Achieving PCI - SSF Compliance
With Contrast Security
Contrast Security helps businesses meet all application security standards from the PCI Council and supports the upcoming migration from PA-DSS to PCI-SSF. Contrast has served as a trusted advisor to the PCI Council on application security for many years.
PCI Compliance:
What You Need to Know

The PCI Council publishes standards that govern the security of applications that store, process, or transmit payment cardholder data. Since the PCI Council first started publishing standards requiring application security back in 2004, the software market has changed dramatically, including the rapid adoption of APIs, open source libraries, complex frameworks, Agile and DevOps methods, CI/CD pipelines, containers, cloud-native, serverless, and more.
Consequently, the PCI Council no longer considers compliance as a simple checklist to demonstrate sufficient security for modern applications and APIs processing cardholder data.
Migrating to the new PCI
Software Security Framework (PCI-SSF)
All organizations building or operating software that stores, processes, or transmits cardholder data should now be using the PCI Software Security Framework (PCI-SSF) standards, and should deprecate the legacy Payment Application Data Security Standard (PA-DSS).
Currently, there are two standards under PCI Software Security Framework (PCI-SSF). Note that an additional “Web Software Module” is currently under development.
PCI Secure Software Standard (PCI-SSS)
The PCI Secure Software Standard (PCI-SSS) defines technical security requirements for software that stores, process, or transmit payment cardholder data. The PCI-SSS is less rigid than the DSS or PA-DSS, allowing vendors flexibility in how they reach each objective. The requirements fall into categories of 1) minimizing attack surface, 2) security protections, 3) secure operations, and 4) ongoing maintenance.
PCI Secure SLC Standard (PCI-SSLC)
The PCI Secure SLC standard (PCI-SSLC) is a set of organizational security capability requirements intended to ensure that a software vendor’s software development processes, technology, and personnel have security built into and throughout the entire software lifecycle. Broadly, the requirements cover 1) governance, 2) engineering, 3) software and data management, and 4) stakeholder communications.
PA-DSS vs. PCI-SSF:
What’s the Difference?
The now deprecated PA-DSS was released in 2008 and is now end-of-life in 2022. The PA-DSS is essentially a set of 14 prescriptive security requirements for applications that process cardholder information. Generally, the PCI-SSF is a much broader and flexible standard.
The PCI-SSF is intended to ensure products are developed using good security hygiene and encourages a sophisticated application security program rather than a simple compliance-oriented program. The PCI-SSF requires tangible evidence of a real application security program that meets both technical (PCI-SSS) and process (PCI-SSLC) requirements.
How Contrast Helps
Meet the PCI-SSF
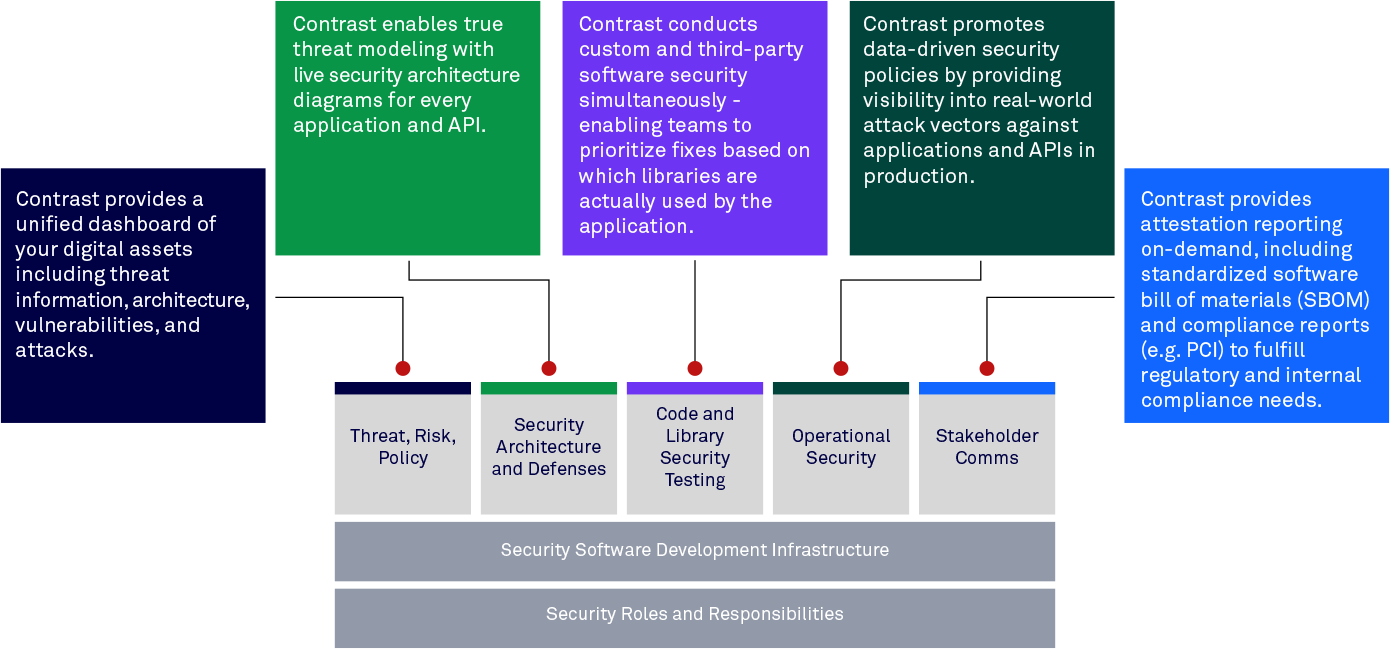
The Contrast Secure Code Platform provides a suite of capabilities to enable businesses to meet PCI standards head-on - aligning to both technical and process requirements of the PCI-SSF. The diagram below shows a high-level overview of Contrast’s support for six of the the seven major areas covered in the PCI-SSF. Since the original PCI specification was developed, Contrast Security has kept pace with major milestones within the software market by offering secure code coverage across API’s, cloud-native and serverless, open source libraries, and complex new frameworks to name a few areas. Contrast Security uniquely delivers this built on a common platform.