Find and fix in real-time the vulnerabilities that really matter in your code
Development teams can secure every line of code with Contrast's Interactive Application Security Testing (IAST) solution that continuously detects and prioritizes vulnerabilities and guides them on how to eliminate risks. All with industry leading accuracy, efficiency, scalability, and coverage.
Turn every test into a security test
More context = accurate results
Fix faster
Applications that are built and deployed in a rapid cadence within the AWS cloud offer us greater scalability, agility and resilience. By automating application security into DevOps processes, Contrast helped GreenSky keep up with the demand to keep delivering business value with increasing speed.
David Butterworth
Senior DevSecOps Engineer


Contrast Assess for Log4j
Contrast Assess detects the underlying vulnerability in applications. This means, Contrast will find the next application vulnerability like this one, before it becomes a disclosed CVE or major incident.
The world’s leading
IAST solution
Now development teams can secure every line of code with breakthrough IAST technology that continuously detects and prioritizes vulnerabilities and guides them on how to eliminate risks.
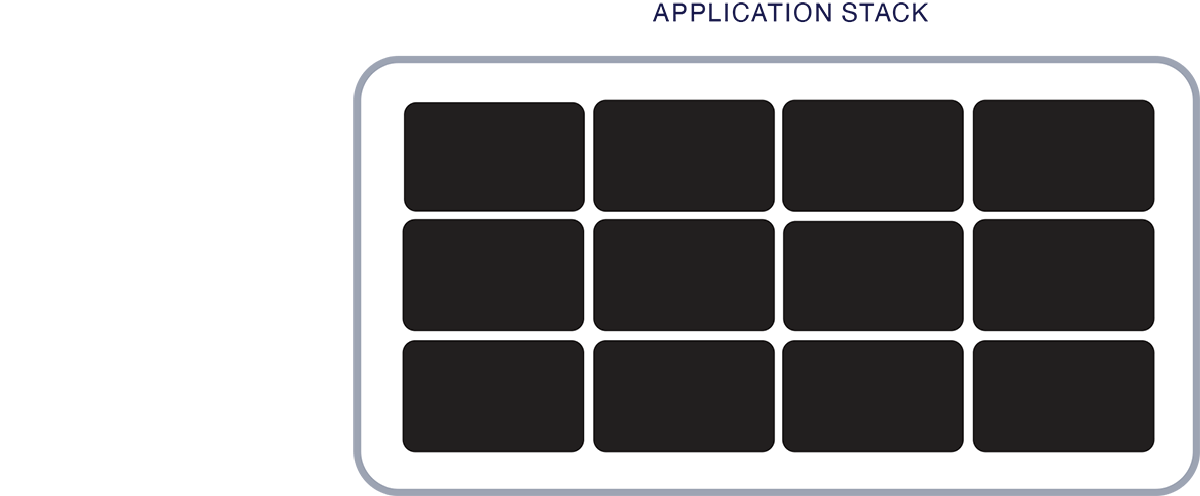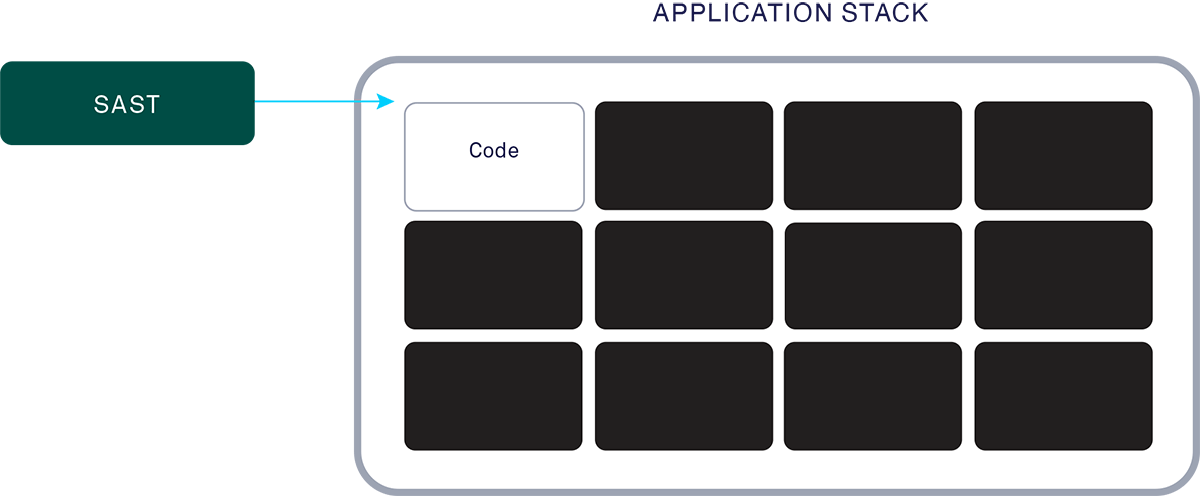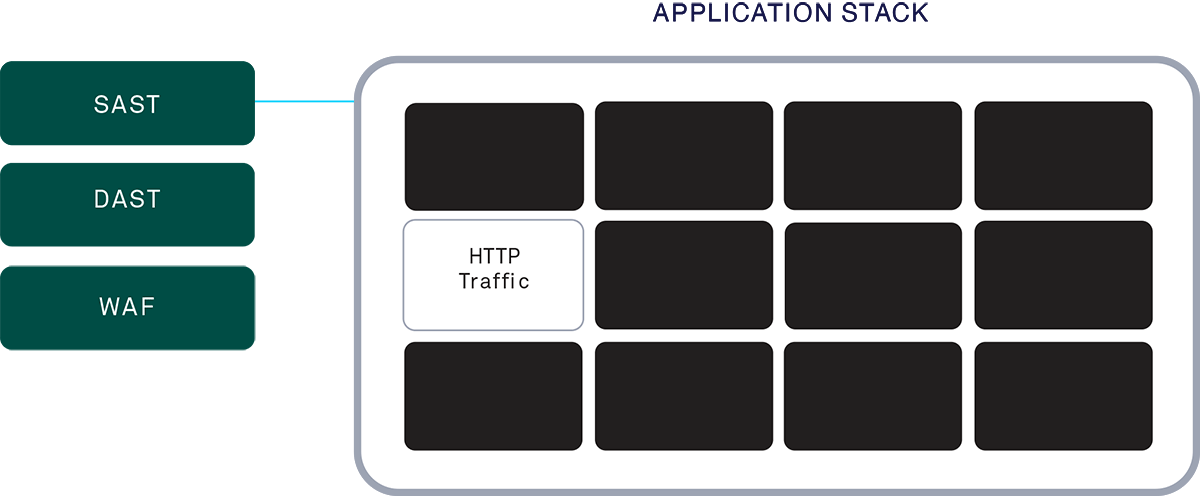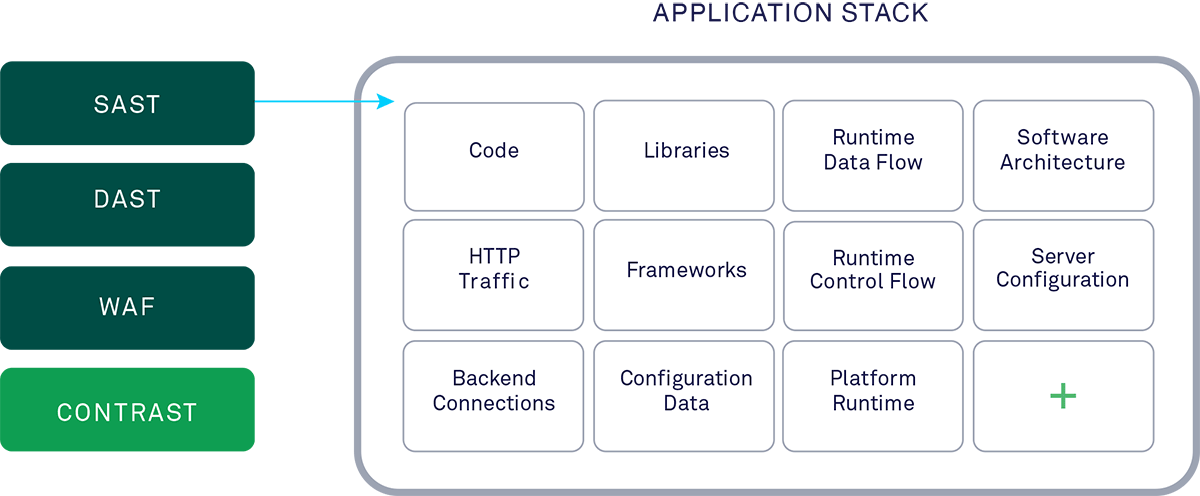
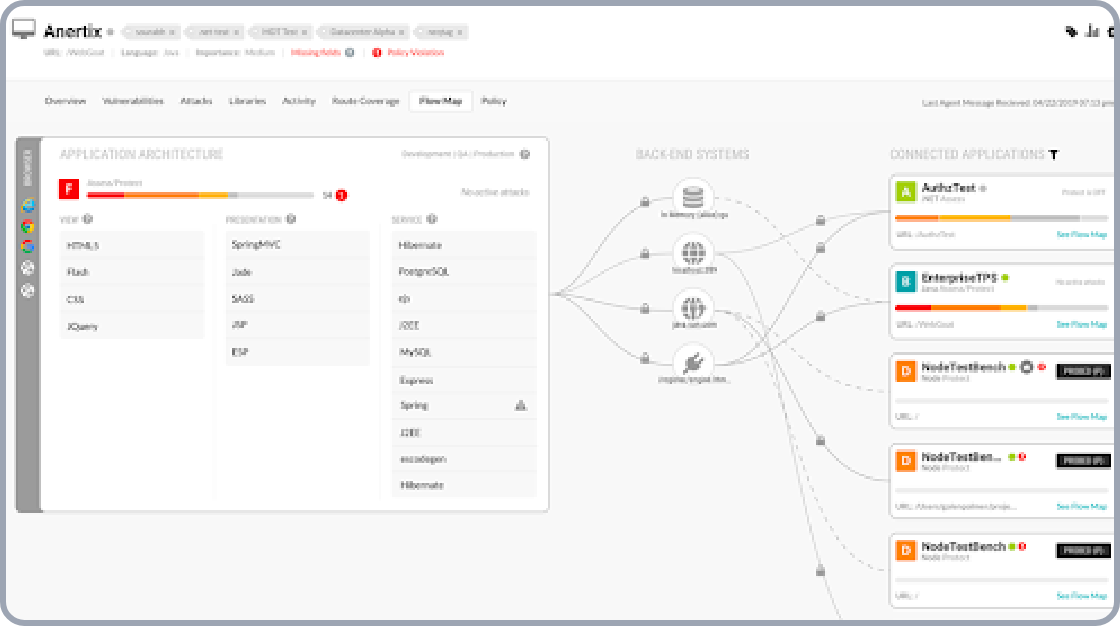
Live architecture
and flow view
In-depth visualization of application components, code trees, and data flow
In order to manage software inventory and identify aggregate risk in applications, and by leveraging the instrumentation insights of the Contrast agent, organizations can visualize application architecture, code trees, and message flow information. Contrast automatically generates simple diagrams that illustrate the application’s major architectural components. This information helps the developer quickly identify the meaning of a vulnerability that Contrast pinpoints and can form a starting point for threat modeling remediation.
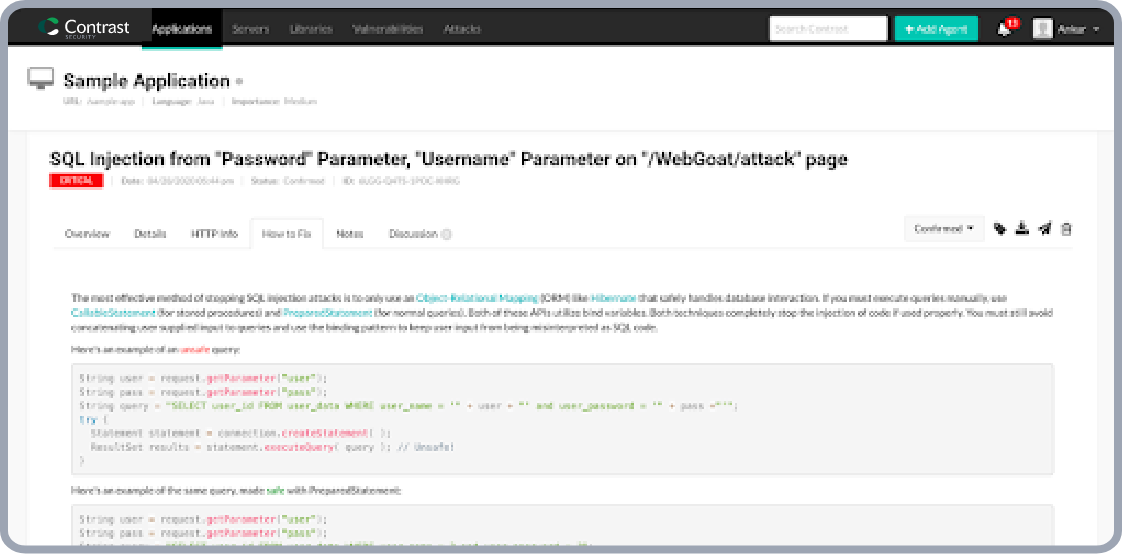
Developer remediation guidance
Pointed, code level remediation guidance
The Contrast platform explains vulnerabilities to those that need to understand and fix them. Contrast’s innovative Security Trace format pinpoints exactly where a vulnerability appears in the code, and how it works. This enables developers to fix vulnerabilities easily without the need of security expertise.
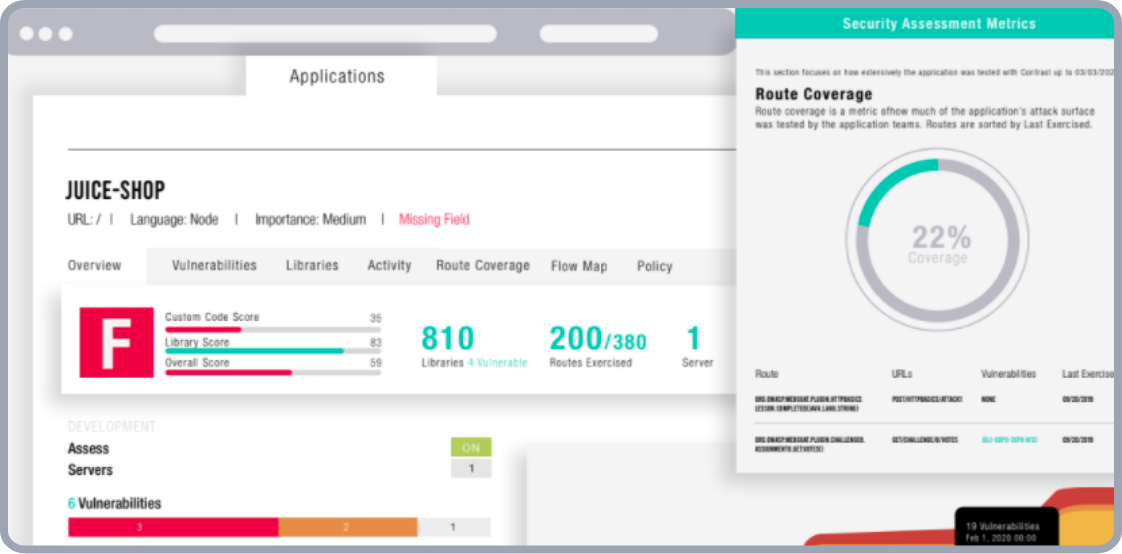
Application attack intelligence
Attack surface mapping with route and URL intelligence
Contrast Assess provides developers a mapping of the URL and routes of their software that are executed during the testing phase of the SDLC. This helps security teams increase confidence in the coverage of the Assess solution as well as developers identify the effectiveness of their overall testing practice.
Contrast Security is a #1 Leader in G2® Grid Report for IAST
With a Satisfaction Score of 93 out of 100, Contrast Assess was rated #1 for Quality of Support, #1 for Market Presence and #1 for User Satisfaction
Resources to help you get
secure code moving

Securing Kafka in Modern Application Environments: A Crucial Step for Today's Businesses
Learn the importance of Apache Kafka security in modern application environments and how Contras Assess can identify and fix real-time Kafka vulnerabilities.

Solution Brief:
Contrast Application Security Platform: Realizing the Full Potential of DevSecOps in Modern Software
Experience Contrast Assess
Schedule a one-to-one demo to see how you could reduce your security risk 1.7x by continuously assessing vulnerabilities in your code
Discover other products on the
Contrast Runtime Security Platform
Contrast Protect
Detect and block run-time attacks on known and unknown code vulnerabilities with greater precision
Contrast Scan
Identify and fix real vulnerabilities faster with unparalleled scan accuracy
Contrast SCA
Test and protect third party, open-source code moving through your software supply chain












