Highlights From Contrast Security's Bimonthly Application Security Intelligence Report
The saying that “every company is a software company” has never been more apropos. With the onset of COVID-19, we have witnessed an acceleration in the digital transformation already taking place. More code is now being written and deployed, at a faster pace than ever before.
This new normal allows businesses, customers, partners, and employees around the globe to stay connected and stay afloat. However, this increased focus on application development and faster release cycles also provides malicious actors with more and bigger targets. Over the previous six months, Contrast Labs has seen higher than average rates of applications with vulnerabilities (as compared to the May 2019–June 2020 metrics reported in Contrast’s 2020 Application Security Observability Report), and even more alarming, applications with serious vulnerabilities (Figure 1). The same trend can be seen on the attack front, where three of the top five vulnerability targets were hit in a larger percentage of applications than in the previous 12 months.
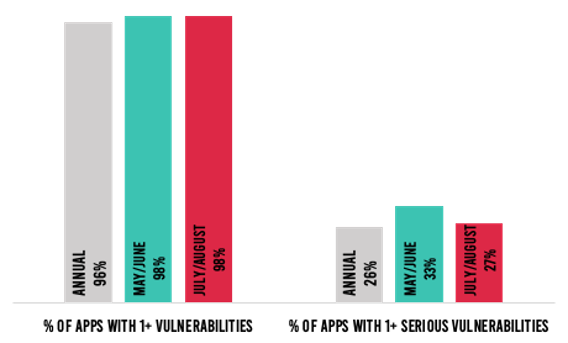 Figure 1: Percent of applications with one or more vulnerabilities and serious vulnerabilities
Figure 1: Percent of applications with one or more vulnerabilities and serious vulnerabilities
98% of applications had at least one vulnerability in July–August, for the second bi-monthly period in a row. The percent of applications with serious vulnerabilities, however, fell by 6%. Serious vulnerabilities were found in 27% of applications in July–August, compared to 33% in May–June. In addition, all five of the most common vulnerability types saw a drop in prevalence—which is great news for those responsible for applications. The likelihood of a cross-site scripting vulnerability dropped by 18% overall, compared to May–June—4% in Java applications, and 50% in .NET applications.
Hopefully, these downward trends are a sign that many organizations are starting to adapt to the current landscape and are prioritizing the remediation of vulnerabilities with the greatest likelihood to deleteriously impact their businesses.
Yet, despite the above, there are some warning signs in July–August data—specifically, the percent of total vulnerabilities that are serious increased. Notably, high-severity vulnerabilities increased from 24% to 27% and critical vulnerabilities grew from 4% to 5% of all vulnerabilities reported in July–August as compared to May–June. In return, we saw a decrease of 8% in total vulnerabilities without severity. This likely is an indication that organizations continue to struggle with prioritization, remediating lower, easier-to-address vulnerabilities before more business-critical ones.
Overall attack volumes declined in July–August, down from 9,008 in May–June to 8,346 in July–August. This trend was reverse for Java and .NET applications where attacks were up, experiencing a 4% and 42% surge, respectively. In the case of Java applications, they saw greater than a 2% increase in the likelihood of being attacked by the top five most common vulnerabilities.
The alarming rise in .NET attack volume was driven by increases in the percentage of applications targeted by broken access control and SQL injection attacks. Compared to 80% of .NET applications experiencing SQL attacks in the May–June time frame, nearly 100% of .NET applications experienced an SQL attack in July–August (Figure 2). If this isn’t a red flag for developers and application security specialists, I don’t know what might be!
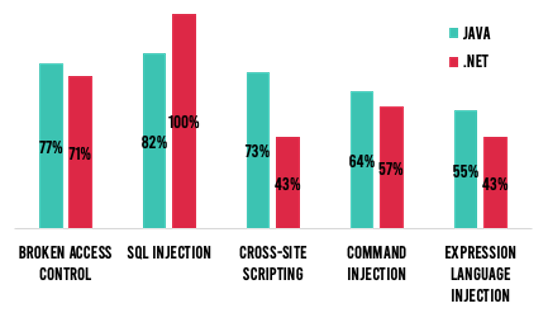
Figure 2: Percent of applications with attacks targeting the top 5 most common vulnerabilities in July-August.
Taking a step back, there is some good news on the attack front. The percent of attacks that were viable—namely, those targeting an existing vulnerability within the intended vulnerability—was the lowest it has been in 2020 (Figure 3).
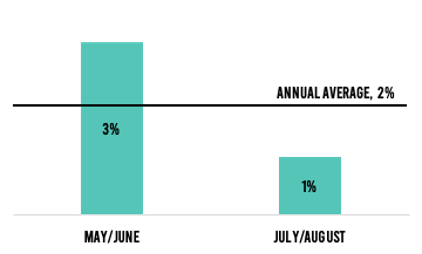
Figure 3: Percent of that were viable.
While growing numbers of organizations stabilized operations in July–August, software vulnerabilities and attacks continue to plague applications. The following are some of the top takeaways in the bimonthly report for readers:
Security, development, and operational teams can find additional metrics and trends about the current risk landscape in Contrast Labs’ July–August Application Security Intelligence Report. Combining this knowledge with their internal data, as well as other industry reports, enables teams to bolster their application security efforts while lowering the related risks.
For the entire report, readers can download a copy today or listen to the Inside AppSec Podcast interview with Contrast’s CISO David Lindner and me.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.