies that have adopted Open Source Software experience significant gains. It should therefore not be surprising that Open Source Software, libraries and frameworks account for ~80% of the source code in modern web applications. This makes open source security more important then ever before.
Attackers are aware of these trends as well, and applications that use open source code are now a primary target for cybercriminals due to the leverage that vulnerabilities in third-party software provide them. Consequently, all software elements need to be actively managed and monitored to identify vulnerabilities and to eliminate the risks they pose.
Unfortunately, the visibility and effective management of Open Source Software has not kept pace with the increase in its use. And, legacy application security tools (SAST and DAST) used for traditional waterfall-based development do not translate well into modern high-velocity Agile / DevOps environments. Security teams need to be able to quickly and effectively respond to application security threats, and prioritize and remediate in real-time. New innovative and automated approaches to implement and manage Open Source Software are required - automated solutions that quickly and effectively identify, mitigate, and remediate software vulnerabilities wherever they reside, including libraries, frameworks and custom code.
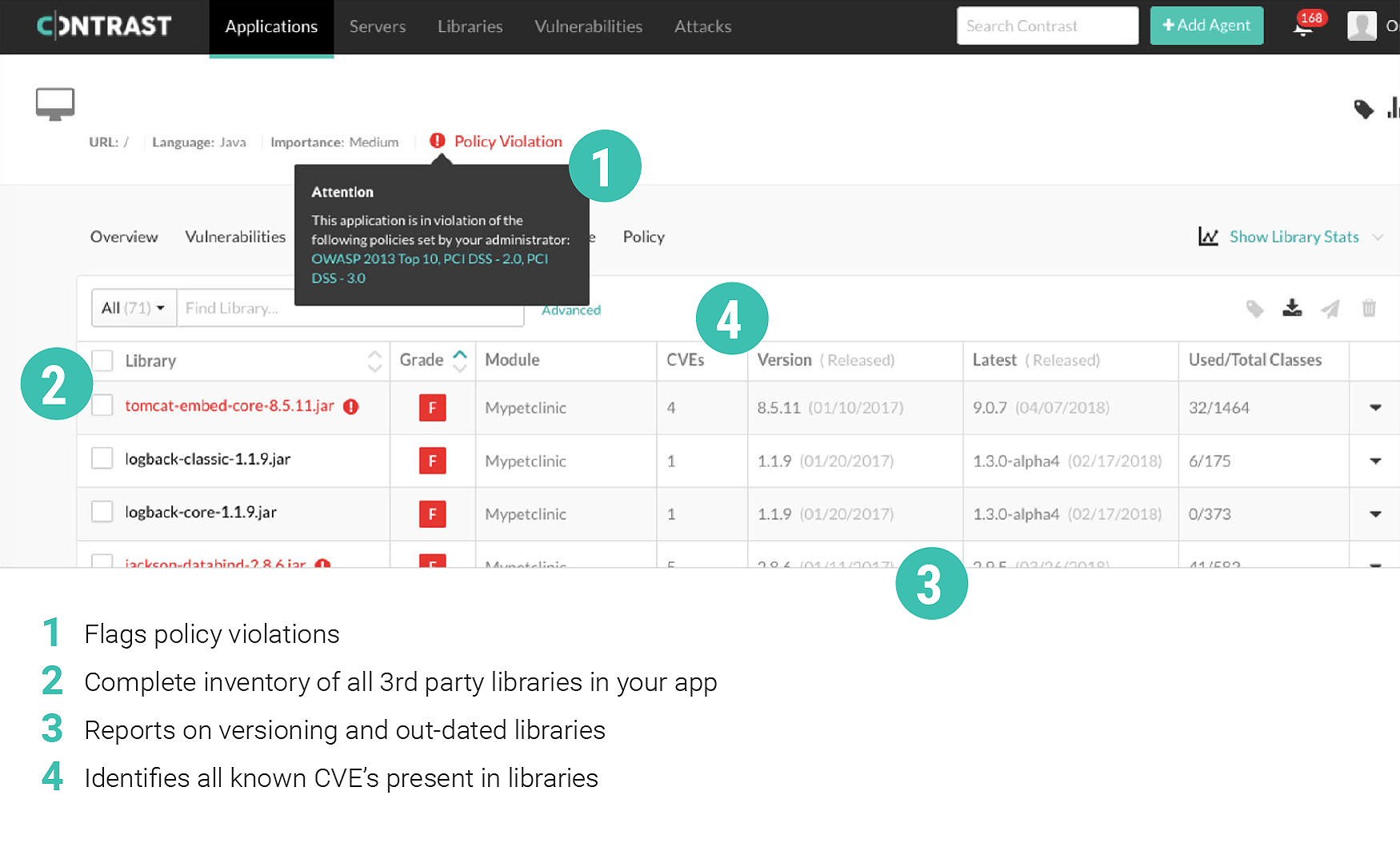
Contrast Security is uniquely positioned to identify and mitigate Open Source Software vulnerabilities & risks and deliver application software security solutions at scale and low cost. To find out how, we invite you to download the free solution brief, "Securing Your Open Source Software Applications".
About Contrast Security:
Contrast Security is the world’s leading provider of security technology that enables software applications to protect themselves against cyberattacks, heralding the new era of self-protecting software. Contrast's patented deep security instrumentation is the breakthrough technology that enables highly accurate assessment and always-on protection of an entire application portfolio, without disruptive scanning or expensive security experts. Only Contrast has sensors that work actively inside applications to uncover vulnerabilities, prevent data breaches, and secure the entire enterprise from development, to operations, to production. More information can be found at www.contrastsecurity.com or by following Contrast on Twitter at @ContrastSec.