Leading Companies Trust Contrast
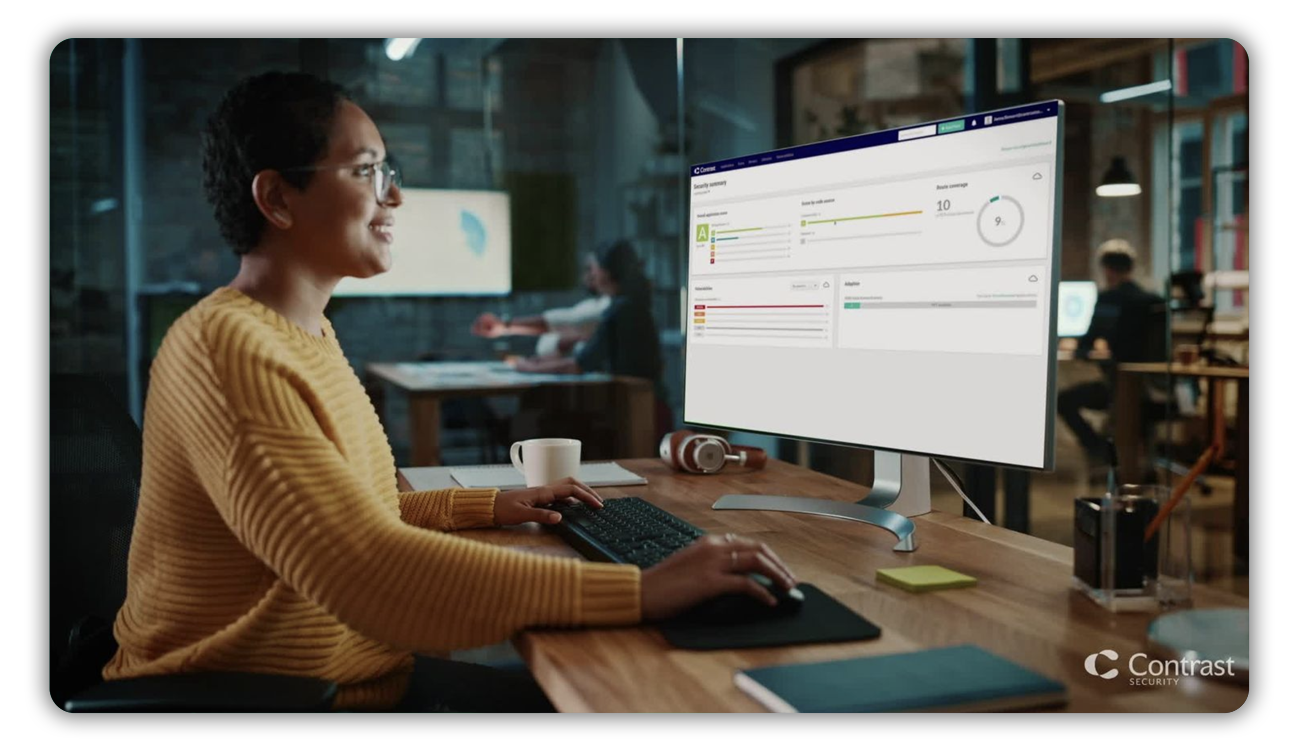
Contrast helps today’s software-driven companies get secure code moving.
Built for Developers. Trusted by Security.




A can't miss report based on real-world data from thousands of applications that highlights vulnerability and attack trends, security debt, benchmarks on the vulnerability escape rate, and much more.

Significantly Reduces False Positives And Speeds Devops Cycles With Contrast Application Security Platform.

Watch this customer case study video to learn how Contrast helped BMW shift left their DevOps

IDC study shows that businesses could achieve at least a 92% reduction in known security vulnerabilities across their major business applications by using Contrast Security.

In a recent video at the RSA Conference, Kiran Sharma, Senior Privacy Program Manager at Snap Finance, highlighted the significant impact of Contrast’s platform on their security initiatives.
The platform enables both security and development teams to work more rapidly in a way that enhances both teams' experiences. The most important piece of this is removing the vast majority of false positives out of the equation while moving at speeds that can keep up with Agile/DevSecOps practices. As the number of developers and development teams continue to grow exponentially our security team has not. This enables us to scale with the increasing development activities without significant team size changes. Because it feeds the information directly into development's hands (Jira, Slack, IDE, etc.) much of the burden is lifted off of the security teams while also keeping development teams happy by not filling the backlogs with false positives. Also since the entire platform is API accessible you can customize the data / platform to meet your companies' unique needs.
Cyber Defense Specialist,
Gartner Peer Insights

CUSTOMER SPOTLIGHT
How an American Financial Technology Company Embeds Application Security
In this customer spotlight session, our co-founder and CTO Jeff Williams sat down with an American financial technology company to discuss the importance of embedding application security, implementing run time protection, and shifting left in the development process. Learn how these strategies can help organizations stay ahead of evolving security threats and keep their applications safe.
Experience Contrast Today
Schedule a one-to-one demo to see what the Contrast Secure Code Platform could do for you.
Leading brands around the world rely on Contrast
Built for developers and trusted by security to secure their code through the entire development pipeline and continuously protect across the complete software lifecycle.







































CUSTOMER SPOTLIGHT
IDC Business Value Case Study: Floor & Decor
IDC study shows that businesses could achieve at least a 92% reduction in known security vulnerabilities across their major business applications by using Contrast Security.
Contrast Security - Replace the old way of doing Application Security" -This will most likely replace the old way of doing things, which is running a boring and long scan. Developers/engineers don't like going to "another" dashboard to view the results of their scan, so Contrast does a great job of taking care of this extra work for users."

Security with DevOps in mind - Contrast Assess provides a clean and intuitive UI for viewing your organization's overall security posture while giving developers continuous real-time vulnerability details for their custom code and libraries, as well as how-to-fix remediation advice. No more packaging and uploading of code or outdated point-in-time scans. Great for letting you know what application routes are vulnerable or those that still need testing. If your app is running, Contrast is testing it.”
Application Security Testing at scale - The tool helps find high-quality security vulnerabilities at the speed of DevOps. "Fail fast, fail often" at the requirement of daily changes to the application landscape. Traditional SAST and DAST tools struggle to keep up with the rate of change and cause more noise than acceptable. Contrast Security helped us reach our goal of coverage without the hassle of the terrible signal-to-noise ratio common to other application security tools."

An easy, fast way to improve your code security and health - The effectiveness of the solution’s automation via its instrumentation methodology is very effective and was a very easy integration. The solution has absolutely helped developers incorporate security elements while they are writing code."

Great security product - Great vendor to work with. We use a combination of their IAST and RASP tooling and for most part are very happy with the solution. There are some areas that I wish it was a bit more robust, such as a better support for container-based applications and feature parity across all supported languages."
ecause they're (Developers) not waiting on security to complete scans for them, Dev teams are not seeing delays in deployment. This has changed the way that developers are looking at usage of third-party libraries, upfront. It's changing our model of development and our culture of development to ensure that there is more thought being put into the usage of third-party libraries."

Customer Success the Contrast Way
Learn more about Contrast's best-in-class customer experience through strategic planning, training, enablement, support and services.