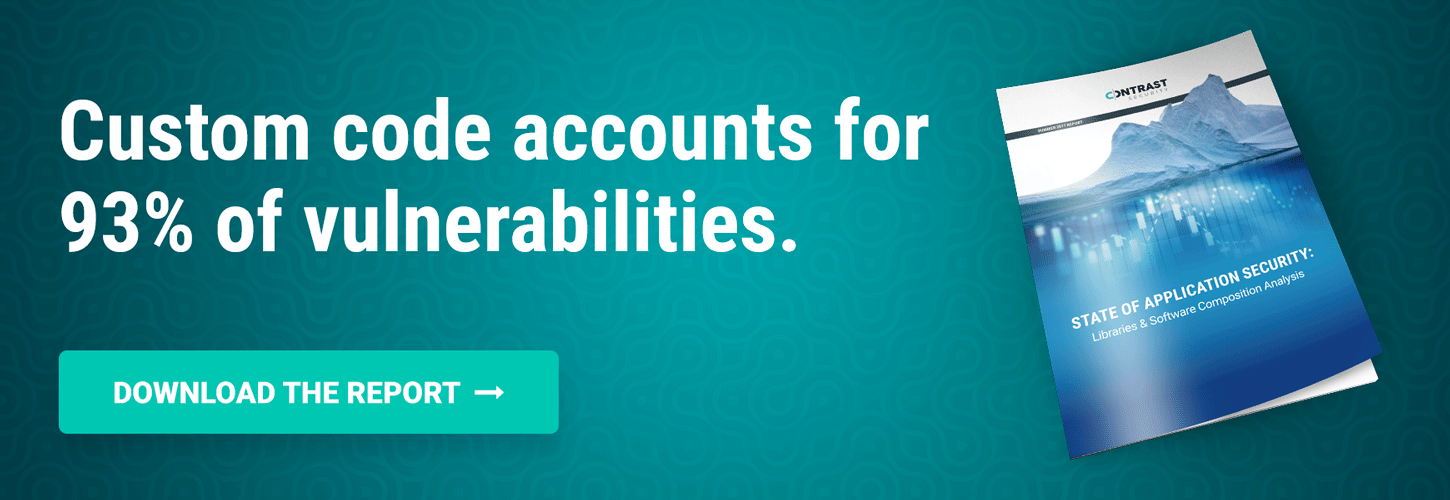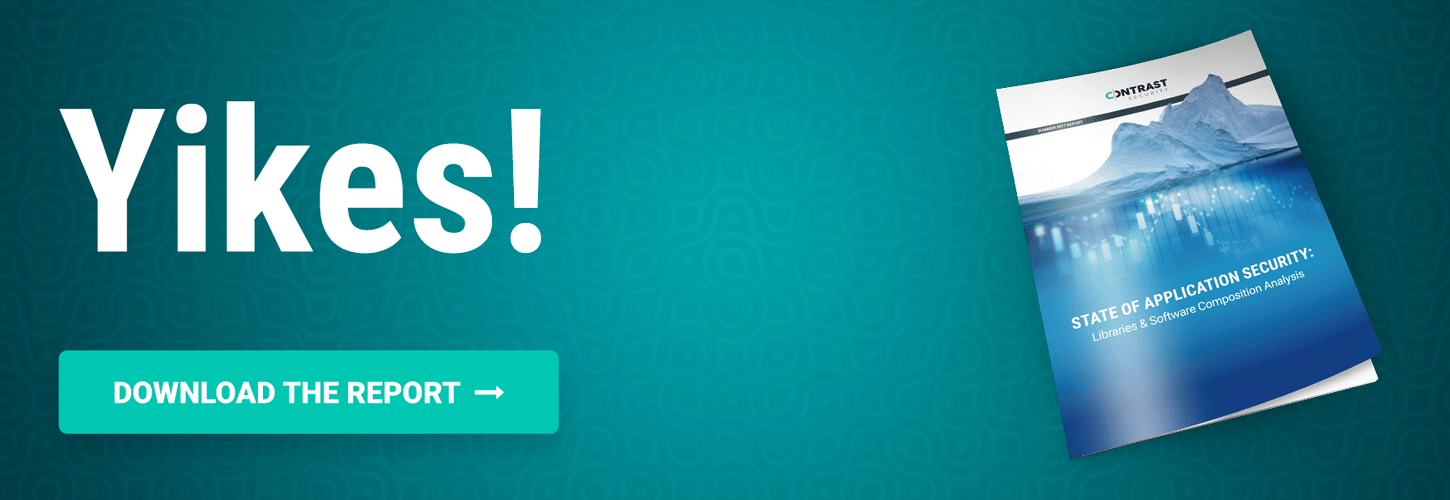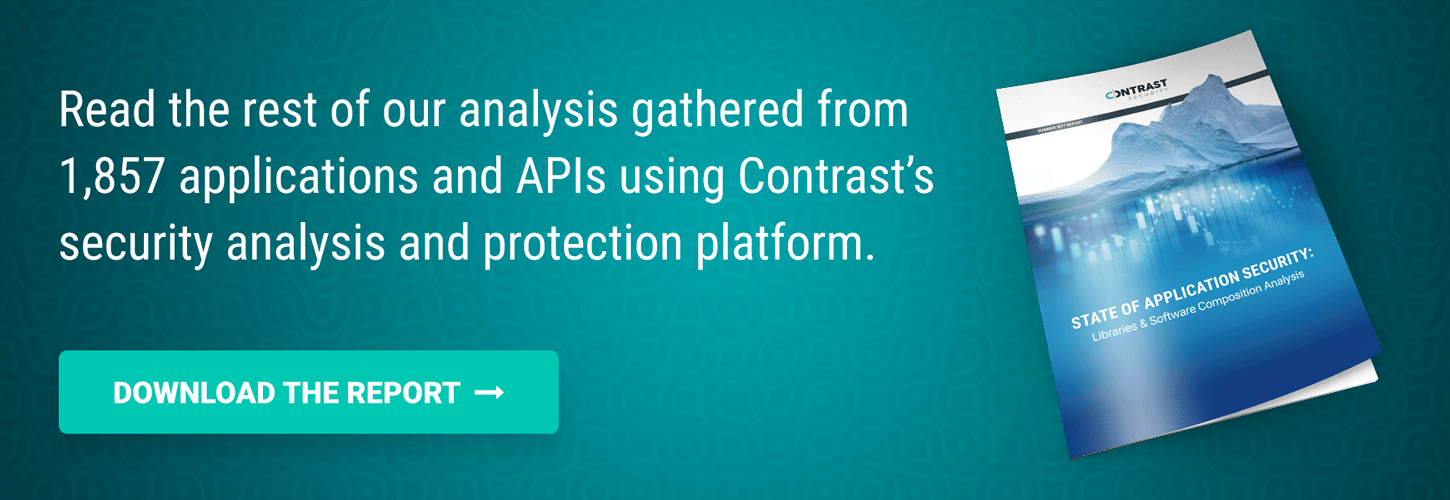
As we mentioned last week, Equifax continues to make headlines and ramifications of building sites with insecure code is taking a its toll. Below you'll read a series of startling comments that appeared this past week by Jeff Williams, Contrast Security Co-Founder and CTO. According to Jeff, the source of the attack was a 3rd-party library called Fireclick, which accesses yet another site, netflame.cc, to pull in javascript. To learn more about the security of third party libraries (and the security of your own code) you may want to read this whitepaper: State of Application Security: Libraries & Software Composition Analysis.
“Many websites include javascript from third parties for a variety of purposes, including analytics, ads, styling, and many other webpage features. Equifax included this Fireclick library on their own website, but it pulls in some javascript from another site, netflame.cc, that appears to have been hacked. When the Equifax site loads Fireclick, which loads netflame.cc code, the victim’s browser is redirected to malware,” explained Jeff Williams, CTO and co-founder of Contrast Security.
“Anyone using the Fireclick library may have been affected, and the attackers may not even know that they compromised Equifax. A more targeted attack could have used the netflame.cc code to access victim’s data from the Equifax page, submit false data on behalf of the victim, or deface the Equifax page. The attack could have been made invisible to the victim and could have been much more difficult to detect,” Williams added.
Everyone uses third-party code, said Jeff Williams, chief technology officer and co-founder of Contrast Security. However, he said in a statement, doing so “creates an obligation to analyze for vulnerabilities continuously and respond to new vulnerabilities/attacks within hours.”
Jeff Williams, co-founder of Contrast Security, linked the latest hack to third-party software used by Equifax called Fireclick. "Basically, a very similar problem with two quite different pieces of code," he said. "Anyone using the Fireclick library may have been affected, and the attackers may not even know that they compromised Equifax," Williams added.
The newest incident "happened because Equifax trusted a different piece of third-party code (Fireclick Web Analytics javascript library) and didn't put in the work to make sure it stayed secure,” said Jeff Williams, CTO and co-founder of Contrast Security. “Basically, a very similar problem [to the first breach] with two quite different pieces of code.”
The Fireclick library was included on the Equifax site, “but it pulls in some javascript from another site, netflame.cc, that appears to have been hacked,” said Williams. “When the Equifax site loads Fireclick, which loads netflame.cc code, the victim's browser is redirected to malware.”
Anyone that uses the Fireclick library could feel the impact of the second breach, but “the attackers may not even know that they compromised Equifax,” he said. “A more targeted attack could have used the netflame.cc code to access victim's data from the Equifax page, submit false data on behalf of the victim, or deface the Equifax page.” If the attack had been hidden from the victim, he said, it “could have been much more difficult to detect."
It's time for organizations to stop viewing third-party code as “'free functionality that saves the cost of having to write, test, and deploy that code themselves,” Williams said. ”We need to accept the fact that using third-party code creates an obligation to analyze for vulnerabilities continuously and respond to new vulnerabilities/attacks within hours.”