If you are like the development team at Contrast Security and build Jenkins plugins, then you probably find value in the maven-hpi-plugin. The Jenkins Maven HPI Plugin hpi:run target initializes a local Jetty HTTP server with the current plugin project for development testing. This enables plugin developers to quickly prototype and test without deploying plugins to a separately managed instance.
However, during a penetration test, we found this exposes the Jenkins web application on all interfaces with no authentication by default. Any adversary on the same network can access the script console and compromise the running machine.
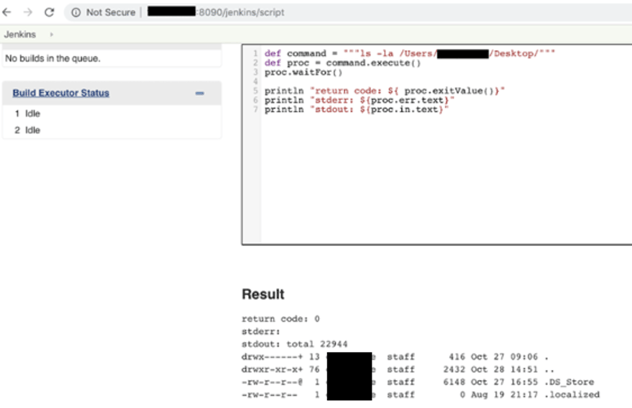
Jenkins Script Console Command Execution
Ideally, the plugin should configure Jetty to listen on localhost only by default, and provide configuration options and documentation in the event a user wants external hosts to access the Jenkins instance. Contrast Labs reported this issue to the Jenkins team since no configuration option was available to disable listening on all interfaces.
No CVE or formal notice was created since this issue only affects developers and not users. Starting in Jenkins 2.223, the plugin should only listen on the loopback interface (localhost) by default, unless the configuration option -Dhost=0.0.0.0 is specified.
- 11/18/2019: Issue reported to Jenkins (SECURITY-1667)
- 2/13/2020: Follow up with Jenkins
- 3/4/2020: Notice sent to DEV mailing list