Optimize Resources with Automated Penetration Testing
Save valuable financial and people resources and minimize time-to-remediate with Contrast automated penetration testing.
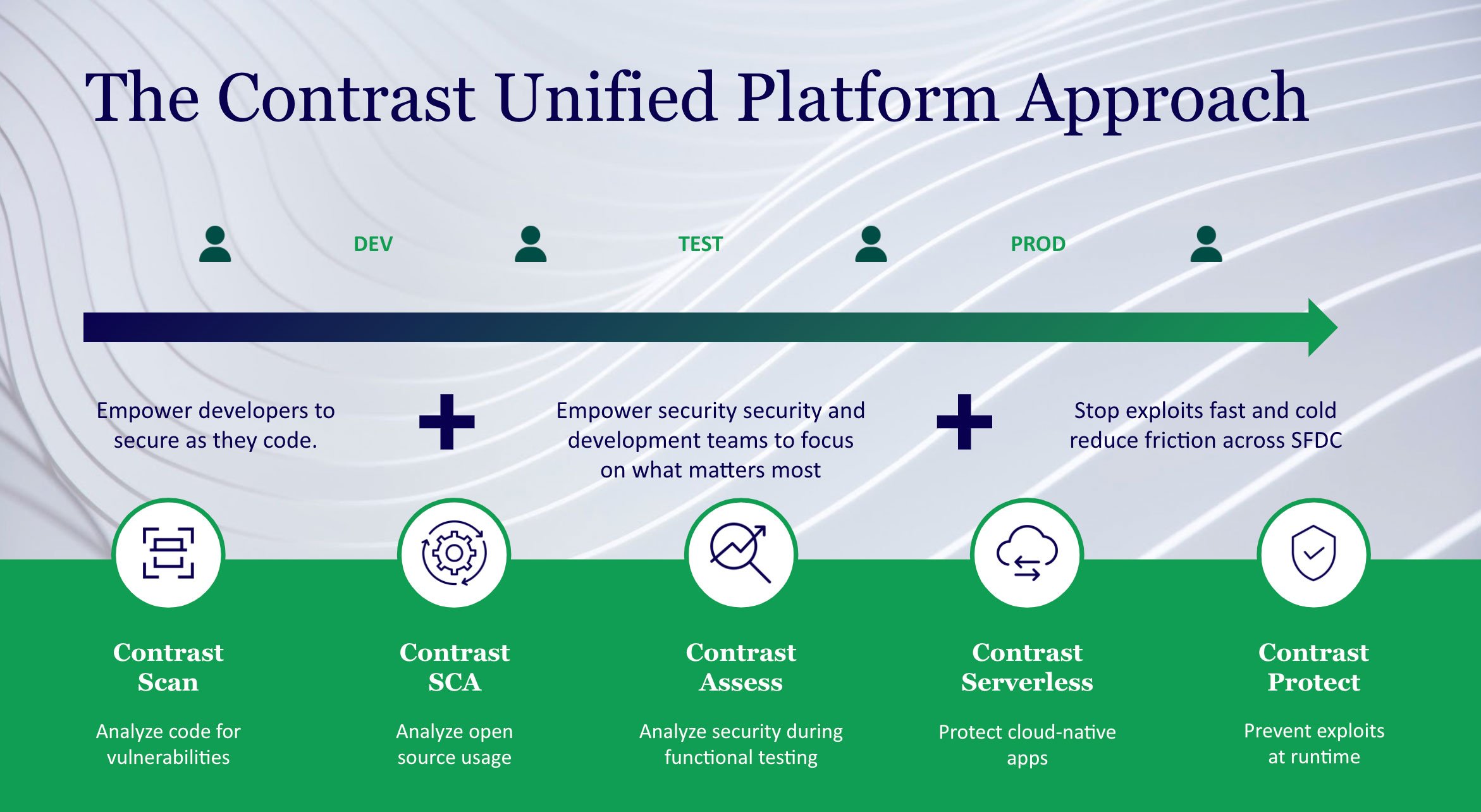
Automated Penetration Testing
The Contrast Secure Code Platform automates the penetration testing process, enabling penetration testers to focus on more complex vulnerabilities that require more detailed review.
Who Needs Automated Pen Testing?

CISOs
CISOs that are cost conscious and need to “do more with less” with regards to the Security staff they have on hand. Automated pen testing is less costly than manual pen testing.

AppSec
Application security teams who need to provide layered security without impeding development timelines. Automated pen testing is faster than manual pen testing.

DevOps
DevOps teams that need application security to reduce the number of false positives and actionable remediation guidance. Automated pen testing is more efficient.

Red Teams
"Red teams" that would benefit from a detailed “roadmap” of highlighted vulnerabilities that exist in the applications. Automated pen testing is more advanced than a vulnerability scan.
The Automated Security Testing Solution is Here
Experience Contrast Today
Schedule a one-to-one demo to see what the Contrast Secure Code Platform could do for you.
Why Automated Pen Testing?
Save Valuable Resources
Contrast automates penetration testing across the development lifecycle, allowing Security teams to focus on remediation rather than manually pen testing.
Minimize MTTR
Contrast drastically cuts security debt by embedding within native developer pipelines and providing actionable remediation guidance.
Pinpoint Accuracy
Contrast’s industry leading accuracy means less time manually triaging false positives from pen-testing reports.
With Contrast Assess we had an average of 7% of false positives against the 57% in the pen-test reports received from our customers.
Jose Oca
Lead Quality Manager
Get in Touch
See how the Contrast Secure Code Platform can help automate application security testing at scale.






