This report summarizes Contrast Labs' analysis of real world application attack and vulnerability data from October 2019. It utilizes data from attacks that Contrast Security observed over the previous months and highlights the key trends found.
Developers, product owners, AppSec, and security engineers can use this information to better understand application security threats, adjust security controls, and improve their security posture.
Through reading this report on a monthly cadence, AppSec teams can gain a better understanding of the possible types and origins of attacks and attackers.
Visit our website to learn more about how Contrast Security continuously measures both vulnerabilities and attacks in parallel across your application portfolio.
Custom Code Vulnerabilities
Applications had an average of 5 open, serious vulnerabilities in October. This number decreased from an average of 6 open, serious vulnerabilities in September.
The top 5 most prevalent serious vulnerabilities reported in custom code for the first time during October:
Vulnerabilities by Language
On average, Java and .NET applications reported the largest number of the following attacks:
Custom Code Attacks
Attacks on custom code made up 99% of attacks last month.
The chart below shows the likelihood of a vulnerability having been reported for an application and the likelihood of an attack on those vulnerabilities in the month of October.
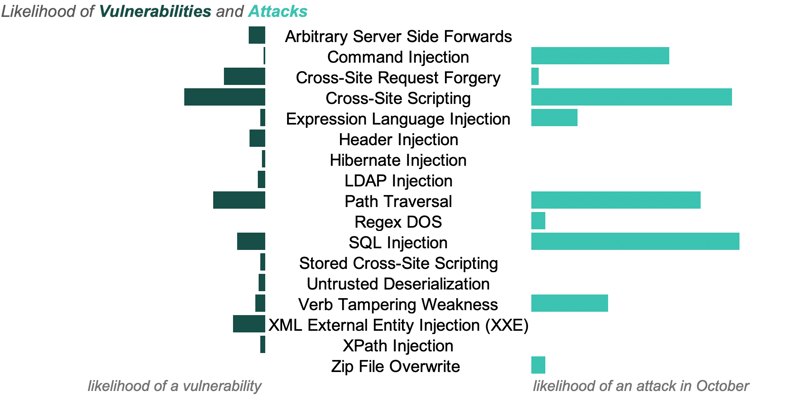
The three most common attack types in October:
89% of applications were targeted by one of these three types during the month.
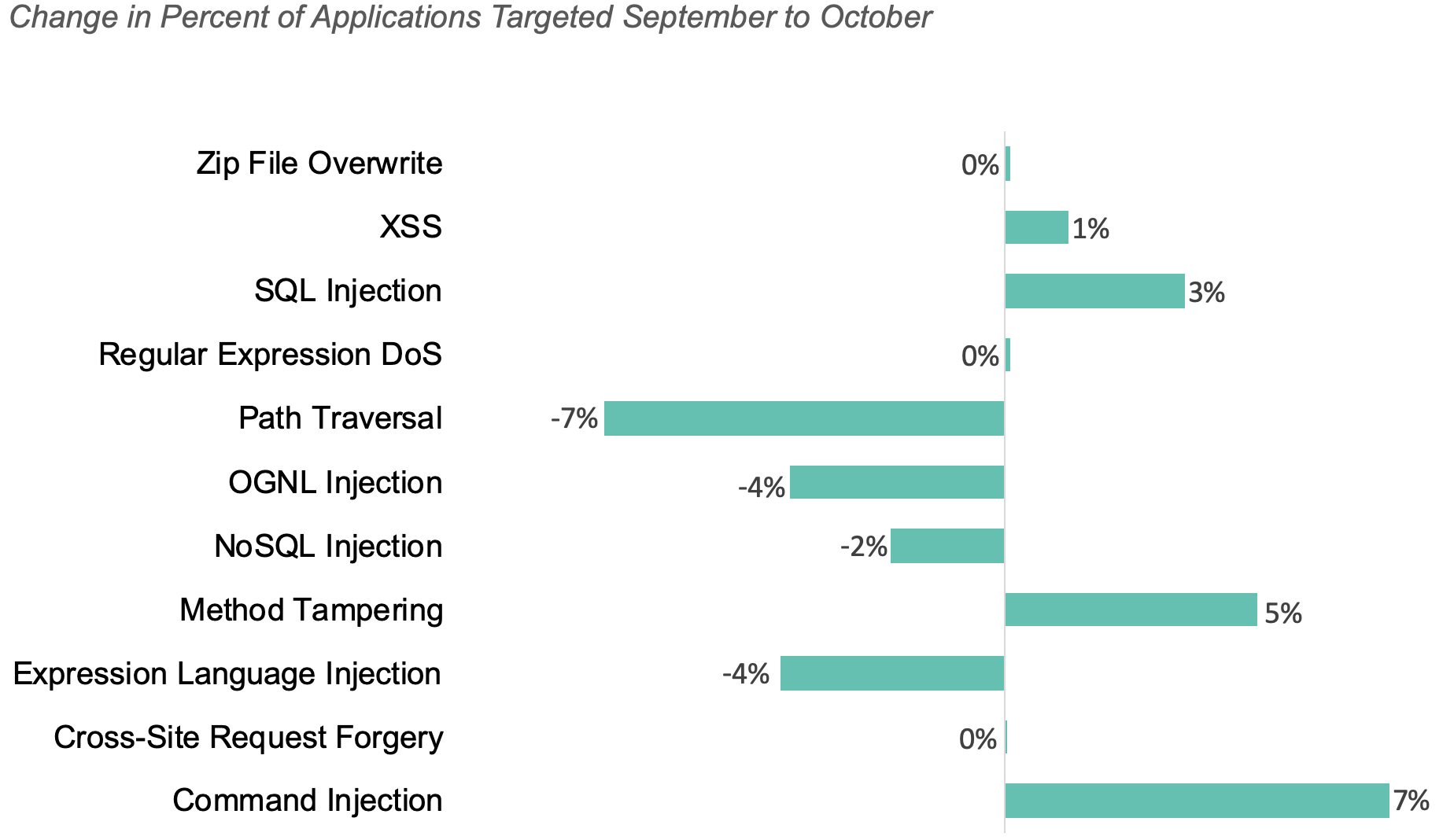
The chart below shows how the percent of applications targeted changed for each attack type month to month.
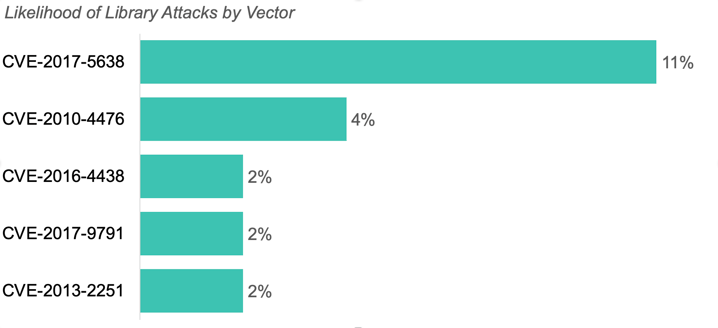
Library Attacks
The top attacks on CVEs were CVE-2017-5638, CVE-2010-4476, and CVE-2013-2251.
There were no recorded attacks on CVE-2013-2251 during September. However, these attacks have spiked again, targeting 2% of applications last month. First identified in 2013, CVE-2013-2251 is an improper input validation vulnerability in Apache Struts 2. Make sure that your team is proactive in identifying and blocking these rising attacks over the next month.
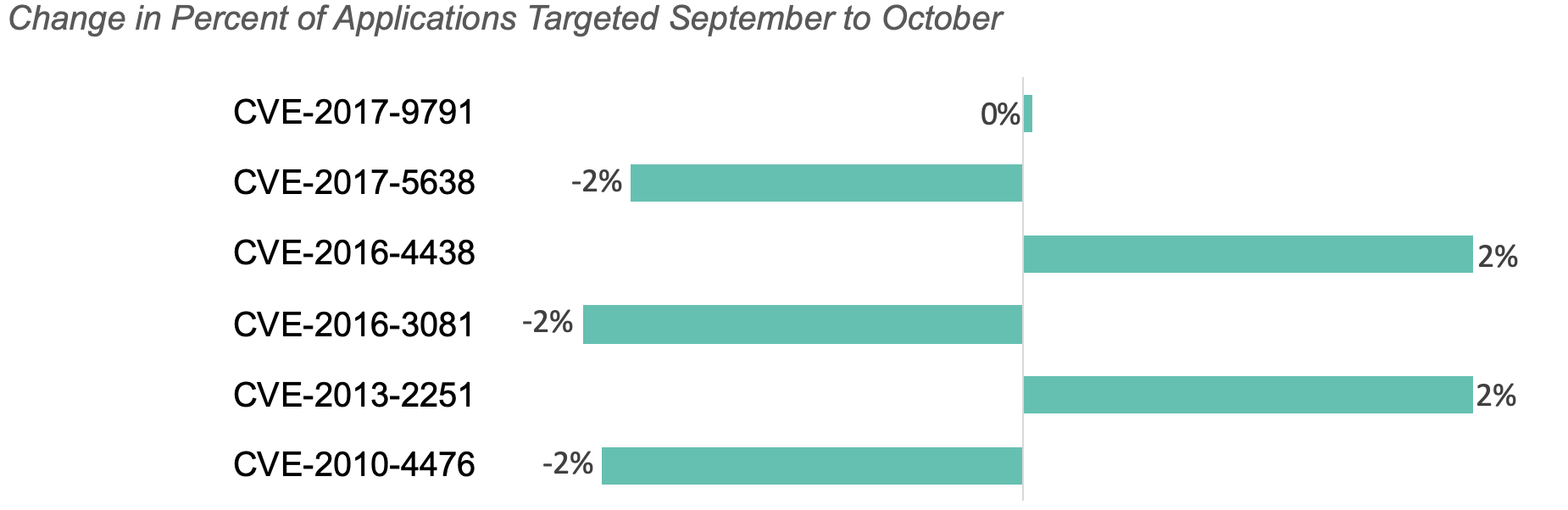
The charts below show the percent of applications of attacked, by CVE targeted last month and how this percent changed month to month.
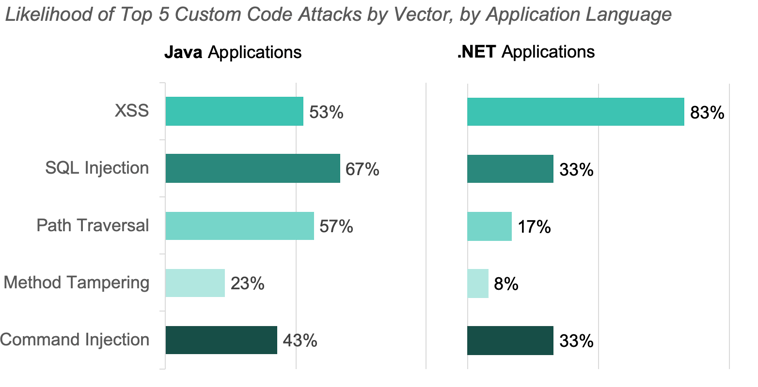
 Attack Vectors by Language
Attack Vectors by Language
Injection attacks continued to dominate, with Java applications targeted by the highest number of Command Injection attacks and .NET applications targeted by the highest number of SQL injection attacks in both September and October.
The charts below show the percent of applications attacked, by vector last month for both Java and .Net applications.
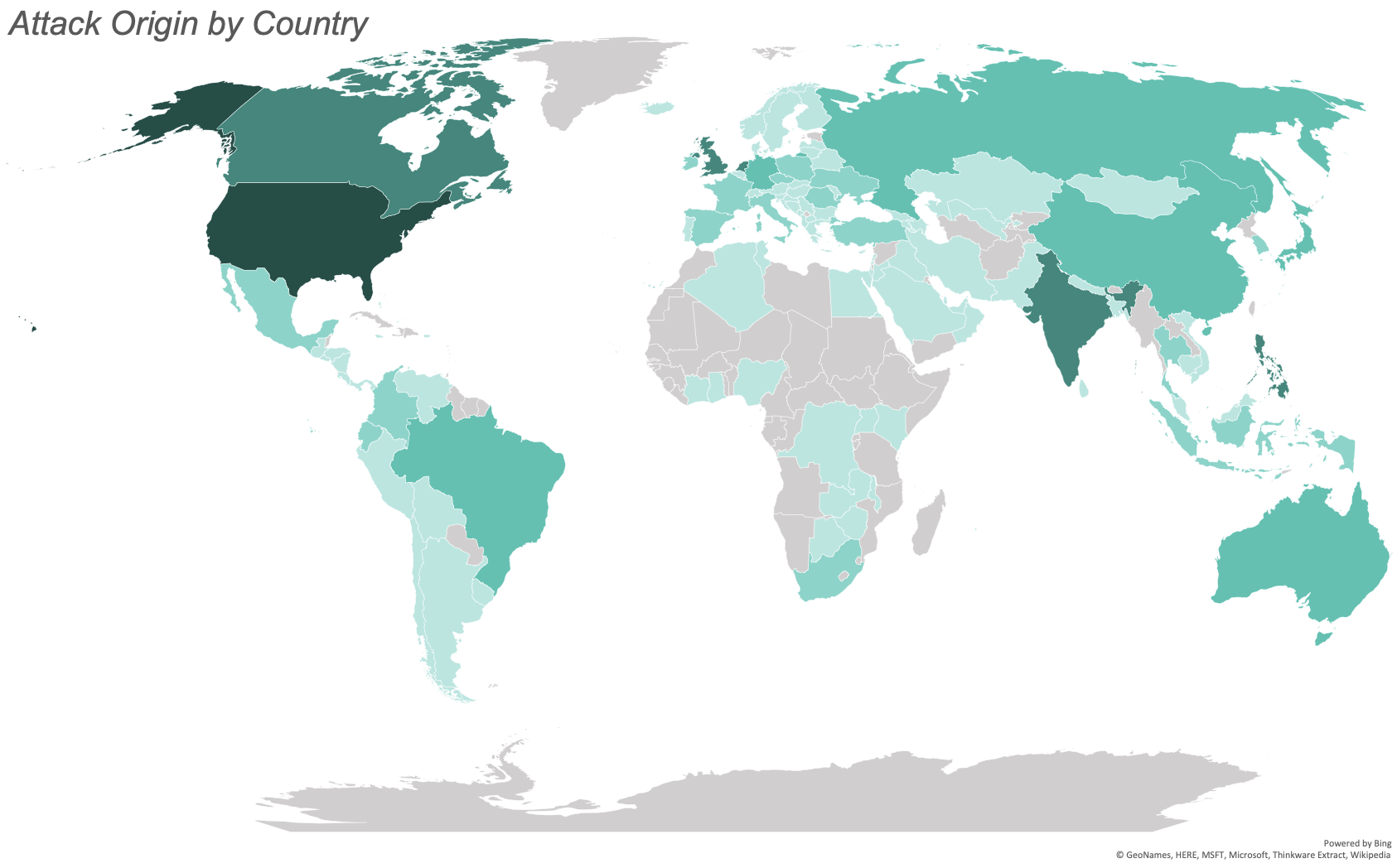
 Attacks by Geolocation
Attacks by Geolocation
October saw attacks from 127 countries. The greatest number of attacks originated from the United States, India, Canada, the Netherlands, and the Philippines.
The map below illustrates the number of attacks originating from each country with the most saturated color representing the most attacks and the least saturated representing the least attacks. We observed no attacks from the countries filled in gray.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.