December 2, 2019
Runtime Application Self-Protection (RASP) adds threat visibility and security control to application runtimes so you can continuously discover application threats and block attacks—as they are still happening. Enjoy visionary RASP breach protection for your application layer and gain the fastest possible security response with superior 'insider' visibility and low false positive rates.
How do you defend that unaddressed attack surface deep down inside the application layer? Monitoring for security threats in a running application has typically always been a guessing game. Without any visibility into the internal workings of applications or without instrumentation like Runtime Application Self-Protection (RASP), security teams might be employing a 'hope' strategy:
SOCs and security teams require more effective ways to monitor, detect, disrupt, and block application-layer attacks while incident response teams seek deep contextual insight into attacks and threat actors.
Instead of relying on traffic-sniffing perimeter (IPS/IDS, WAF) solutions which cannot see the threats inside applications, modern security operation teams can look to emulate what developers have gained with instrumentation for application performance monitoring (APM) as a more effective way to monitor for security events with much greater visibility. Many enterprise security teams have already begun to innovate and adopt RASP (Runtime Application Self-Protection) instrumentation located inside the application itself to make applications self-protecting, which is especially helpful to improve threat monitoring and incident response.
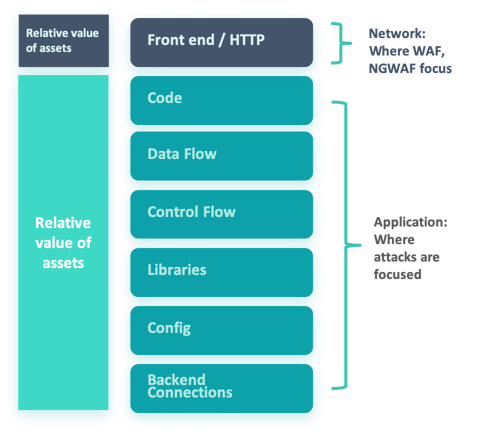
Let's face it, developers of applications are pressured to innovate and improve core functionality and may not get around to prioritizing security or vulnerability issues. For legacy applications developers may be unable to modify or retrofit an application at all, but RASP can still protect the application using RASP instrumentation inside the application itself—a big advantage to solve the security problem of vulnerable software.
So, in response to development and visibility limitations, modern security protection teams are increasingly looking to adopt RASP and solve threat monitoring for the entire running application. Security professionals are no longer satisfied with a flood of alerts, limited visibility into only parts of a library or into uncompiled code (like scanning), or limiting themselves to just traffic monitoring from the outside perimeter of an application (like WAFs). SOCs are learning how RASP instrumentation sensors located inside the application will monitor and log everything—logging all events that happen inside the runtime—so you can alert, disrupt, block, and respond continuously to the security events that matter most to you while continuing to use your favorite security tools.
|
“Monitor for security threats just like monitoring performance and use application threat intelligence to gain full context about an attack while it is still happening, then block the attack instantly.” |
How would you like a blue team solution that improves your MTTD (Mean Time To Detect) and MTTR (Mean Time To Respond) benchmarks for a more mature SecOps and better overall security? Of course, you would. With RASP your security teams can automatically collect, discover, and quantify threats—and perform investigation and remediation—with hyper-accurate visibility and low false positive rates thanks to built-in Code Security while also digesting threat intelligence using existing common SOC tools and consoles you're already familiar with (logging, SIEM, more).
RASP application threat monitoring empowers the SOC to monitor applications like never before. You can monitor for security threats just like monitoring performance and use application threat intelligence to gain full context about an attack while it is still happening, then block the attack instantly. Runtime Application Self-Protection (RASP) technology delivers unprecedented visibility by using Deep Security Instrumentation to go as deep as possible into the application stack and protect it from threats. For every attack, RASP sees:
|
“Directly instrument and monitor application runtime code and APIs to identify and block attacks at the initial point of attempted execution inside your runtime environment.” |
Unlike firewalls (WAFs), RASP will directly instrument and monitor application runtime code and APIs to identify and block attacks at the initial point of attempted execution inside your runtime environment. Sensor location inside the actual application is how RASP gains full visibility and control of data flow to allow first-hand threat detection and rapid response while the code is still in the process of executing. Very fast!
With continuous threat visibility and control RASP can automatically alert security teams to threats that could lead to a breach event—and automatically block breach attempts during real-time code execution within the actual application runtime itself. There isn't any faster (or better) way to detect and block or disrupt threats before the damage associated with a breach has been done.
|
“There is no faster way to identify actual threats with 100% confidence and confirmation than to observe the threat executing malicious code in real-time.” |
RASP sensor locations inside application runtimes reduces overall security team alert fatigue due to extremely low false positive and false negative rates, unlike firewalls (WAFs) that cannot even differentiate a real attack (exploit) from just an attempted attack (probe). Because RASP monitors for threats inside the actual application runtime, security teams can automate blocking before threats manifest to surrounding attack surfaces. There is no faster way to identify actual threats with 100% confidence and confirmation than to observe the threat executing malicious code in real-time within the application runtime environment itself.
RASP code visibility ensures accuracy, unlike slower "behavior-based" detection solutions that have to wait for any behavioral consequences of code changes to manifest and confidently appear—an unacceptable response delay that a performing SOC or security operations team shouldn't wait around on before blocking and response countermeasures are deployed. The good news is that this rapid threat alerting technology is currently available. Code Security is an integral part of RASP and ensures your team has the fastest application threat detection and response times available in the world today.
RASP supports common integrations to digest security telemetry into popular SOC/SecOps threat monitoring and response tools, including Splunk visualizations, and customizable application and user activity logging. RASP even provides valuable real-time attack surface and external API mapping to know true surface context, along with Software Composition Analysis (SCA) to positively identify and then control third-party library use.
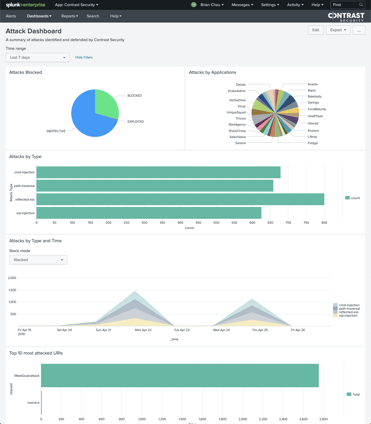 Log Enhancement extends RASP threat monitoring deep into the inner workings of application and user behavior and without developer intervention so you as end-user can log anything inside the application and send threat intelligence directly to your log management or SIEM solution of choice. Login failures, privilege escalations, specific database calls—any aspect of the application environment—can be logged and threat monitored for correlation to indicators of compromise (IoC) and attack (IoA). RASP seamlessly integrates into existing threat monitoring infrastructures you're already using so operation teams can leverage this newly available threat intelligence in their system of choice instead of adding another screen or dashboard.
Log Enhancement extends RASP threat monitoring deep into the inner workings of application and user behavior and without developer intervention so you as end-user can log anything inside the application and send threat intelligence directly to your log management or SIEM solution of choice. Login failures, privilege escalations, specific database calls—any aspect of the application environment—can be logged and threat monitored for correlation to indicators of compromise (IoC) and attack (IoA). RASP seamlessly integrates into existing threat monitoring infrastructures you're already using so operation teams can leverage this newly available threat intelligence in their system of choice instead of adding another screen or dashboard.
Policy creation enables whatever choice of logging you set with the ability to respond immediately to security events as they happen in real-time within the runtime of an application and according to conditions that are most important to you. Be alerted instantly when specified areas of the application are accessed or specific conditions occur (logins, privilege escalations, transactions, etc.). Policy can be managed with a button press using an award-winning console or you can deploy effective hands-off protection out-of-the-box in minutes with built-in OWASP Top Ten identification of common application attack vectors. And, because you're using RASP, all application threat monitoring and logging from inside application runtimes continuously operate without you modifying a single line of source code, without tuning or scanning, and without redeployments.
If faster threat detection and response with insider hyper-accurate visibility is still not enough, that's ok, because what is shared here is just scratching the surface regarding what RASP can do to improve your security and even your application development teams. Try for yourself the free, full-strength, Contrast Community Edition to find out first-hand how RASP protects web applications and APIs from attacks and discover exactly how RASP delivers improved blue team results, speeds up your SOC, and fully matures your SecOps. Thank you for helping us break the cycle of 'vulnerable software' and for allowing us to protect customers by protecting their applications.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.