By David Lindner, Chief Information Security Officer
May 26, 2021
Only 25% Can Successfully Triage All Security Alerts, and 98% Have Had 3+ Successful Attacks
The financial services industry has long been a big target for cyber criminals, and the past 12 months have been no exception. While a lot of media attention has focused on cyber attacks on healthcare institutions that were trying to provide lifesaving care during a pandemic, attacks have continued apace for banks, investment firms, and insurance companies.
Verizon’s brand new 2021 Data Breach Investigations Report finds that the financial and insurance industries suffered 721 data breach incidents in the past year. And the share of those events with confirmed data disclosure skyrocketed from 30% to 65% compared with 2020, with 467 instances where data was definitely stolen.
Some of these attacks took advantage of the unique world we have lived in for the past 18 months due to COVID-19. Adversaries recently breached the online sales system for Geico, stealing thousands of driver’s license numbers. The hackers were apparently not able to access other personal information such as social security numbers, and driver’s license numbers alone would ordinarily not be a highly valuable haul. But at a time when the federal government was supplementing unemployment insurance payments, this information is enough to file fraudulent unemployment claims in the names of unwitting citizens. Indeed, the Internal Revenue Service reports that multiple states have seen a surge in fraudulent claims recently.
Other institutions have escaped close calls because vulnerabilities were caught by security researchers before bad actors could find them. One researcher exploited an unsecured application programming interface (API) for an Experian tool that enables lenders to automate FICO-score queries. Once inside, he was able to access credit scores and risk factors from Experian’s database.
To gain insight into the state of application security in the industry, Contrast Labs commissioned a survey of application security and development professionals—and C-level IT leaders—at large financial services institutions across North America. We have just released our 2021 State of Application Security in Financial Services Report to share the findings.
Survey respondents work for banking, insurance, and investment companies with at least 5,000 employees. Six in 10 represent companies with at least 15,000 employees. The cohort was balanced by role, with 44% working in application security and 46% associated with development or DevOps teams. Individual contributors comprise 44% of respondents, while the remaining 56% are managers, directors, VPs, or C-level IT and security executives.
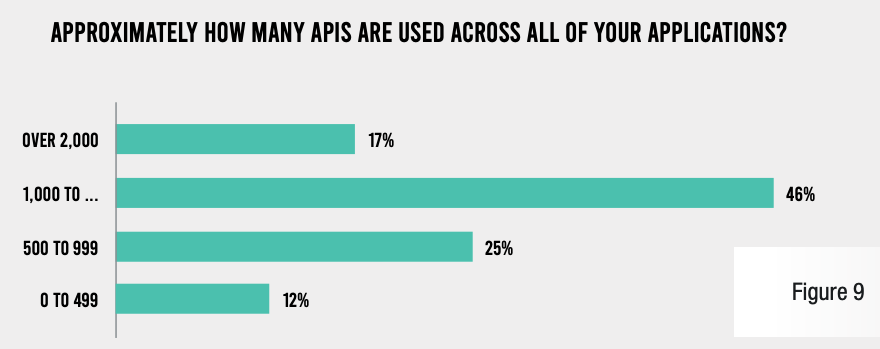
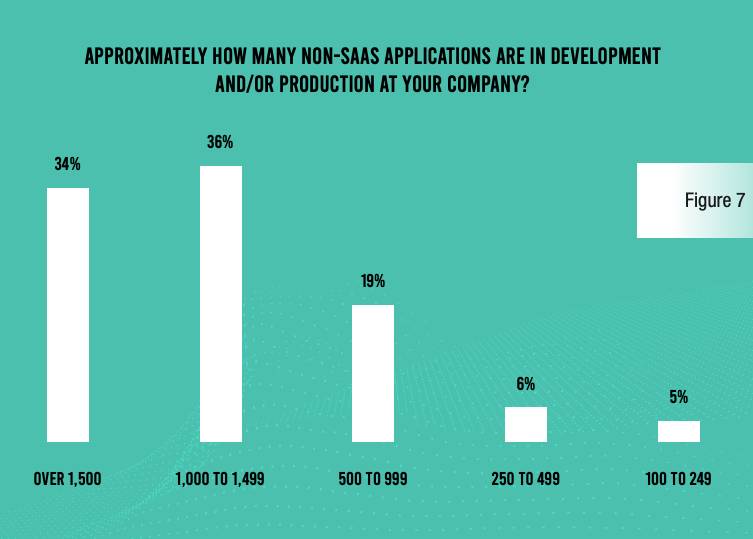
One key finding of our research was that software development operations at financial services institutions are very mature. While organizations in many industries have just recently embraced methodologies like Agile and DevOps, they are largely entrenched in the firms represented in the survey. More than 1,000 APIs are in use at a significant majority (63%) of organizations, and even more institutions (70%) have more than 1,000 applications in development or production. A similar percentage (65%) releases code into production multiple times per day.
APPROXIMATELY HOW MANY APIS ARE USED ACROSS ALL YOUR APPLICATIONS?
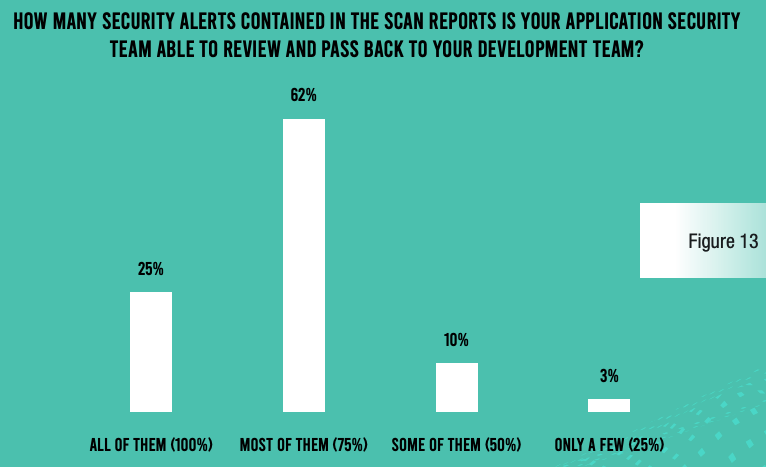
Unfortunately, application security has not kept pace with the speed and efficiency of the development team at the companies included in the survey. One of the most eye-popping findings of our survey is that only 25% of respondents say they are capable of reviewing all the security alerts contained in scan reports and pass them back to the development team for remediation. That number is slightly better for large enterprises (more than 15,000 employees), where 35% can account for all alerts. But only 5% of respondents from organizations with 5,000–9,999 employees can account meet this benchmark. Regardless of the reason they cannot bring some level of closure for every alert, this is a serious problem.
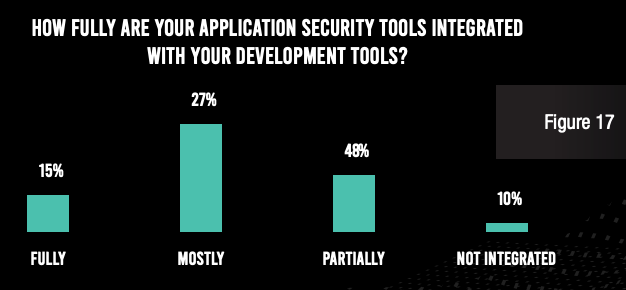
One reason for financial services institutions’ inability to address every alert may be the sheer number of alerts and limited bandwidth on the part of the application security team. Another is a lack of integration in the development and security architecture. Only 15% of respondents said that their application security tools are fully integrated with their development tools. Disaggregated tools create wasted cycles throughout the software development life cycle (SDLC).
One consequence of a lack of integration is limited observability. An astounding 97% of respondents in this highly regulated industry admit that they do not have full visibility across all their APIs, and 63% cannot claim that even most of their APIs are observable.
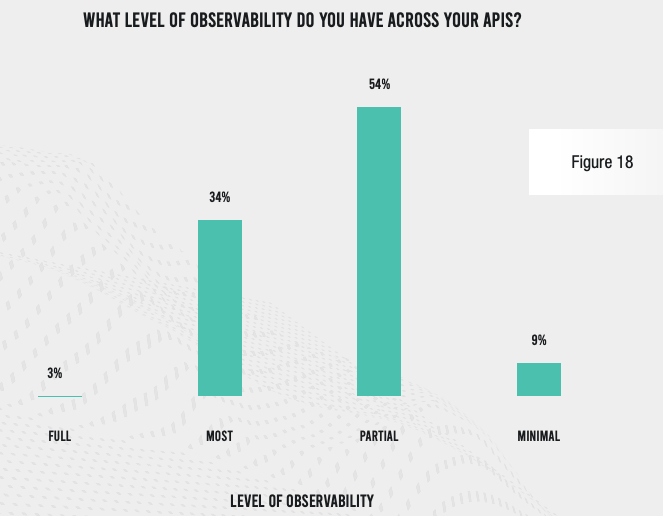
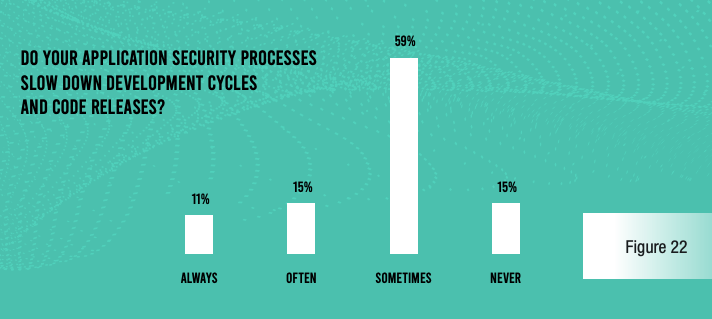
This lack of integration and observability is creating problems for development and release cycles. Fully 85% of respondents admit that application security processes slow code releases at least some of the time. For the smaller organizations in our survey (5,000–9,999 employees), 27% say that security-related delays happen every time, and another 43% say this happens most of the time.
One reason for these delays is frequent security scanning of applications in development in an attempt to stay on top of vulnerabilities. Well over half (56%) of respondents do static application security testing (SAST) scans at least 100 times per year per application, and nearly everyone does dynamic application security testing (DAST) scans every day for each piece of software.
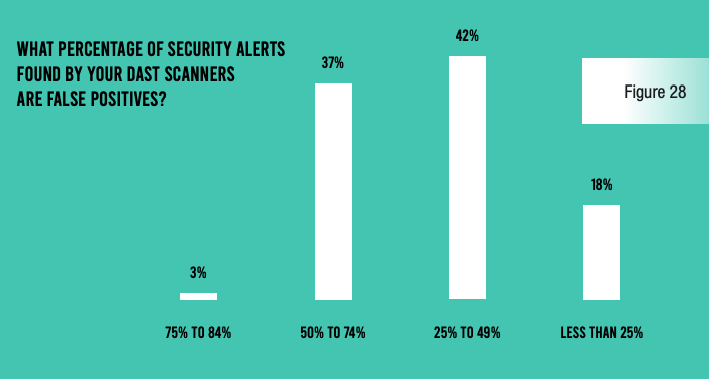
Unfortunately, these scans yield a lot of false positives. More than three-quarters (78%) of respondents estimate that at least half of alerts from their SAST scans are false positives, and 40% say the same thing about their DAST reports.

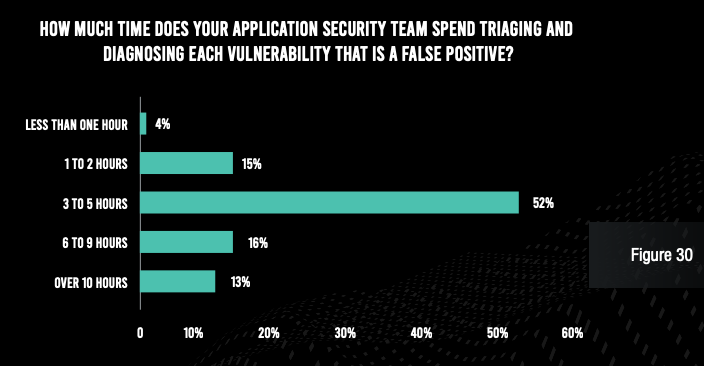
Of course, the result of these inefficiencies is a lot of wasted time on the part of both application security and development team members. The vast majority of respondents admit that the security team spends at least three hours with each false positive and at least six hours with each true vulnerability. And the security operations team spends at least 15 hours per vulnerability found in production. Developers, for their part, spend six hours or more per vulnerability identified in development, and at least 15 hours per vulnerability found in production.
While these numbers may sound manageable, it should be noted that each of these numbers must be multiplied by hundreds of false positives per application, hundreds of true vulnerabilities per application across the SDLC, and hundreds or thousands of applications at the typical organization. Financial services institutions are truly wasting tens of thousands of staff hours per year because of ineffective application security tools and processes.
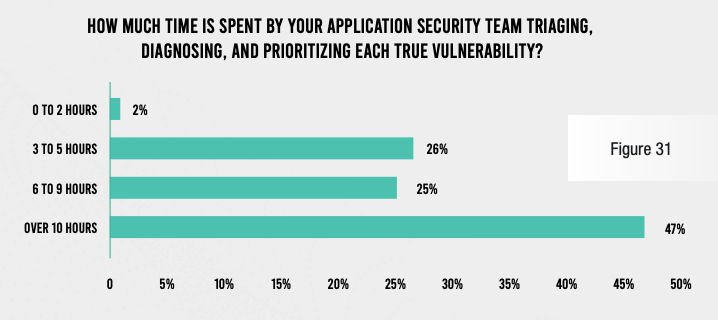
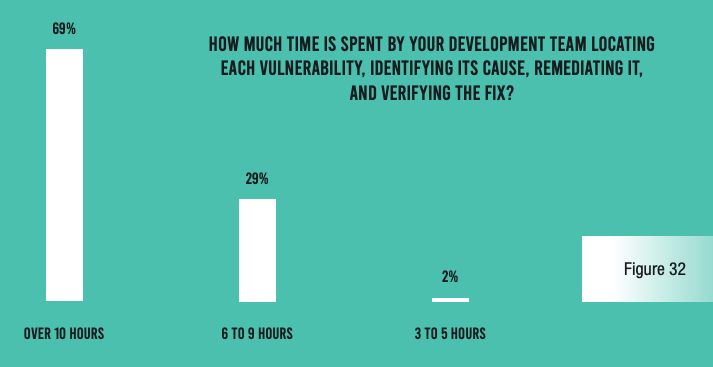
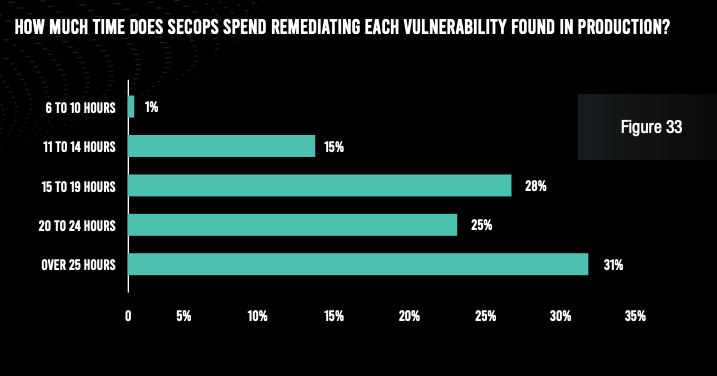
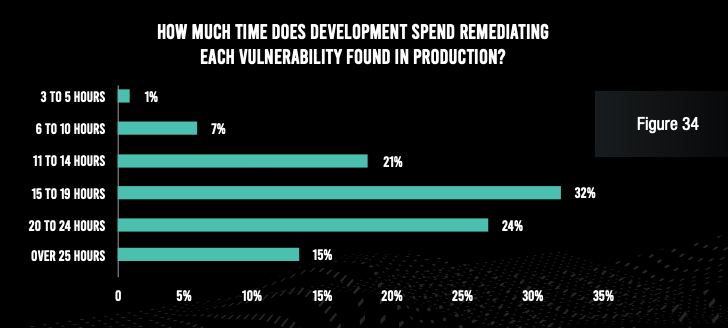
Security operations teams at the typical organization also expend three hours per application per month keeping their web application firewalls well tuned—potentially adding up to tens of thousands of hours per year. And compliance reporting requires 40 hours per report at a typical organization—multiplied by 10 required reports and a frequency of four per year.
Despite the enormous time commitment to application security, vulnerabilities and attacks continue to plague applications. Nearly two-thirds of respondents admit that each of their applications in development have an average of 20 serious vulnerabilities. Even applications in production have six or more serious vulnerabilities at a typical organization. And more than a quarter of their APIs have serious vulnerabilities at a solid majority of companies.
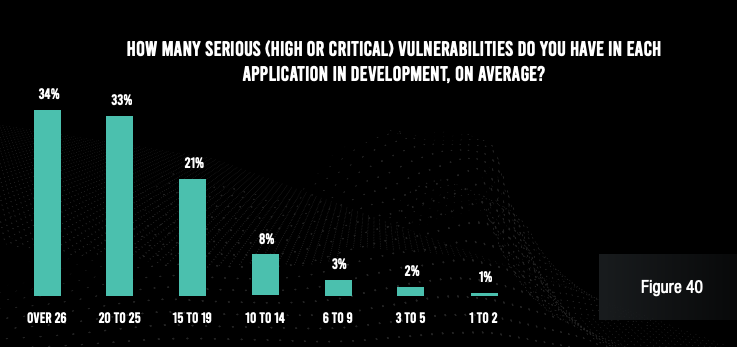
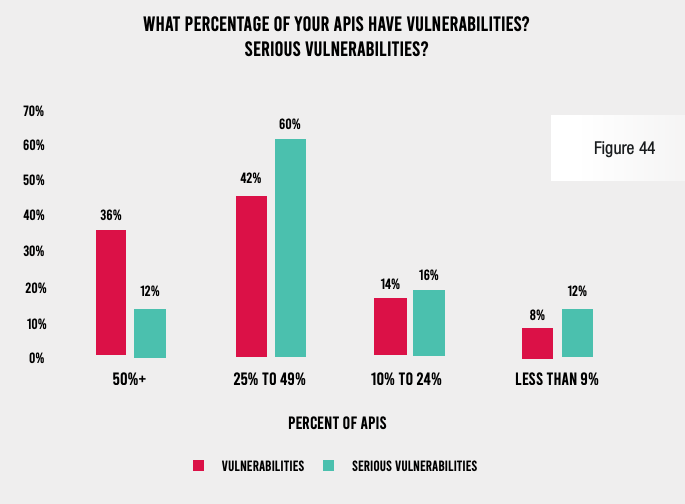
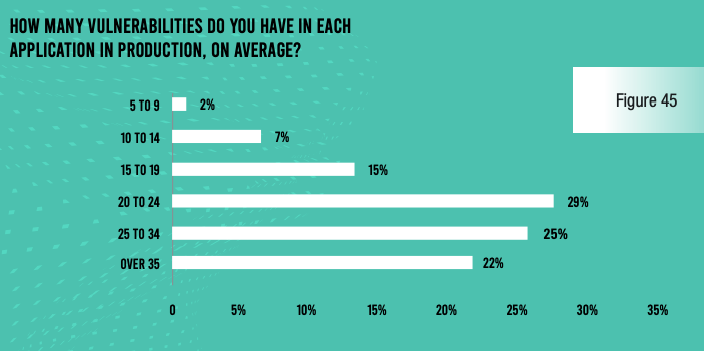
Even more worrying, nearly all respondents admit that they have been on the receiving end of at least three successful application exploits. And 52% of organizations saw more than 10 successful attacks. Each of these attacks cost $1 million or more in losses at three-quarters of organizations, and the typical organization spent more than 100 hours of staff time (internal and outsourced) to make repairs after each incident.
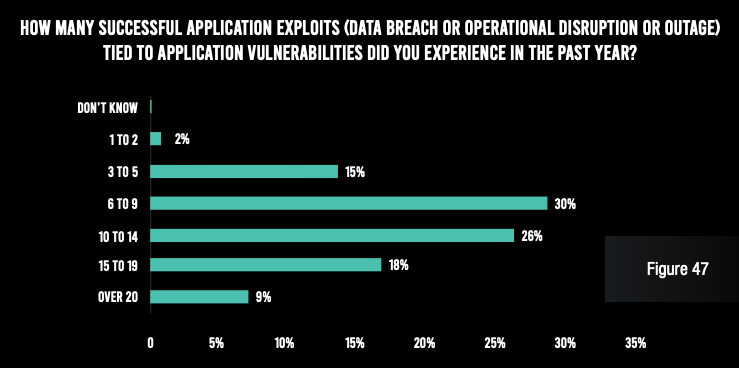
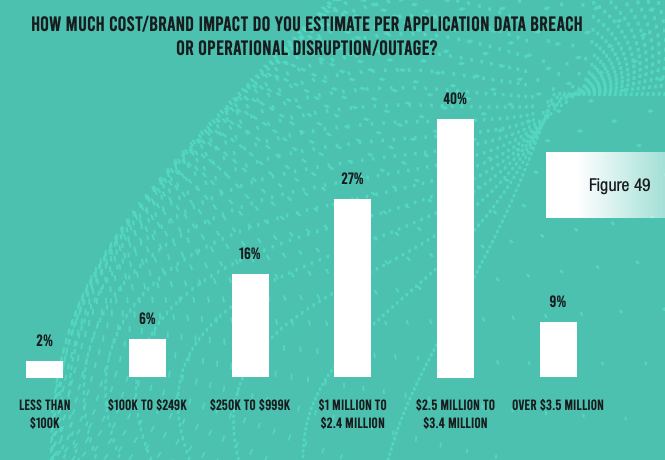
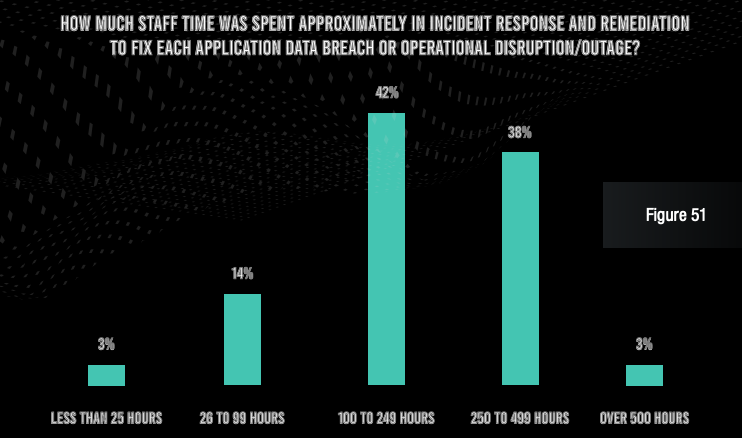
The findings of this report are very telling. Despite tens of thousands of hours spent by security and development professionals in dealing with alerts and vulnerabilities, financial services institutions are suffering millions of dollars in losses every year because of application attacks. One underlying problem is that most organizations cannot even adequately deal with all the alerts from their scan reports—partly because of a lack of application security observability.
This state of affairs can cause a variety of problems. A burgeoning security debt of unresolved vulnerabilities can increase an organization’s overall risk posture. Attackers need to find just one serious vulnerability to launch a damaging attack, and the typical application has many. And in a highly regulated industry like financial services, inadequate application security can make compliance can be more difficult to achieve—and to document to auditors.
Of course, integration is key to improving both the operational efficiency and effectiveness of an applications security program. Application security tools should be natively connected with each other and with every development tool in use at a given organization—something that is accomplished with the Contrast Application Security Platform. And Contrast’s instrumentation approach enables real-time discovery and remediation of vulnerabilities while coding is in progress.
As one of our survey respondents noted, “Attackers see the financial industry as an easy target, so we must always have strong security in place.” My hope is that financial services firms start moving toward a proactive, integrated approach to application security. If they do, the results of next year’s report will be much more positive.
REPORT: 2021 State of Application Security in Financial Services Report
PODCAST: Digital Transformation in Financial Services Accelerates, Application Security Struggles to Keep Up

David is an experienced application security professional with over 20 years in cybersecurity. In addition to serving as the chief information security officer, David leads the Contrast Labs team that is focused on analyzing threat intelligence to help enterprise clients develop more proactive approaches to their application security programs. Throughout his career, David has worked within multiple disciplines in the security field—from application development, to network architecture design and support, to IT security and consulting, to security training, to application security. Over the past decade, David has specialized in all things related to mobile applications and securing them. He has worked with many clients across industry sectors, including financial, government, automobile, healthcare, and retail. David is an active participant in numerous bug bounty programs.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.