It is time… time to ditch traditional approaches to the way we have managed application security. Specifically, it’s time to ditch your Web Application Firewalls (WAFs). Ten to fifteen years ago, WAF network security revolutionized the way we thought of securing our web apps, all done through the network layer. But today, network security alone just won’t cut it. Web Application Firewalls come at application security from an external perspective, employing network techniques to stop application attacks. Software is eating the world, and Web Application Firewalls weren't designed for that world. Below are 3 reasons why:
By defending from within the application itself, Contrast Protect has an inherent accuracy advantage over Web Application Firewalls products. WAFs only examine network traffic and have to make a decision based on assumptions they make outside the application, typically at the perimeter. Contrast sees what is really happening within the application, acting only when an application is vulnerable to an attack.
The key to accuracy in Contrast Protect is that it looks at more than just the attack. Contrast Protect observes exactly how a potential attack flows through an application and whether it hits a vulnerability that is susceptible to that attack. Contrast sees the HTTP-request and -response, configuration files, code execution, backend connections, and more.
By the nature of their design, WAF network security is blind to what is happening inside an application.
By being within the application itself, Contrast agents have the context necessary to understand if an attack is happening and defend the application with a high degree of accuracy. For example, in the case of Cross-site Scripting (XSS), Contrast monitors both the request and response prior to deciding if an activity is indeed an attack, and then takes the corresponding action. This same principle, drawing the necessary information to make a highly accurate decision, drives the definition of all Contrast Protect defenses.
Operating from within, Contrast Protect moves and scales with the application and provides accurate attack visibility and protection because it is fully aware of how the application is operating.
More and more organizations are moving applications to the cloud for cost and scale benefits and, as they do, traditional network security approaches no longer apply. For example, appliance-based WAF network security solutions don’t translate directly to cloud environments, requiring businesses to adopt a patchwork approach – with different WAF solutions in different environments.
Contrast Protect uses patented deep security instrumentation to become part of the application. It moves seamlessly with the application, whether on premises, in the cloud, or a hybrid of the two. Contrast Protect also scales elastically, as the application grows or shrinks. Contrast instrumentation enables applications to defend themselves against attacks in real-time, all the time.
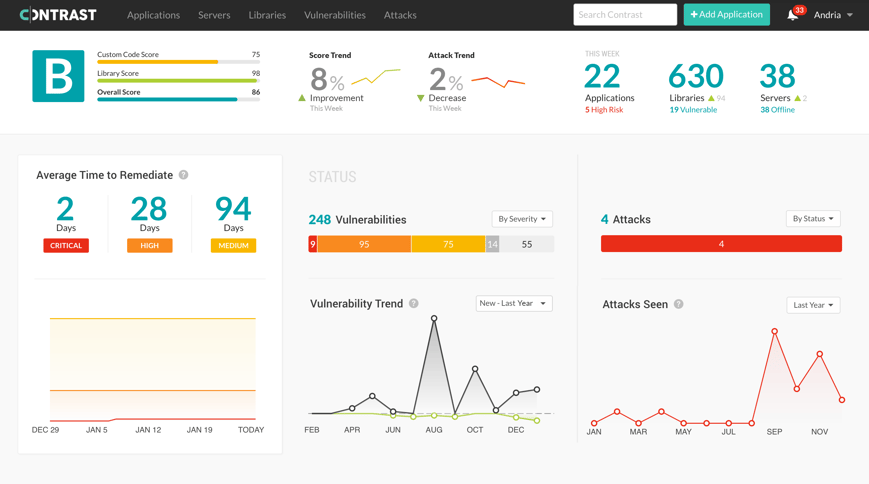
FIGURE 1. The Contrast Dashboard shows your application security environment in real time. This application is under attack and it has some critical vulnerabilities as well.
Always There, Always Working. Contrast Protect Highlights:
All WAF network security solutions require network re-configuration, and all require tuning as they attempt to “learn” the applications they are protecting.
Unlike WAF solutions, Contrast Protect requires no network changes or re-configuration, and no coordination with network teams. Because Contrast Protect works from within the application, it is indifferent to network configuration, protocols, encryption or encoding.
Contrast Protect doesn’t need to learn applications either – instead it becomes part of them, so there is no “learning mode.” Contrast rules work right-of-the-box with no tuning required to work properly. WAF solutions need to learn, because they are building ever-more complex models based on network traffic. That’s not necessary with Contrast Protect, because it sees what’s going on inside the application, where it doesn’t have to build a model or guess.
It’s time… Ditch that WAF
Legacy solutions have attempted to block attacks in the network, without any knowledge about the very applications they are protecting. Contrast Protect is different. Contrast enables applications to protect themselves against attacks based on a rich set of accurate application and security context.
It’s time… See how Contrast Protect stacks up against a WAF
The new era of self-protecting software has arrived. Click here to sign-up for a demo or peruse the Resources section to learn more. You can also give sales a jingle by dialing 888.371.1333.
Get the latest content from Contrast directly to your mailbox. By subscribing, you will stay up to date with all the latest and greatest from Contrast.