A recent Executive Order from the Biden Whitehouse instructs various government agencies to take action to improve our nation’s cybersecurity. One of those actions is to provide guidance and standards on Software Bills of Materials (SBOMs). In this article, we will explore what SBOMs are and how to easily create them with Contrast Security’s free developer toolset — CodeSec.
An SBOM is a standardized format for recording all the constituent parts of a software product. It lists all the open-source libraries used, other third-party proprietary libraries and some metadata about the custom code in the product. The hope is that software purchasers, such as the Federal Government, will be able to use SBOMs in a searchable way for early detection and resolution of vulnerabilities hidden within the various parts of the products they use.
Compiling and authoring an SBOM by hand can be a maintenance nightmare. No one in their right mind would want to have the chore of combing through all the libraries used in a project and recording their information in a very rigorous JavaScript Object Notation (JSON) format. Imagine making a mistake only a few hours into such a project as your mind starts to daydream about something more interesting.
Luckily, CodeSec by Contrast provides a very simple command for creating SBOMs. After installing CodeSec, navigate to the top level of your project in your terminal and run the following command:
Run Command: contrast audit --save

SBOM file saved at the end of the contrast audit output
Near the end of the output of the audit command, CodeSec lists the name of the saved SBOM file. Viewing that file reveals it is a very extensive JSON record of the example project and the many libraries it uses. Some other highlights to note are that it lists the SBOM format used, the software vendor and the project name.
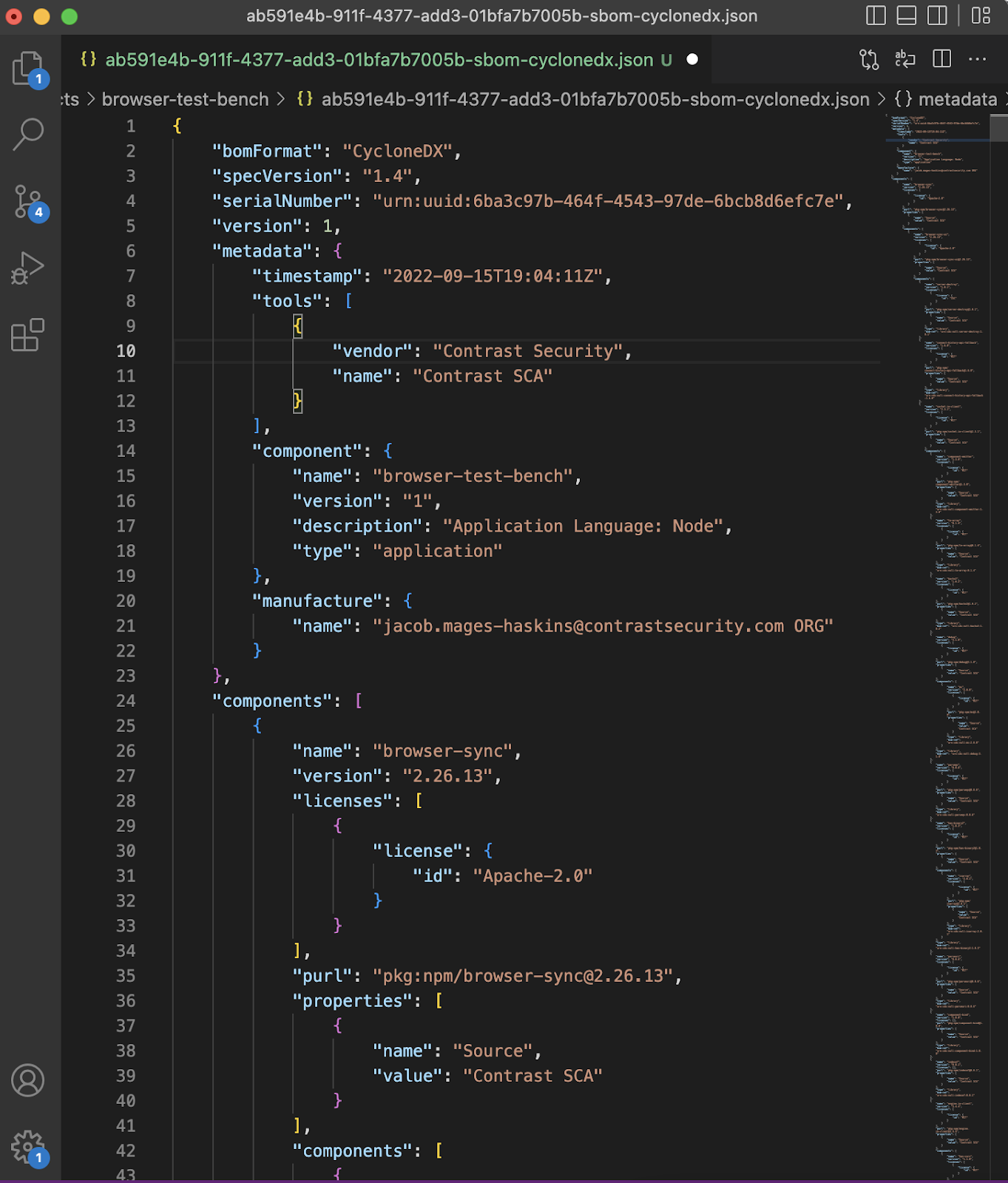
Once this file is created, it can be provided to customers or other security professionals related to your organization as needed.
Because CodeSec is a command-line tool, it is also possible to build software automation around creating SBOMs. For example, it is possible to add the following line to your project’s pre-commit Git Hook to create the SBOM and then add it to the commit, automatically and free for every commit:
git add ‘$(contrast audit --save | grep -e “(SBOM)” | cut -d “ ” -f 10)’
This command, if placed in pre-commit hook, would run CodeSec’s audit, tell it to create an SBOM, use grep to find the line in the audit output where the SBOM file name is at, then cut that line into pieces at every whitespace and grab the tenth piece — which is the full SBOM file name. After that, it would run Git’s “add” command to add the SBOM file to the commit in progress.
An SBOM provides greater transparency into the components that a software product uses, and that knowledge can help decrease cybersecurity risks for the purchasers of that product. CodeSec provides a super simple mechanism for automatically creating SBOMs that then enables even more opportunities for automating the SBOM creation process. Get started today!